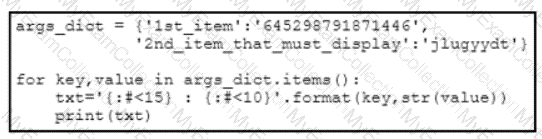
A script contains the statement white loop != 999 ’ Which value terminates the loop?
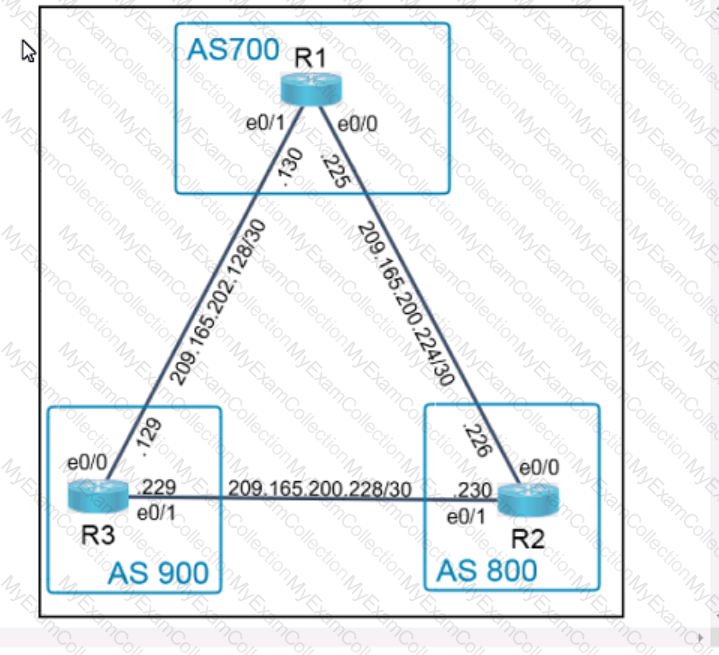
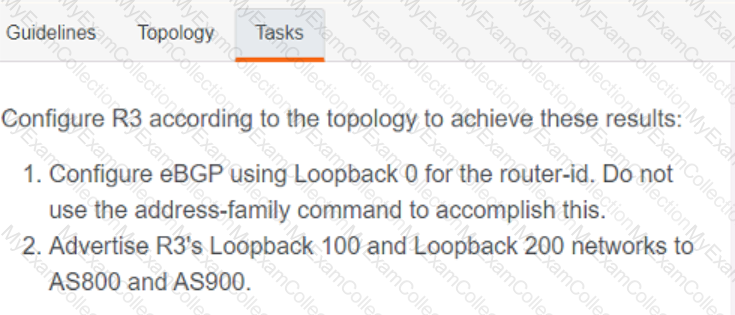
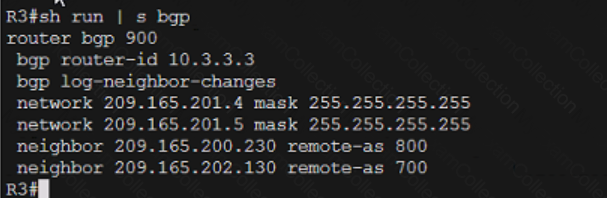
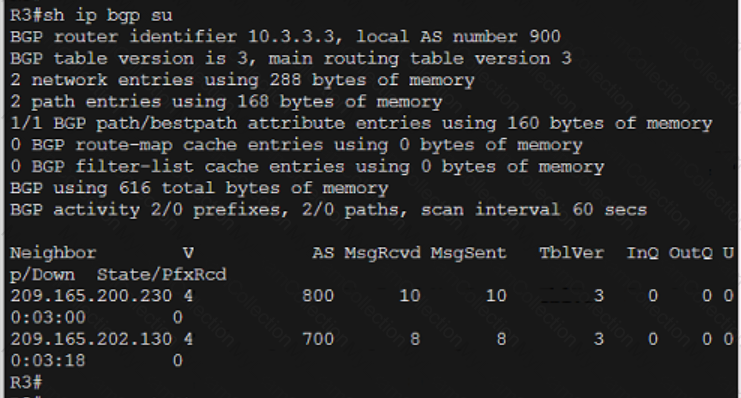
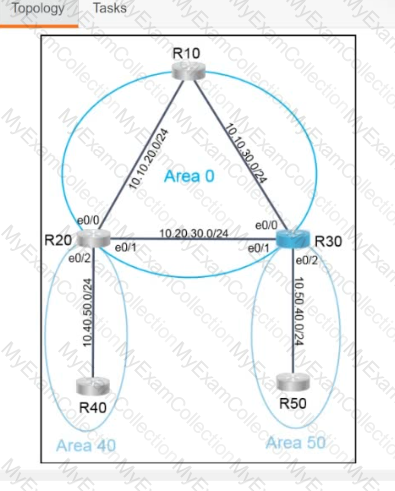
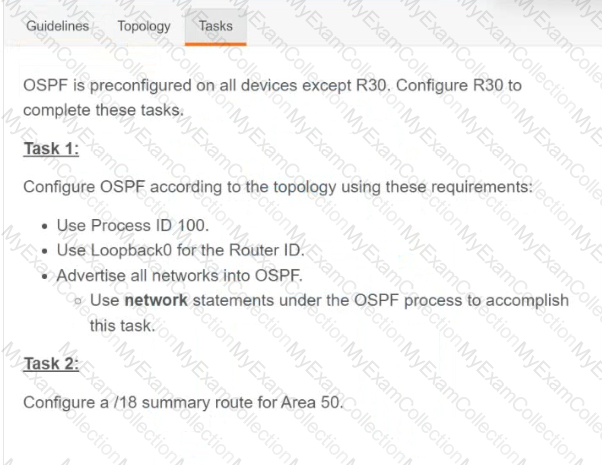
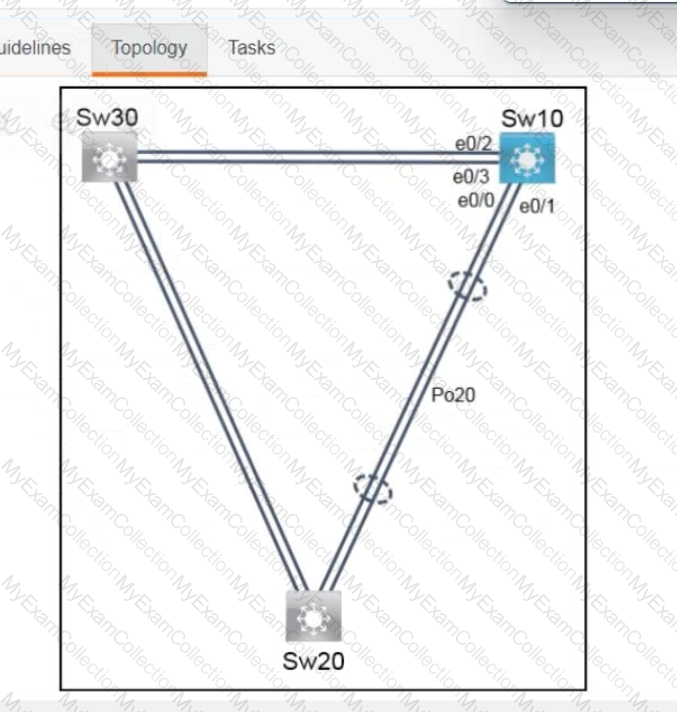
