Refer to the exhibit.
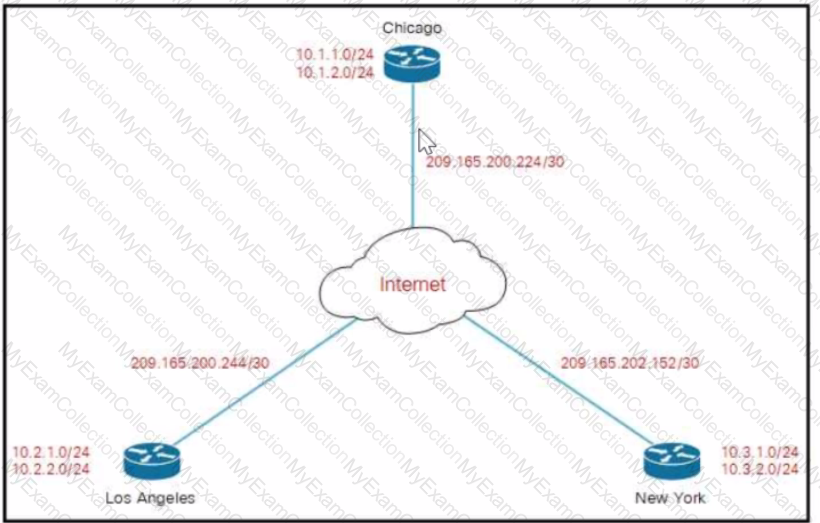
Company XYZ must design a DMVPN tunnel between the three sites Chicago is going to act as the NHS and the company wants DMVPN to detect peer endpoint failures Which technology should be used m the design?
Refer to the exhibit.
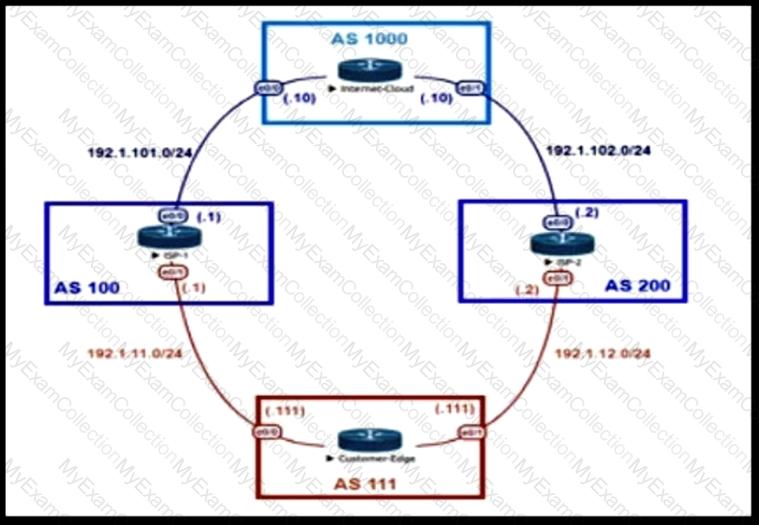
An engineer is designing the traffic flow for AS 111. Traffic from AS 111 should be preferred via AS 100 for all external routes. A method must be used that only affects AS 111. Which BGP attributes are best suited to control outbound traffic?
Refer to the exhibit.
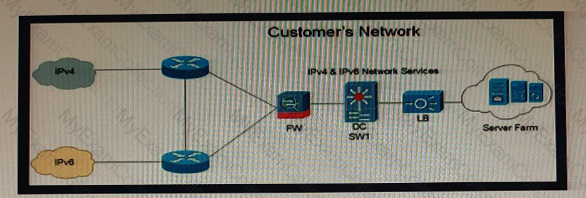
Company XYZ is currently running IPv4 but has decided to start the transition into IPv6. The initial objective is to allow communication based on IPv6 wherever possible, and there should still be support in place for devices that only support IPv4. These devices must be able to communicate to IPv6 devices as well. Which solution must be part of the design?
A service provider recently migrated to an SD-WAN solution for delivering WAN connections to its customers. One of the main challenges with the SD-WAN deployment is that branch site volume increases every year, which causes management complexity. Which action resolves the issue?
Company XYZ is planning to deploy primary and secondary (disaster recovery) data center sites. Each of these sites will have redundant SAN fabrics and data protection is expected between the data center sites. The sites are 100 miles (160 km) apart and target RPO/RTO are 3 hrs and 24 hrs, respectively. Which two considerations must Company XYZ bear in mind when deploying replication in their scenario? (Choose two.)
The SD-WAN architecture is composed of separate orchestration management, control, and data planes Which activity happens at the orchestration plane?
