Question # 4
What is the sequence of messages that must be exchanged between a DHCP client and a server for the client to receive an IP address?
Question # 5
On the Nokia 7750 SR, which key displays all command options and their descriptions?
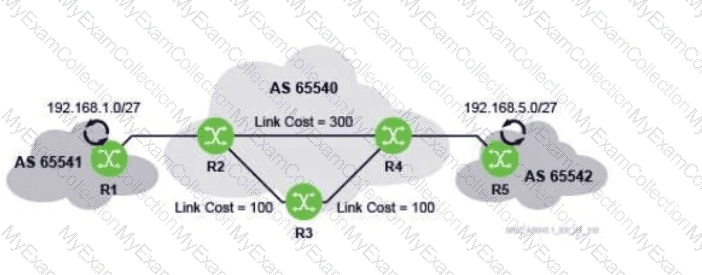
Question # 7
Which of the following routing protocols cannot be used between routers R2 and R4?
Question # 8
Which of the MPLS routers is responsible for pushing new labels for LSP A and LSP B?

Question # 11
Which of the following enables service providers to support multiple customers with the same VLAN ID over the same backbone?
Question # 12
Which configuration edit mode allows only one user to modify the global candidate configuration?