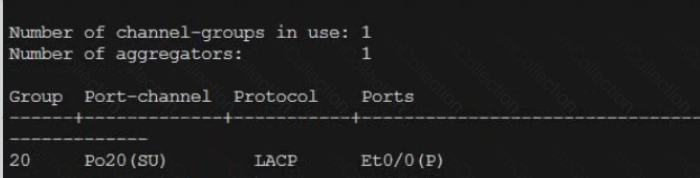
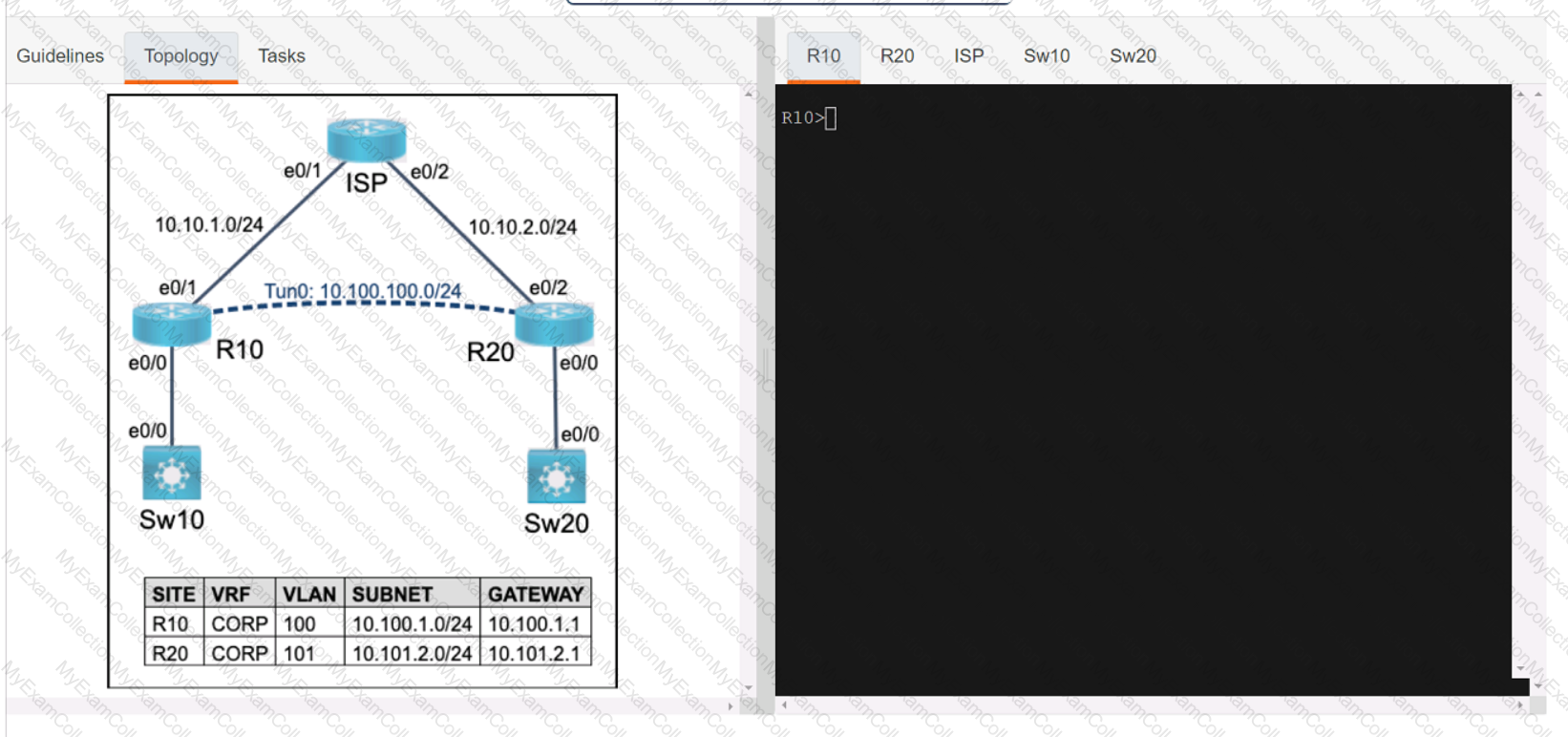
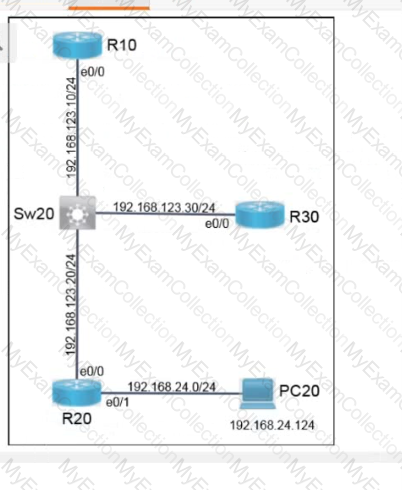
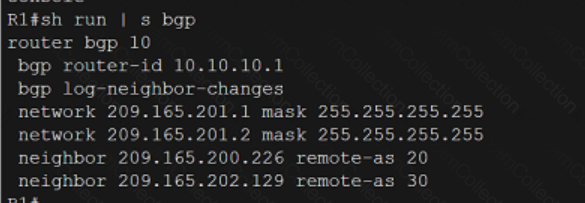
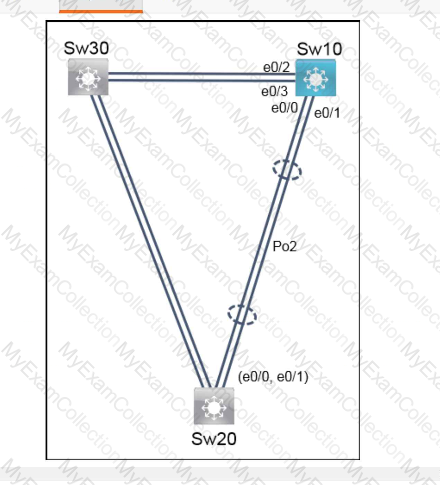
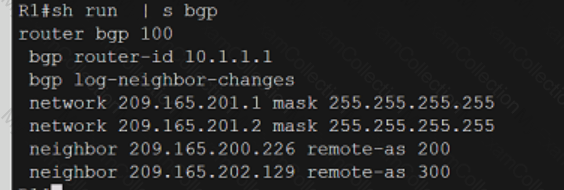
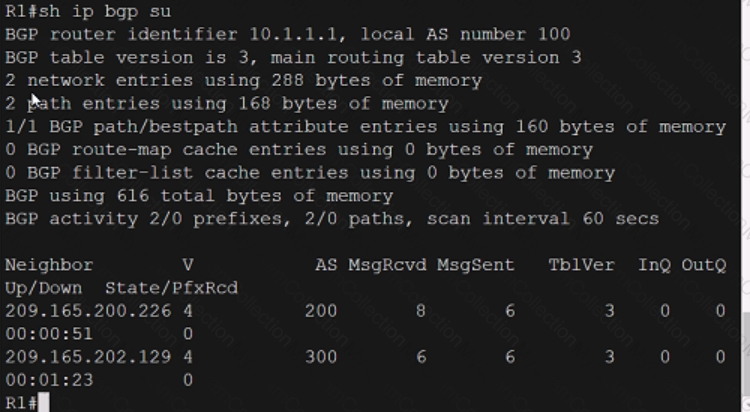
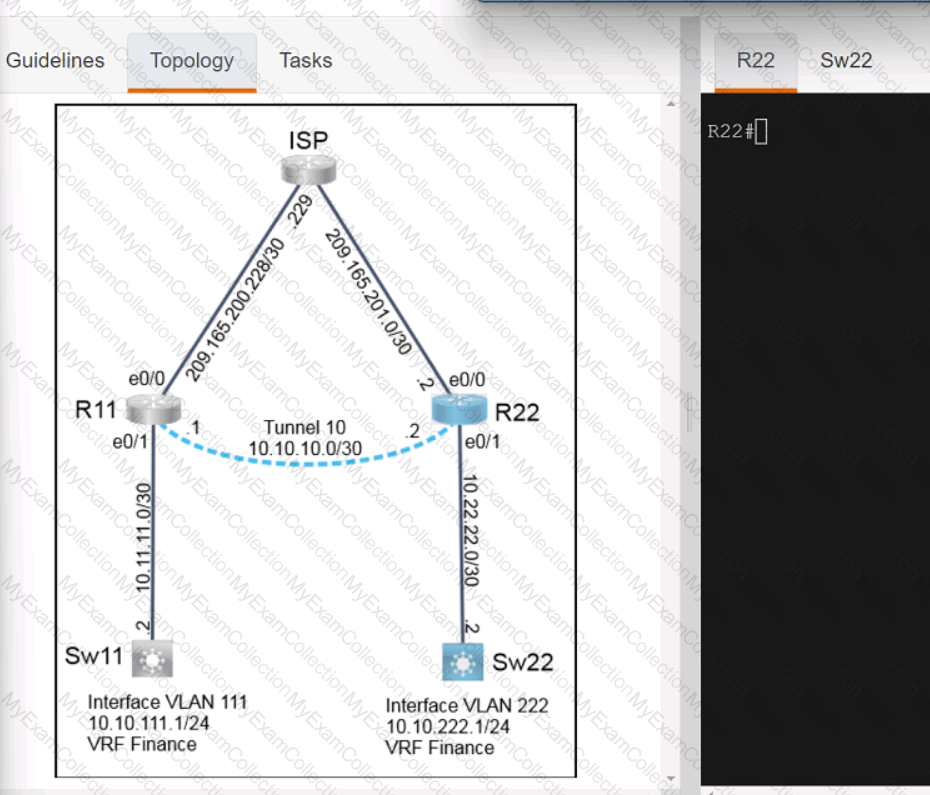
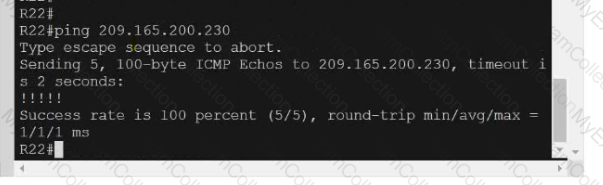
Refer to the exhibit.