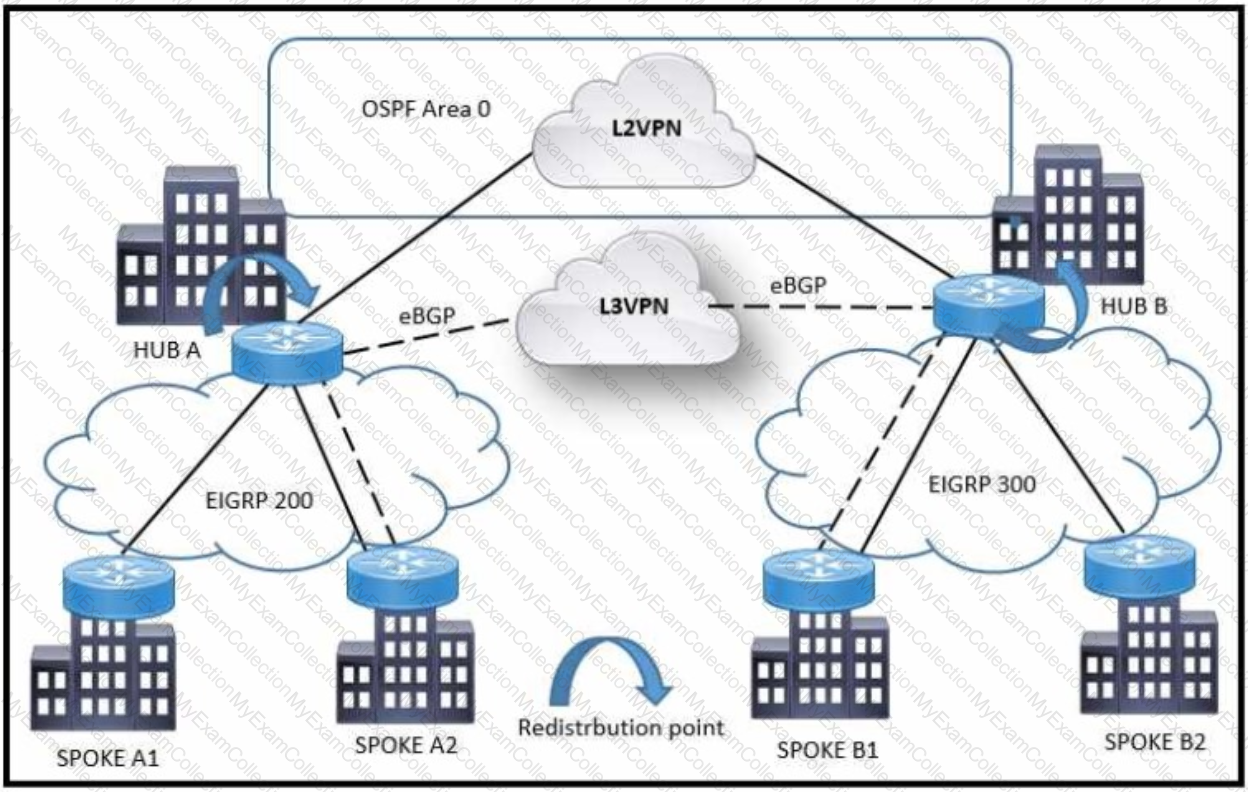
Refer to the exhibit A customer network design team is planning a migration from a legacy TDM-based L2VPN to an MPLS-based L3VPN Migration is planned in a phased approach:
•OSPF backbone Link between HUB A and HUB B sites to be migrated to eBGP
•Spoke A2 and Spoke B1 will be migrated to the L3VPN
Which solution design can be considered to avoid routing loops during backbone link migration?
The Agile release train workflow focuses on tasks which can be accomplished reliably and efficiently Scrum and Kanban are two of the most popular Agile frameworks, but both have a specific use case based on the implementation requirements In which two situations are Kanban the ideal framework to use� (Choose two.)
You are designing the routing design for two merging companies that have overlapping IP address space. Which of these must you consider when developing the routing and NAT design?
Refer to the exhibit.

As part of a redesign project, you must predict multicast behavior What happens to the multicast traffic received on the shared tree (*,G), if it is received on the LHR interface indicated*?
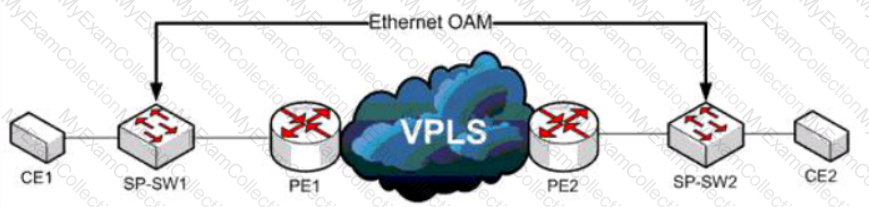
Refer to the exhibit A service provider has a requirement to use Ethernet OAM to detect end-to-end connectivity failures between SP-SW1 and SP- SW2 Which two ways to design this solution are true? (Choose two)
Which actions are performed at the distribution layer of the three-layer hierarchical network design model? (Choose two)
What are two advantages of controller-based networks versus traditional networks? (Choose two.)
A network architect must redesign a service provider edge, where multiservice and multitenant PEs are currently present. Which design feature should be minimized in the new design to achieve reliability?
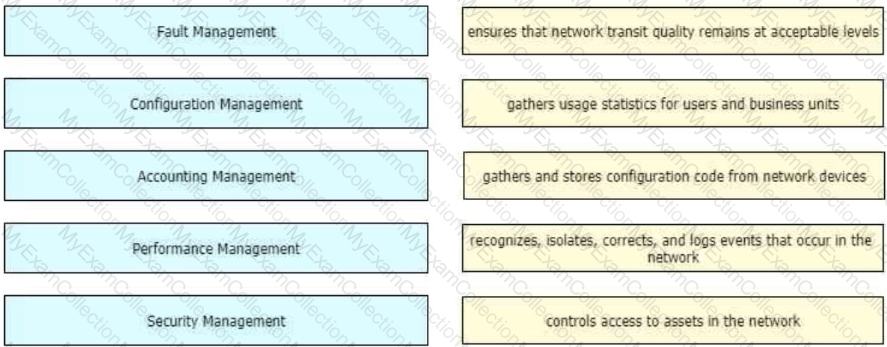
Company XYZ wants to use the FCAPS ISO standard for network management design. The focus of the design should be to minimize network outages by employing a set of procedures and activities to detect and isolate network issues and the appropriate corrective actions to overcome current issues and prevent them from occurring again. Which layer accomplishes this design requirement?
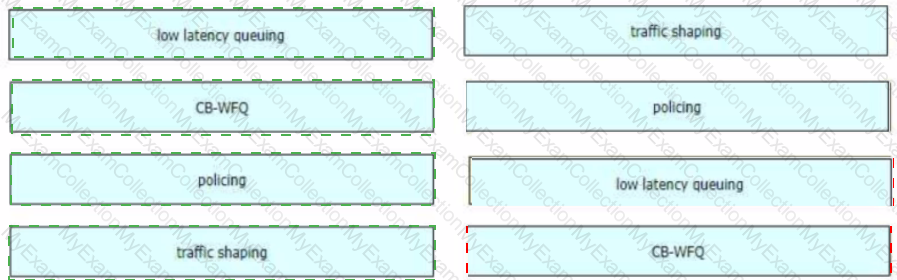
Drag and drop the QoS technologies from the left onto the correct capabilities on the right

Which project management methodology is characterized by a having a low client
involvement?
The major business applications of an enterprise are largely monolithic and hard-coded As part of a major modernization and overhaul of the applications the goal is to move to a modular and containerized application architecture mode At the same time decoupling from the hardware is desired to move to an on-demand provisioning However the CyberOps team mandated that the final architecture must provide the same security levels as an air-gapped data center. Which cloud architecture meets these requirements?
SDWAN networks capitalize the usage of broadband Internet links over traditional MPLS links to offer more cost benefits to enterprise customers. However, due to the insecure nature of the public Internet, it is mandatory to use encryption of traffic between any two SDWAN edge devices installed behind NAT gateways. Which overlay method can provide optimal transport over unreliable underlay networks that are behind NAT gateways?
Which two design option are available to dynamically discover the RP in an IPv6 multicast network? (Choose
two)
Which two benefits can software-defined networks provide to businesses? (Choose two.)
Refer to the exhibit.
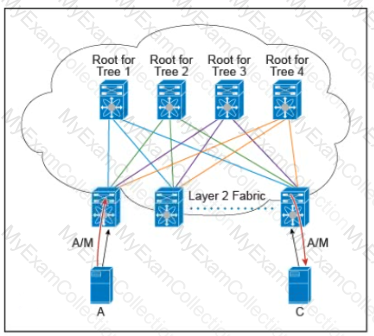
There are multiple trees in the Cisco FabricPath All switches in the Layer 2 fabric share the same view of each tree. Which two concepts describe how the multicast traffic is load-balanced across this topology? (Choose two )
In the wake of a security compromise incident where the internal networks were breached by an outside attacker at the perimeter of the infrastructure, an enterprise is now evaluating potential measures that can help protect against the same type of incident in the future. What are two design options that can be employed? (Choose two)
Refer to the exhibit.
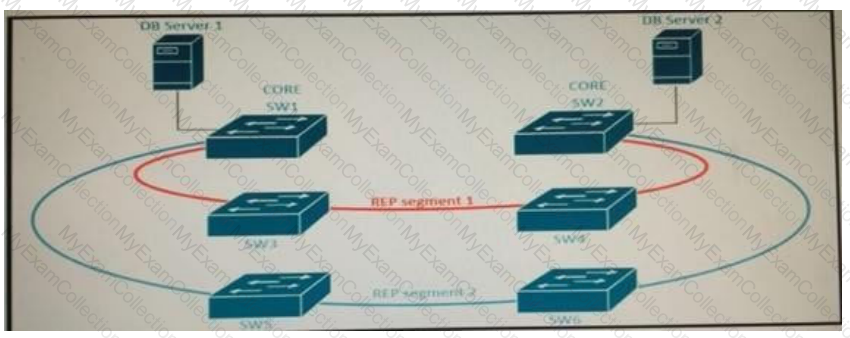
A new high availability DB sever cluster is installed in the network.
These two servers require high bandwidth and low latency Layer 2 connectivity for database replication.
Which solution supports these requirements?
Which optimal use of interface dampening on a fast convergence network design is true?
Company XYZ wants to deploy OSPF. The design plan requires that two OSPF networks be mutually redistributed at multiple locations and ensure end-to-end connectivity to all of the company's networks Which technology can be used to fulfill the requirements while avoiding the creation of routing loops?
A customer migrates from a traditional Layer 2 data center network into a new SDN-based spine-and-leaf VXLAN EVPN data center within the same location The networks are joined to enable host migration at Layer 2 What is the final migration step after hosts have physically migrated to have traffic flowing through the new network without changing any host configuration?
Company XYZ needs advice in redesigning their legacy Layer 2 infrastructure. Which technology should be included in the design to minimize or avoid convergence delays due to STP or FHRP and provide a loop-free topology?