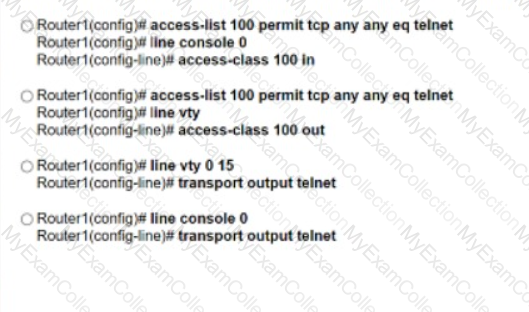
An engineer attempts to connect to another device from Route1’s console port. Which configuration is needed to allow telnet connections?
In a wireless network environment, which measurement compares the received signal to the background noise?
Which AP mode allows administrators to generate pcap files to use for troubleshooting?
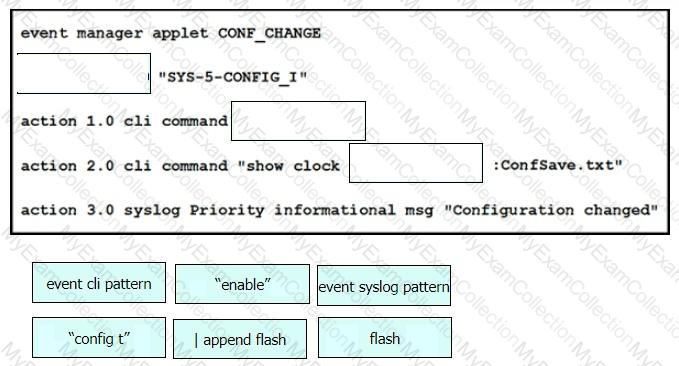
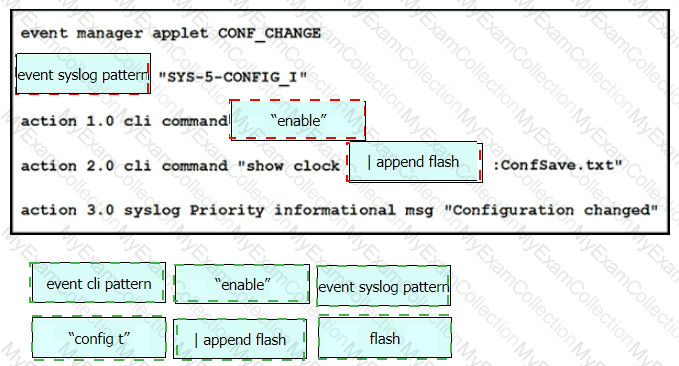
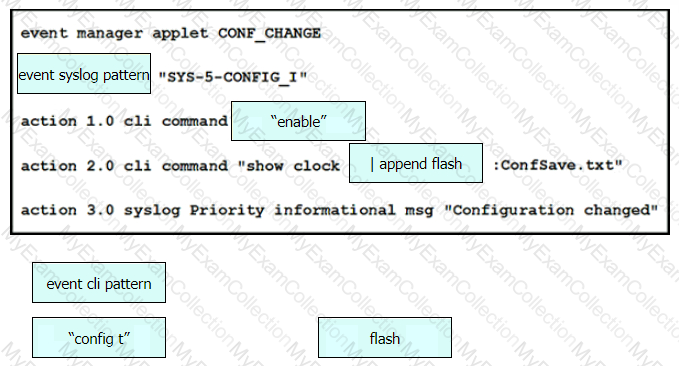
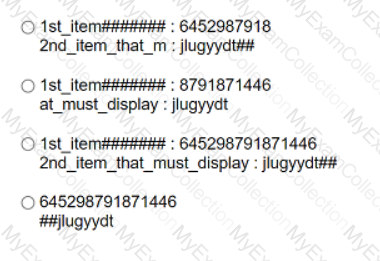
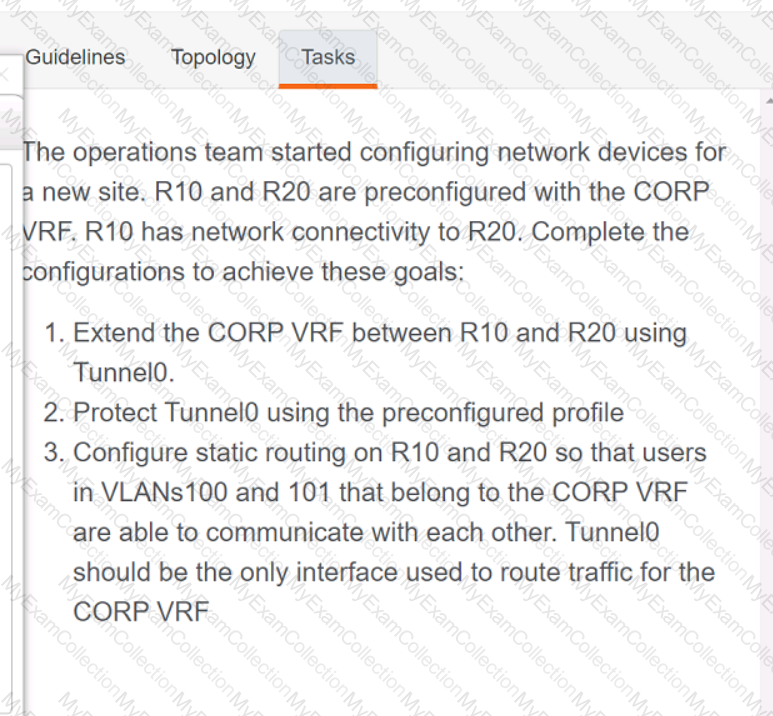
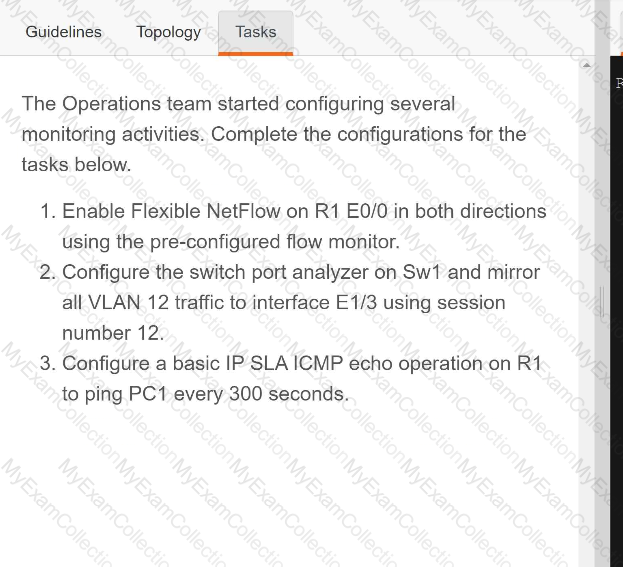
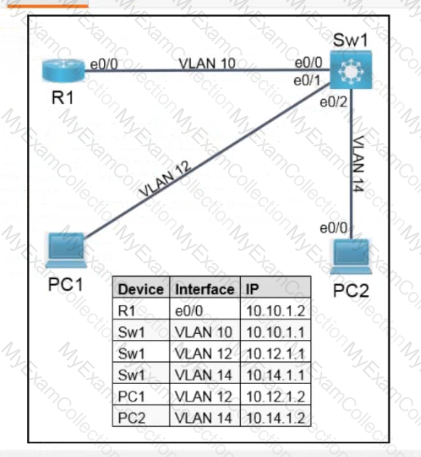
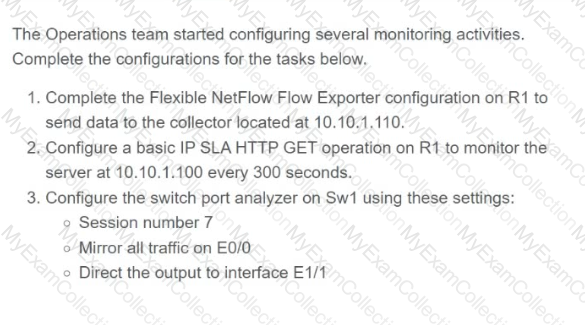
Drag and drop the snippets onto the blanks within the code to create an EEM script that adds an entry to a locally stored text file with a timestamp when a configuration change is made. Not all options are used.