What advantage of placing the IS-IS layer 2 flooding domain boundary at the core Layer in a three-layer hierarchical network is true?
Which two application requirements are mandatory tor traffic to receive proper treatment when placed in the priority queue? (Choose two.)
What is an architectural framework created by ETSI that defines standards to decouple network functions from proprietary hardware-based appliances and have them run in software on standard x86 servers?
Which feature must be part of the network design to wait a predetermined amount of time before notifying the routing protocol of a change in the path in the network?
Drag and drop the FCAPS network management reference models from the left onto the correct definitions on the right.
Software-defined networking architecture is used for cost-effective, adaptable, and easily manageable applications. In which two software-defined networks is SDN commonly used? (Choose two.)
A European government passport agency considers upgrading its IT systems to increase performance and workload flexibility in response to constantly changing requirements. The budget manager wants to reduce capital expenses and IT staff and must adopt the lowest-cost technology. Which technology choice is suitable?
Which technology is an open-source infrastructure automation tool that automates repetitive tasks for users who work in networks such as cloud provisioning and intraservice orchestration?
Which two types of planning approaches are used to develop business-driven network designs and to facilitate the design decisions? (Choose two)
Company XYZ wants to use the FCAPS ISO standard for network management design. The focus of the design should be to monitor and keep track of any performance issues by continuously collecting and analyzing statistical information to monitor, correct, and optimize any reduced responsiveness across the network. Which layer accomplishes this design requirement?
A software-defined network can be defined as a network with an API that allows applications to understand and react to the state of the network in near real time. A vendor is building an SDN solution that exposes an API to the RIB and potentially the forwarding engine directly. The solution provides off-box processes with the capability to interact with the routing table in the same way as a distributed routing process. Which SDN framework model does the solution use?
Refer to the exhibit.
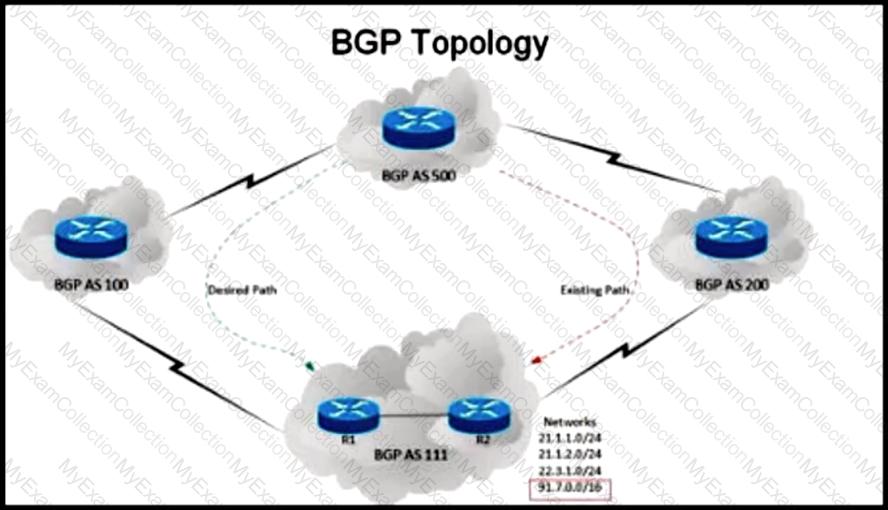
An engineer has been asked to redesign the traffic flow toward AS 111 coming from AS 500.Traffic destined to AS 111 network 91 7 0.0/16 should come in via AS 100. while traffic destined to all other networks in AS 111 should continue to use the existing path Which BGP attributes are best suited to control this inbound traffic coming from BGP AS 500 Into the 91.7.0.0/16 network?
Refer to the exhibit.
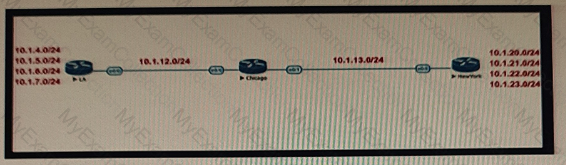
Company XYZ BGP topology is as shown in the diagram. The interface on the LA router connected toward the 10 1.5.0/24 network is faulty and is going up and down, which affects the entire routing domain. Which routing technique can the network administrator use so that the rest of the network is not affected by the flapping issue?
A network uses an SDN architecture with switches and a centralized controller What should be on the switches but not on the controller?
Which tool automates network implementation activities and shortens the implementation lifecycle?
What are two top cloud-native security challenges faced by today's cloud-oriented organizations? (Choose two.)
Which two statements describe the functionality of OSPF packet-pacing timers? (Choose two )
The group-pacing timer controls the interval that is used for group and individual LSA refreshment
The controller has a global view of the network, and it can easily ensure that the network is in a consistent and optimal configuration. Which two statements describe a centralized SDN control path? (Choose two.)
Which mechanism enables small, unmanaged switches to plug into ports of access switches without risking switch loops?
Which two benefits can software defined networks provide to businesses? (Choose two.)
A large enterprise customer is planning a new WAN connection to its headquarters. The current architecture is
dual homed with static routing, but users complain when a specific link fails. Failure of the other link does not
affect any services or applications. The new WAN connection must provide the headquarters with a resilient
network design and increase the return on investment.