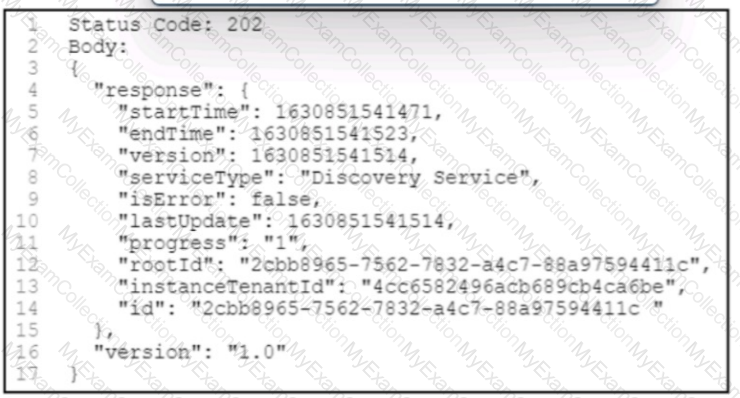
Refer to the exhibit. A POST /discovery request spawns an asynchronous task. After querying for more information about the task, the Cisco DNA Center platform returns the REST API response. What is the status of the discovery task?
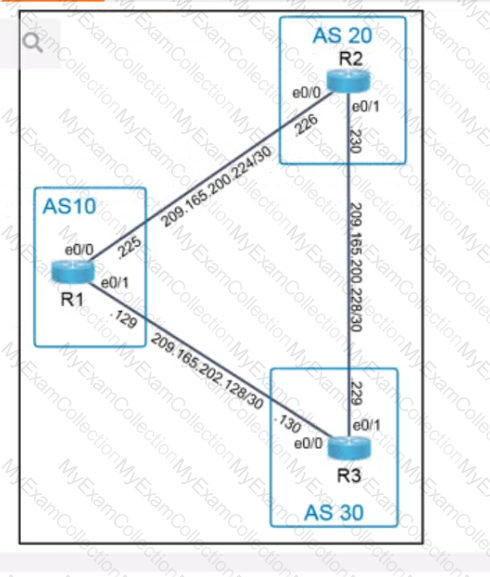
In a Cisco SD-WAN solution, which two functions are performed by OMP? (Choose two.)
What is used by vManage to interact with Cisco SD-WAN devices in the fabric?
In Cisco Catalyst Center (formerly DNA Center) Inventory, the Software Version of a network device displays a status of OUTDATED. What does It me?
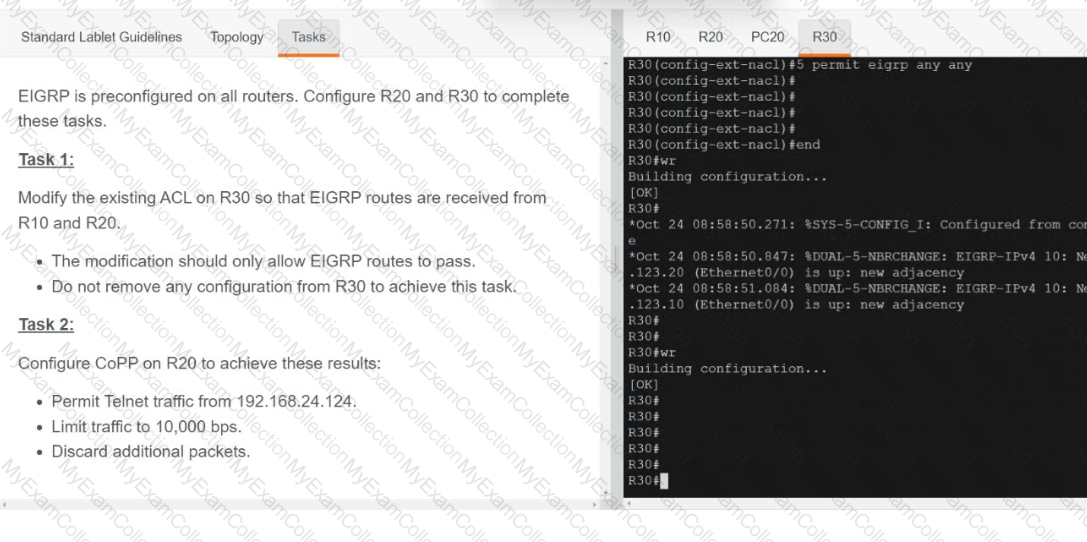
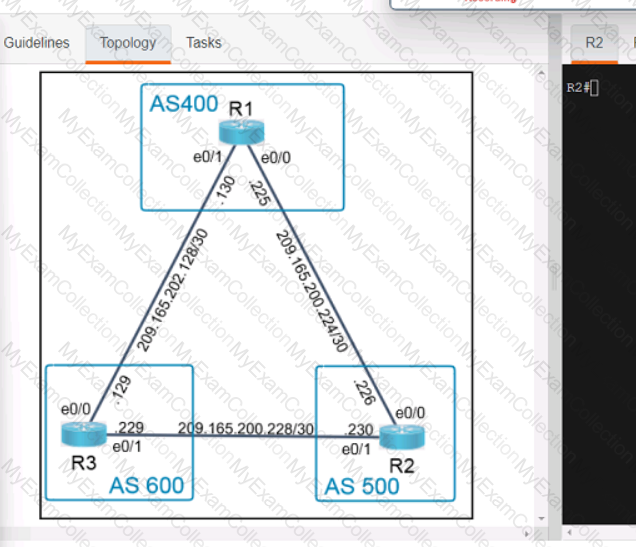
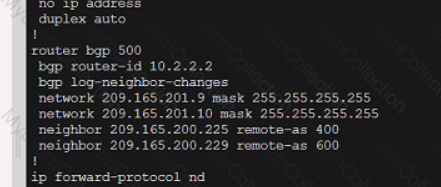
Refer to the exhibit.
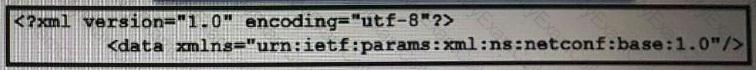
What does the error message relay to the administrator who is trying to configure a Cisco IOS device?
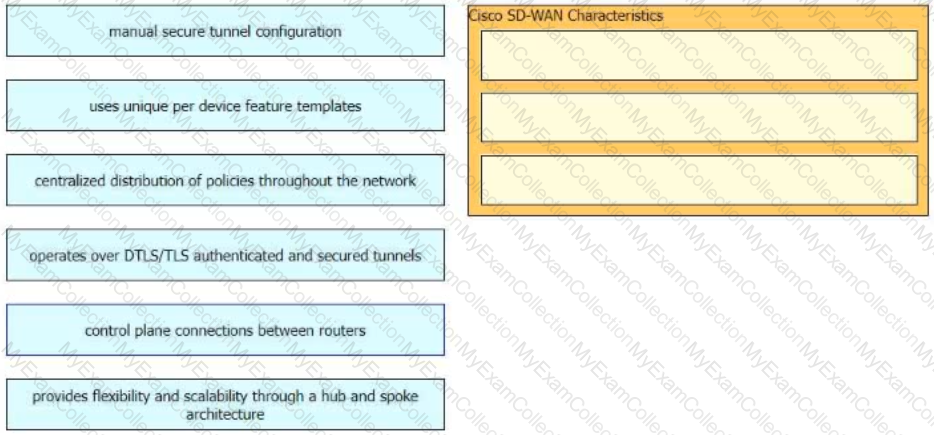
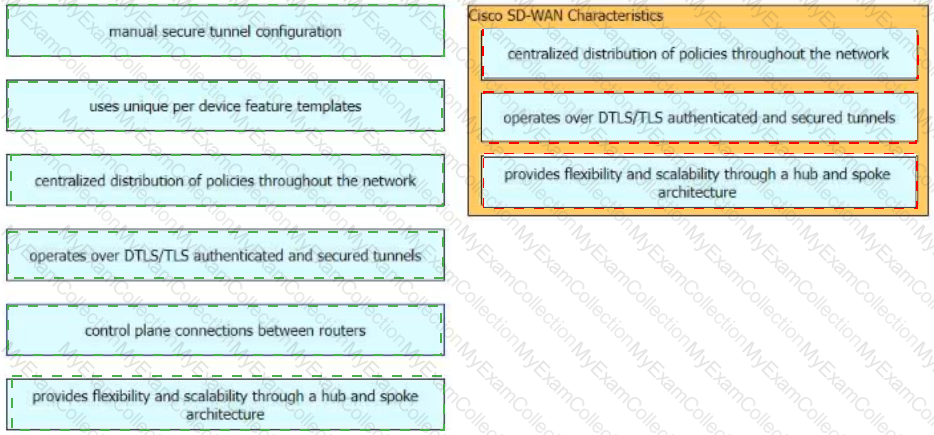
Drag and drop the characteristics of Cisco Catalyst SD-WAN from the left onto the right. Not all options are used.
Which lag/profile on a Cisco Catalyst 9800 Series WLC must be modified to allow Cisco ISE to dynamically assign VLANs to users on an 802.1X-based SSID?
Which two methods are used to assign security group tags to the user in a Cisco Trust Sec architecture? (Choose two.)
Which feature is available to clients using layer 2 roaming in a wireless infrastructure?