Which solution should be recommended to the customer?
When planning their cloud migration journey what is crucial for virtually all organizations to perform?
Two enterprise networks must be connected together. Both networks are using the same private IP addresses.
The client requests from both sides should be translated using hide NAT (dynamic NAT) with the overload
feature to save IF addresses from the NAT pools. Which design addresses this requirement using only one
Cisco I OS NAT router for both directions?
A banking customer determines that it is operating POS and POI terminals that are noncompliant with PCI DSS requirements, as it is running TLSv1.0. The customer plans to migrate the terminals to TLSv1.2. What are two requirements to complete the migration? (Choose two.)
A large enterprise cloud design team is evaluating different cloud consumption models. What is an example of typical PaaS limitations or concerns that should be considered during service design?
Which three items do you recommend for control plane hardening of an infrastructure device? (Choose three.)
The Company XYZ network requires OSPF dead neighbor detection in a subsecond manner However the company network does not support BFD Which other feature can be used to fulfill the design requirement?
Refer to the exhibit.
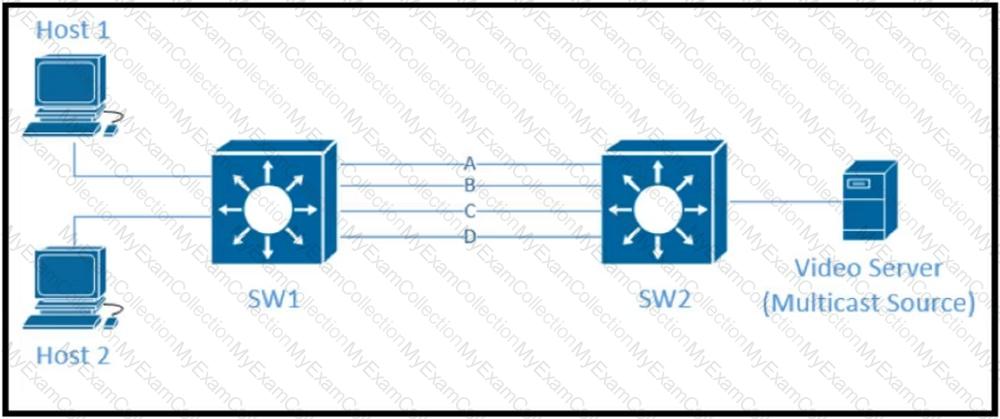
Traffic was equally balanced between Layer 3 links on core switches SW1 and SW2 before an introduction of the new video server in the network. This video server uses multicast to send video streams to hosts and now one of the links between core switches is over utilized Which design solution solves this issue?
Which interface between the controller and the networking device enables the two to communicate and allows the controller to program the data plane forwarding tables of the networking device?
When designing a WAN that will be carrying real-time traffic, what are two important reasons to consider serialization delay? (Choose two )
Which two statements explain the operation of BFD asynchronous mode? (Choose two )
Company XYZ asks for design recommendations for Layer 2 redundancy. The company wants to prioritize fast convergence and resiliency elements. In the design. Which two technologies are recommended? (Choose two.)
As a service provider is implementing Strong Access Control Measures, which two of the following PCI Data Security Standard requirements must be met’ (Choose two.)
A customer has a functional requirement that states HR systems within a data center should be segmented from other systems that reside in the same data center and same VLAN. The systems run legacy applications by using hard-coded IP addresses. Which segmentation method is suitable and scalable for the customer?
You want to add 900 VLANs to the existing 90 VLANs on a data center Which two spanning-tree concerns must you consider? (Choose two )
You want to split an Ethernet domain in two.
Which parameter must be unique in this design to keep the two domains separated?
For a company that offers online billing systems for their customers, which strategy ensures the RPO is kept as low as possible?
Which development model is closely associated with traditional project management?
Company XYZ wants to improve the security design of their network to include protection from reconnaissance and DoS attacks on their sub interfaces destined toward next hop routers. Which technology can be used to prevent these types of attacks?
What are two key design principles when using a hierarchical core-distribution-access network model? (Choose two )
A healthcare provider discovers that protected health information of patients was altered without patient consent. The healthcare provider is subject to HIPAA compliance and is required to protect PHI data. Which type of security safeguard should be implemented to resolve this issue?
Refer to the exhibit.
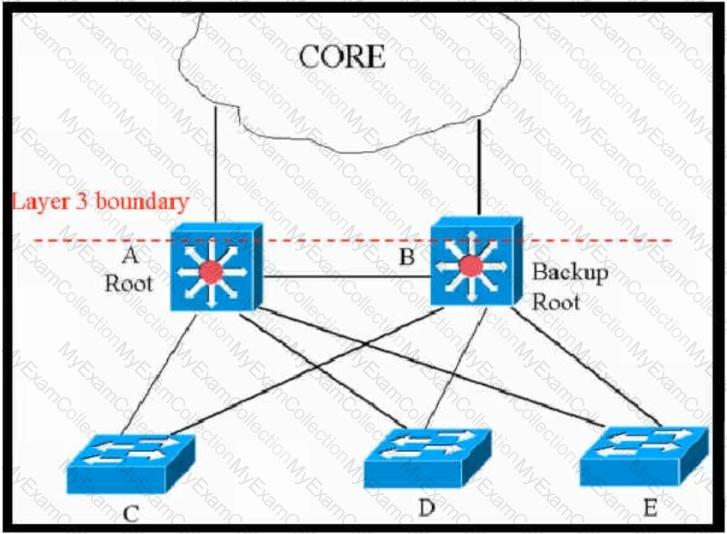
This network is running legacy STP 802.1 d. Assuming "hello_timer" is fixed to 2 seconds, which parameters can be modified to speed up convergence times after single link/node failure?