A customer requires their wireless data traffic to egress at the switch port of the access point. Which access point mode supports this?
A system must validate access rights to all its resources and must not rely on a cached permission matrix. If the access level to a given resource is revoked but is not reflected in the permission matrix, the security is violates Which term refers to this REST security design principle?
 A screenshot of a computer
Description automatically generated
A screenshot of a computer
Description automatically generated

 A screen shot of a computer
Description automatically generated
A screen shot of a computer
Description automatically generated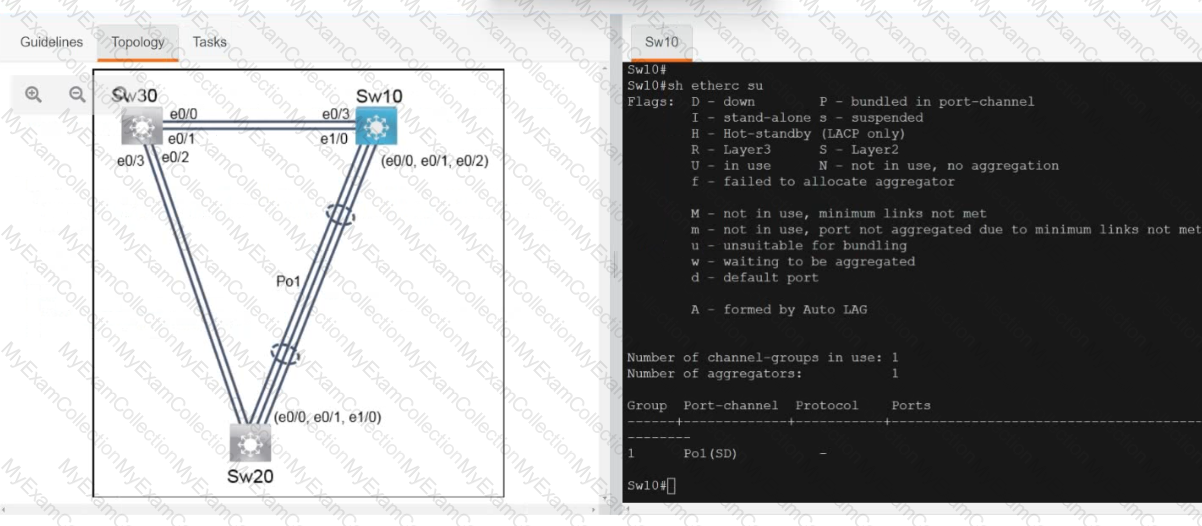
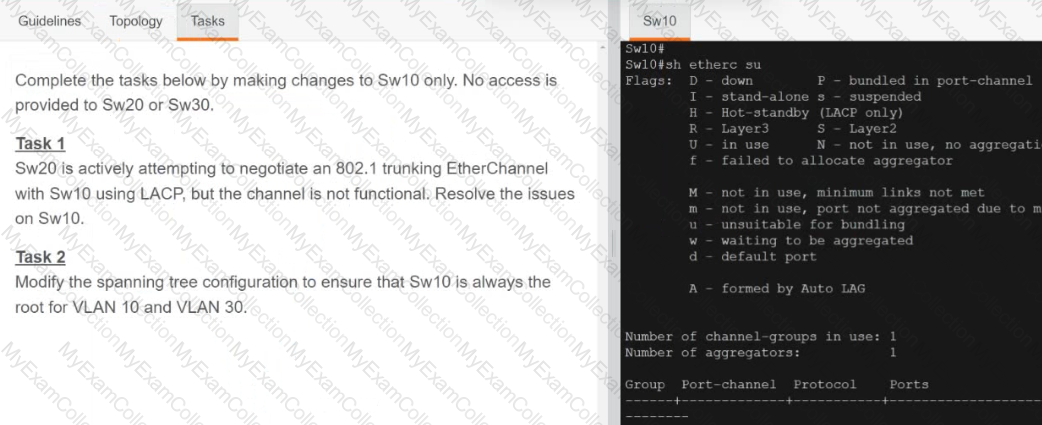
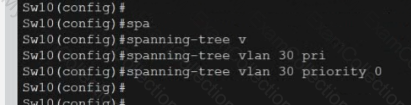 A black screen with white text
Description automatically generated
A black screen with white text
Description automatically generated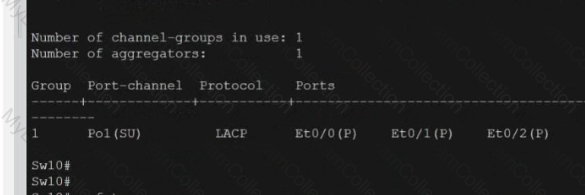 A screenshot of a computer program
Description automatically generated
A screenshot of a computer program
Description automatically generated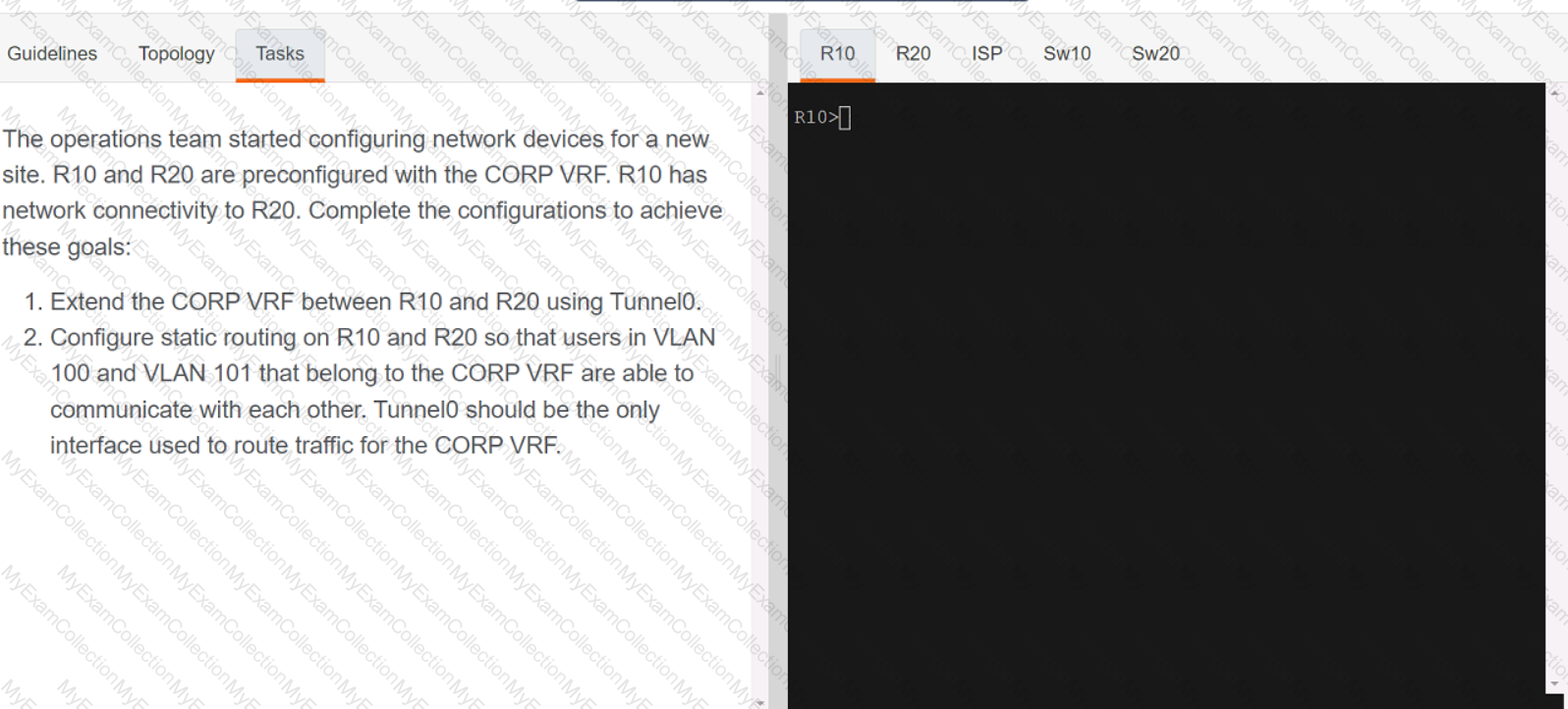

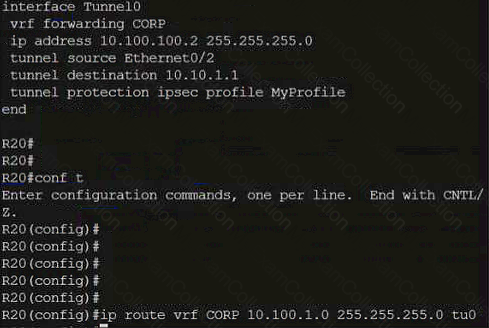
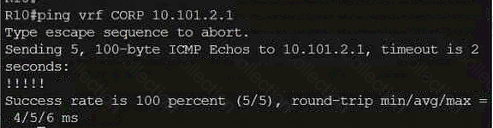

 A computer screen shot of a program
Description automatically generated