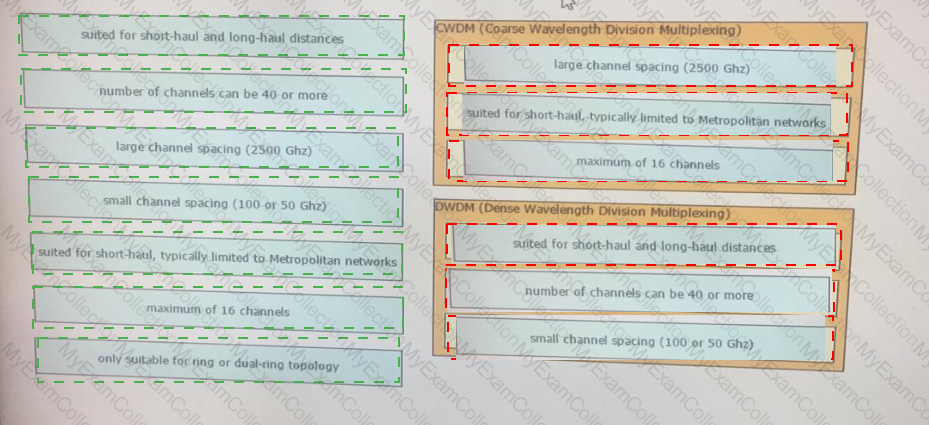
Which two advantages of using DWDM over traditional optical networks are true? (Choose two.)
An architect receives a functional requirement for a NAC system from a customer security policy stating that if a corporate Wi-Fi device does not meet current AV definitions, then it cannot access the corporate network until the definitions are updated. Which component should be built into the NAC design?
An architect receives a business requirement from a CTO that states the RTO and RPO for a new system should be as close as possible to zero. Which replication method and data center technology should be used?
Refer to the exhibit.
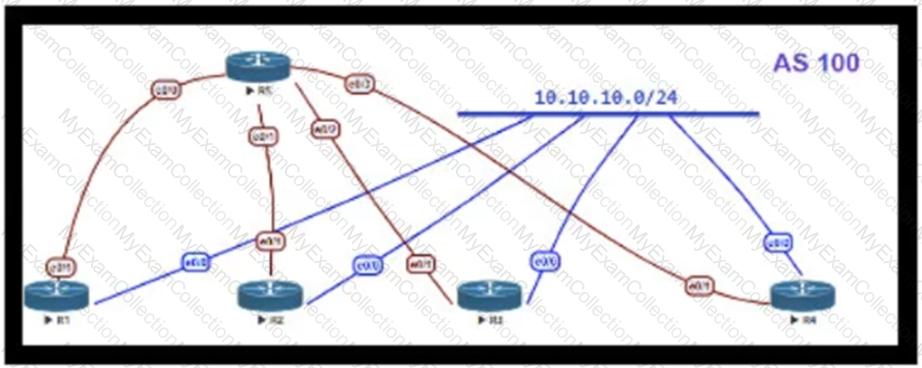
OSPF is running as the IGP to provide reachability to all AS100 networks R3 and R4 are the current ABRs at the boundary of OSPF Area0 and Areal Now BGP must be deployed within AS 100 because it will be receiving Internet routes from its eBGP peers (the service provider) connected to R1 and R2 What is an optimal solution for this deployment to configure BGP relationships and redistribute BGP learned routes into OSPF?
Which two actions must merchants do to be compliant with the Payment Card Industry Data Security Standard? (Choose two.)
Which methodology is the leading lifecycle approach to network design and implementation?
A product manufacturing organization is integrating cloud services into their IT solution The IT team is working on the preparation phase of the implementation approach, which includes the Define Strategy step. This step defines the scope of IT, the application, and the service What is one topic that should be considered in the Define Strategy step?
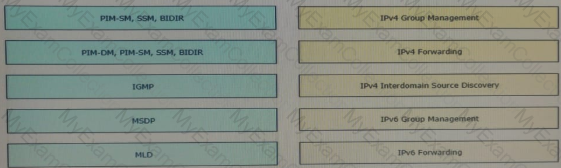
Drag and drop the multicast protocols from the left onto the current design situation on the right.
The Agile Manifesto is a document that defines the key values and principles behind the Agile philosophy and helps development teams work more efficiently and sustainably Each of the four key values is split into two sections a left-hand side and a right-hand side In other words, though there is value in the items on the right we value the items on the left more What is one of the key values of the Agile Manifesto?
You were tasked to enhance the security of a network with these characteristics:
• A pool of servers is accessed by numerous data centers and remote sites
• The servers are accessed via a cluster of firewalls
• The firewalls are configured properly and are not dropping traffic
• The firewalls occasionally cause asymmetric routing of traffic within the server data center.
Which technology should you recommend to enhance security by limiting traffic that could originate from a hacker compromising a workstation and redirecting flows at the servers?
Which issue poses a challenge for security architects who want end-to-end visibility of their networks?
Which two features describe controller-based networking solutions compared to traditional networking solutions? (Choose two.)
You have been tasked with designing a data center interconnect to provide business continuity You want to encrypt the traffic over the DCI using IEEE 802 1AE MACsec to prevent the deployment of any firewall or IPS. Which two interconnect technologies support MACsec? (Choose two.)
As more links are added to the network, information and attributes related to the link is added to the control plane meaning every link that gets added will slow down the convergence of the control plane by some measurable amount of time. As a result when additional redundancy is built or added the MTTR will increase too Which risk increases along with the increased MTTR?
An enterprise has identified these causes for inefficient CAPEX spending:
CAPEX planning is driven by technology and not by business objectives.
The CAPEX planning team lacks the data it needs to perform due diligence tasks.
The organizational structure lacks sufficient accountability and incentives.
Which corporate cultural change contributes to improving the effectiveness of CAPEX spending?
Refer to the exhibit.
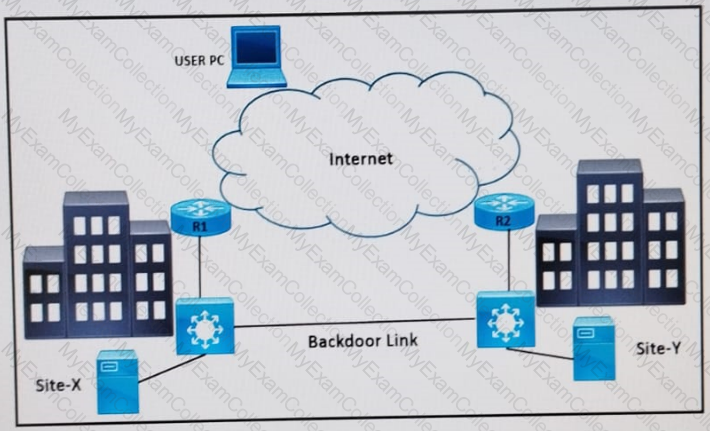
Two data center siles X and Y are connected with a direct backdoor link with these conditions •Site-specific firewalls are deployed behind the Internet edge routers R1 and R2 •Both sites are advertising the address pool 100 75 10 0/23 toward the internet Site-X finds that Internet traffic returning from user PCs comes back on the Site-Y link Which design resolves the issue?
Refer to the exhibit.
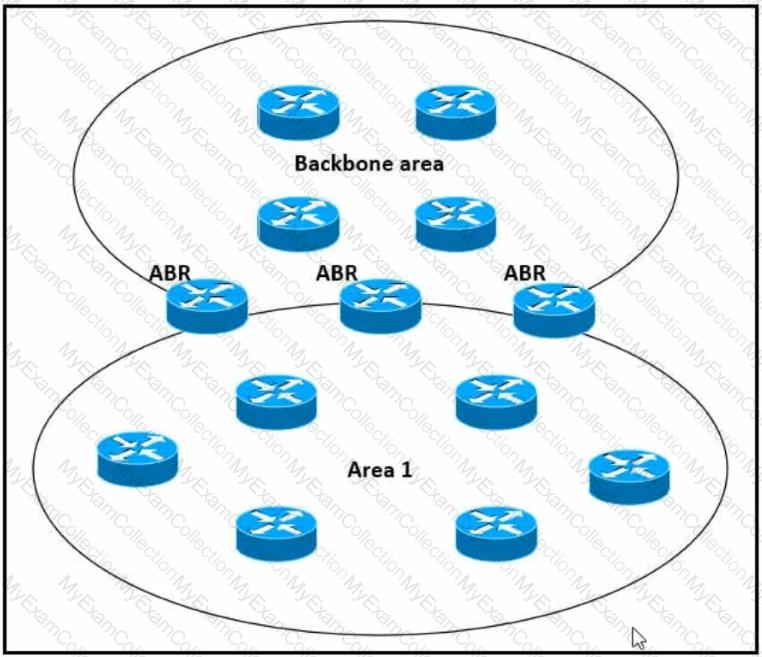
Which impact of using three or more ABRs between the backbone area and area 1 is true?
The network designer needs to use GLOP IP address in order make them unique within their ASN, which
multicast address range will be considered?
Refer to the table.
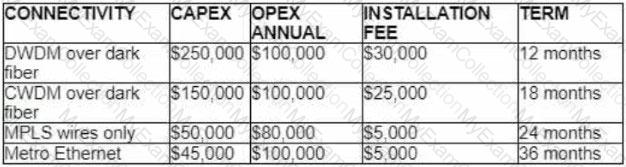
A customer investigates connectivity options for a DCI between two production data centers to aid a large-scale migration project. The solution must provide a single 10G connection between locations and be able to run its own varying QoS profiles without service provider interaction based on the migration stages. All connectivity methods are at 10 Gbps. Which transport technology costs the least if the connectivity is required for just one year?
As part of workspace digitization, a large enterprise has migrated all their users to Desktop as a Sen/ice (DaaS), by hosting the backend system in their on-premises data center. Some of the branches have started to experience disconnections to the DaaS at periodic intervals, however, local users in the data center and head office do not experience this behavior. Which technology can be used to mitigate this issue?
A network attacker exploits application flaws to compromise critical systems in the organization with these objectives:
• Obtain sensitive data and export the data out of the network.
• Compromise developer and administrator credentials to potentially
What is the next step after application discovery is completed in Zero Trust networkings
Which two factors must be considered for high availability in campus LAN designs to mitigate concerns about unavailability of network resources? (Choose two.)
Drag and drop the optical technology design characteristics on the left to the correct optical technologies on the right. Not all options are used
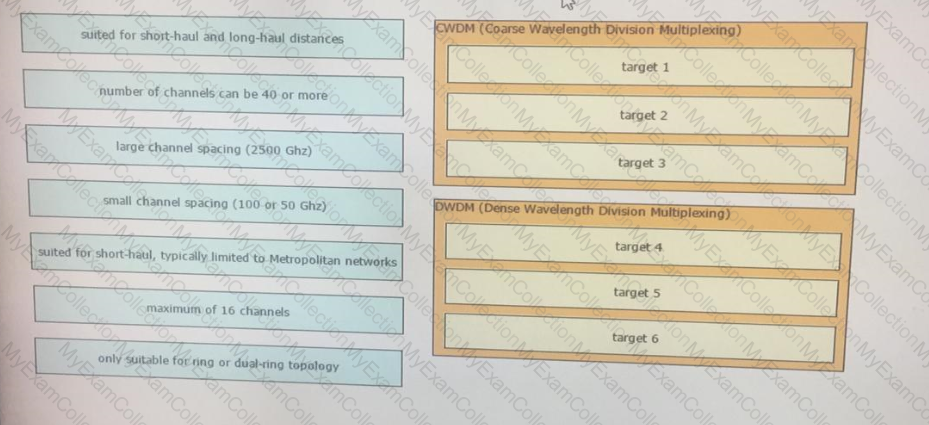
Company XYZ is designing the IS-IS deployment strategy for their multiarea IS-IS domain. They want IS-IS neighbour relationships to be minimized on each network segment and want to optimize the size of the IS-IS LSDB on each router. Which can design can be used to meet these requirements?
Two routers R1 and R2 are directly connected through an Ethernet link Both routers are running OSPF. OSPF has been registered with BFD and BFD is running in asynchronous mode with the echo function enabled Which two actions occur that are related to the echo function? (Choose two)
Two routers R1 and R2 are directly connected through an Ethernet link. Both routers are running OSPF over the Ethernet link and OSPF has been registered with BFD. R1 has been set up to transmit BFD at a 50 ms interval, but R2 can receive only at a 100 ms rate due to platform limitations. What does this mean?
You are designing a new Ethernet-based metro-area network for an enterprise customer to connect 50 sites within the same city OSPF will be the routing protocol used. The customer is primarily concerned with IPv4 address conservation and convergence time. Which two combined actions do you recommend? (Choose two)
Which two pain points are the most common for container technology adoption? (Choose two)
A healthcare customer requested that SNMP traps must be sent over the MPLS Layer 3 VPN service. Which protocol must be enabled?
Refer to the exhibit.
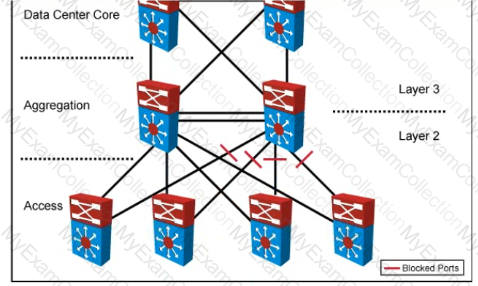
Your company designed a network to allow server VLANs to span all access switches in a data center In the design, Layer 3 VLAN interfaces and HSRP are configured on the aggregation switches Which two features improve STP stability within the network design? (Choose two.)
A legacy enterprise is using a Service Provider MPLS network to connect its head office and branches. Recently, they added a new branch to their network. Due to physical security concerns, they want to extend their existing IP CCTV network of the head office to the new branch, without any routing changes in the network. They are also under some time constraints. What is the best approach to extend the existing IP CCTV network to the new branch, without incurring any IP address changes?
Company XYZ has 30 sites using MPLS L3 VPN and the company is now concerned about data integrity. The company wants to redesign the security aspect of their network based on these requirements:
• Securely transfer the corporate data over the private WAN
• Use a centralized configuration model.
• Minimize overhead on the tunneled traffic.
Which technology can be used in the new design to meet the company's requirements?
An international media provider is an early adopter of Docker and micro services and is using an open-source homegrown container orchestration system. A few years ago, they migrated from on-premises data centers to the cloud Now they are faced with challenges related to management of the deployed services with their current homegrown orchestration system.
Which platform is well-suited as a state-aware orchestration system?
A multicast network is sing Bidirectional PIM. Which two combined actions achieve high availability so that two RPs within the same network can act in a redundant manner? (Choose two)
Company XYZ has multiple production units and marketing departments across the region The current network is a mixture of point-to-point links and MPLS Layer 3 VPN service from the provider. The Info-Sec team has suggested to isolate production traffic end-to-end with an encryption over the transport network to comply with the HIPAA standard Which solution must be used in their design if Company XYZ wants a quick roll out�


 A picture containing table
Description automatically generated
A picture containing table
Description automatically generated