A computer screen shot of a program
Description automatically generated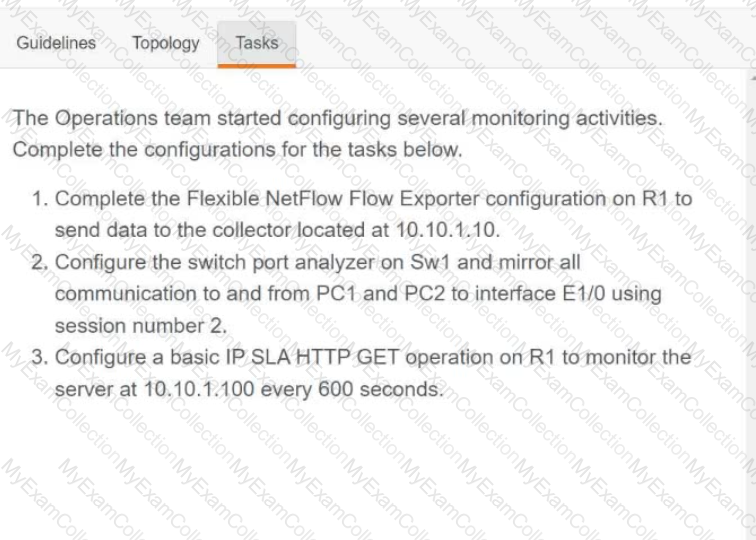
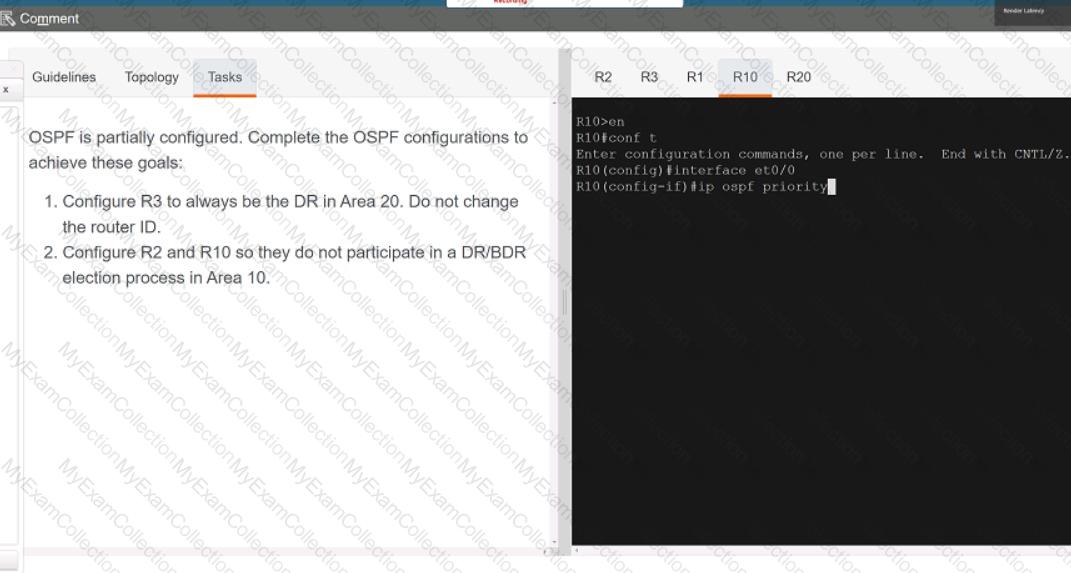
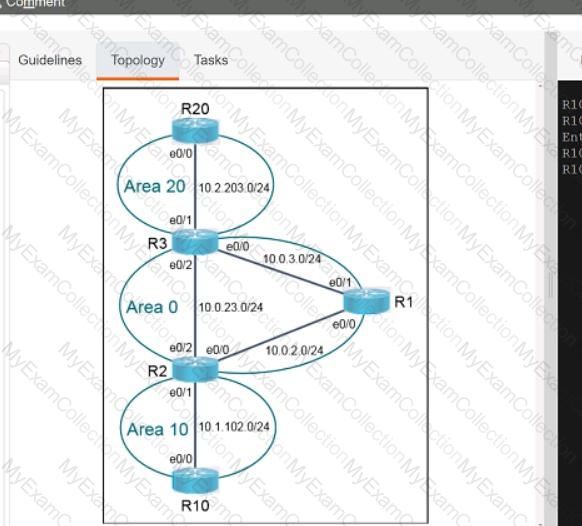
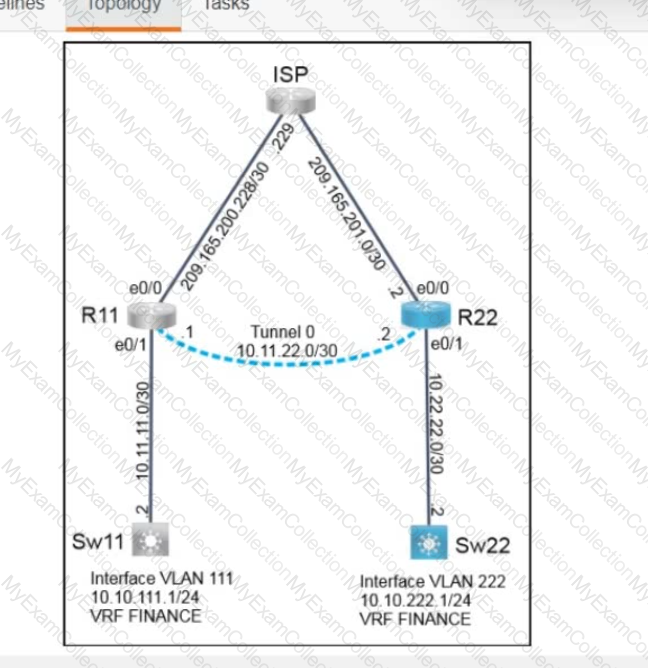
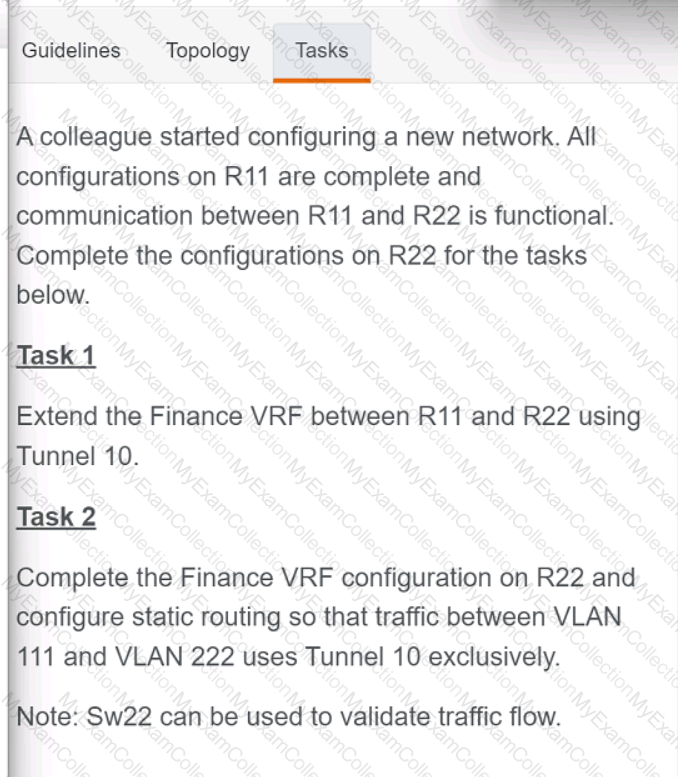
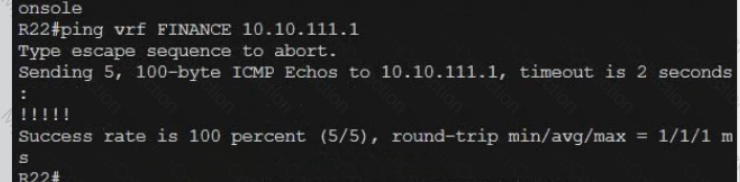 A black screen with white text
Description automatically generated
A black screen with white text
Description automatically generated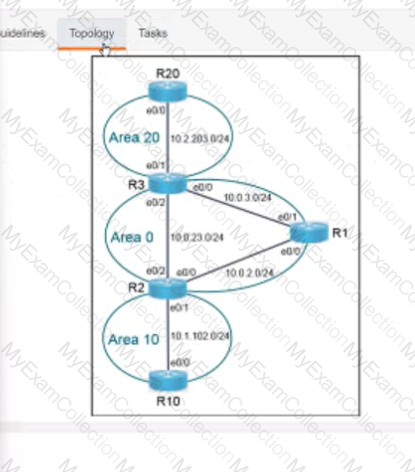
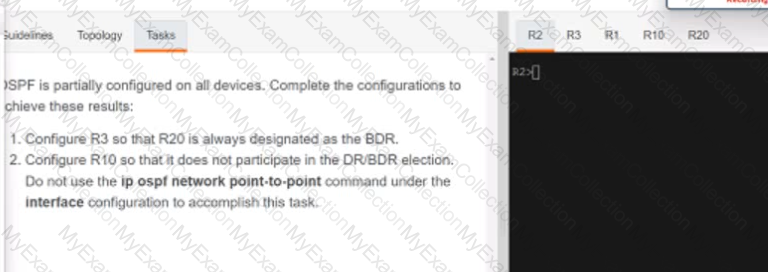
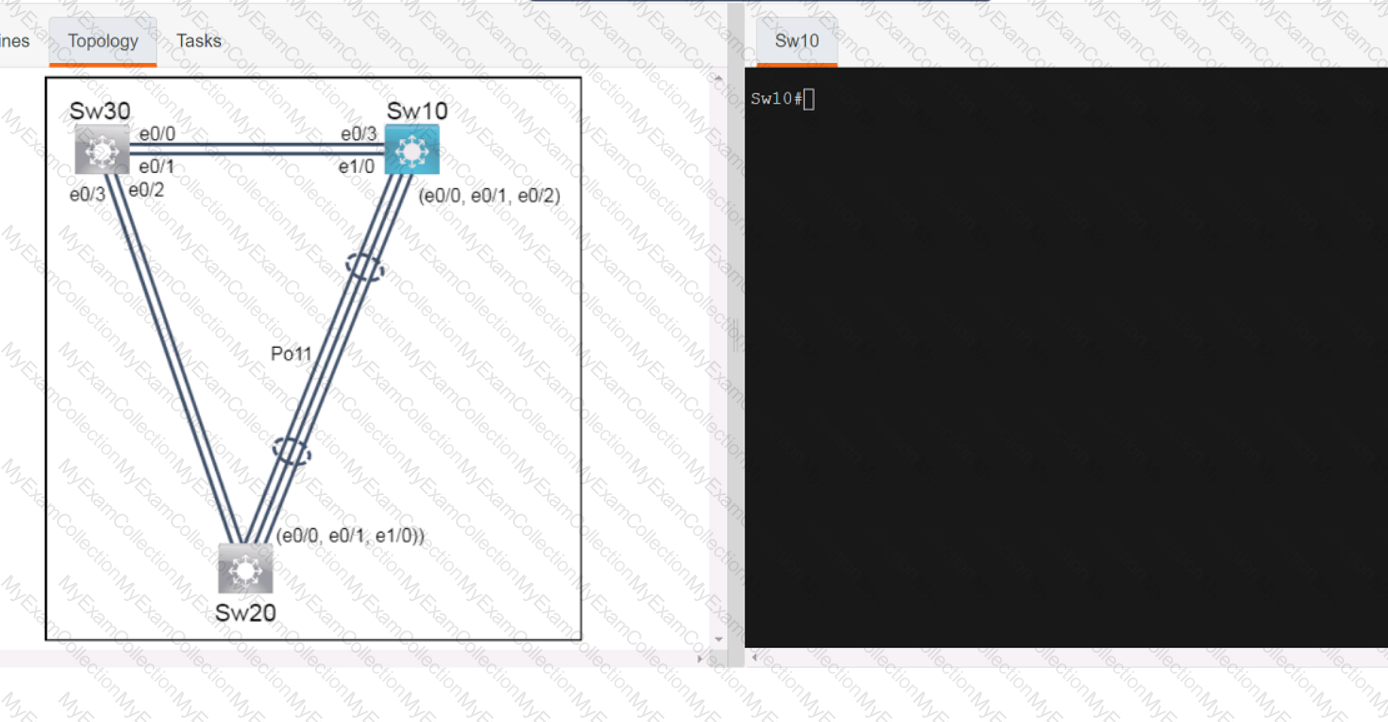
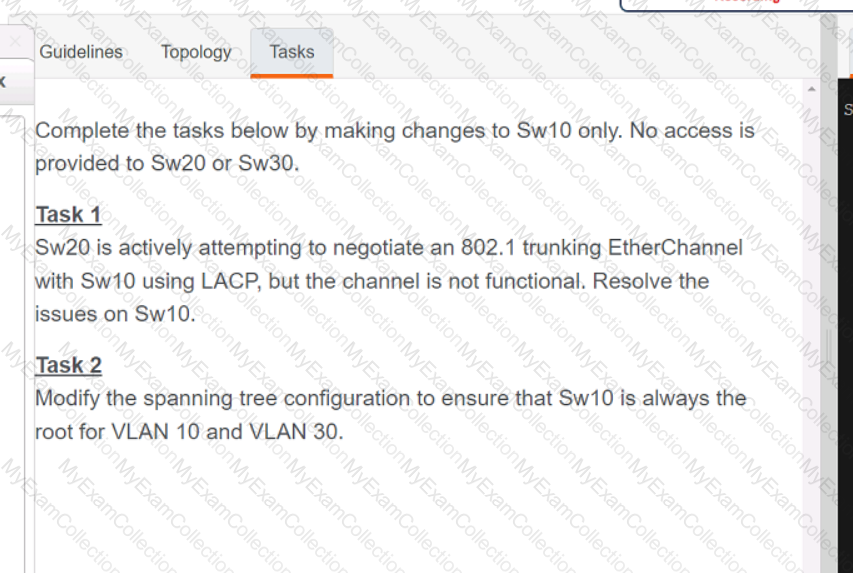
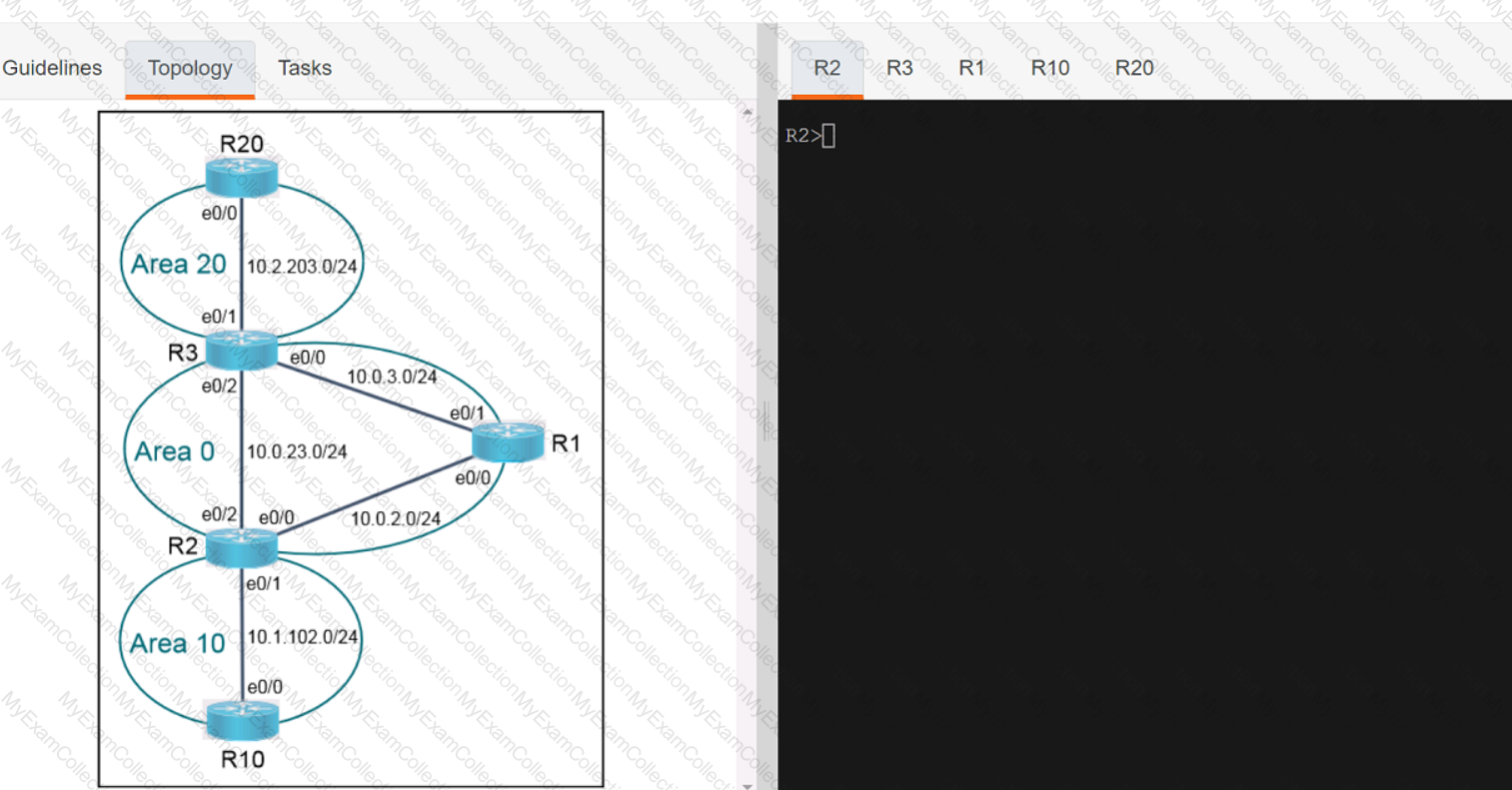
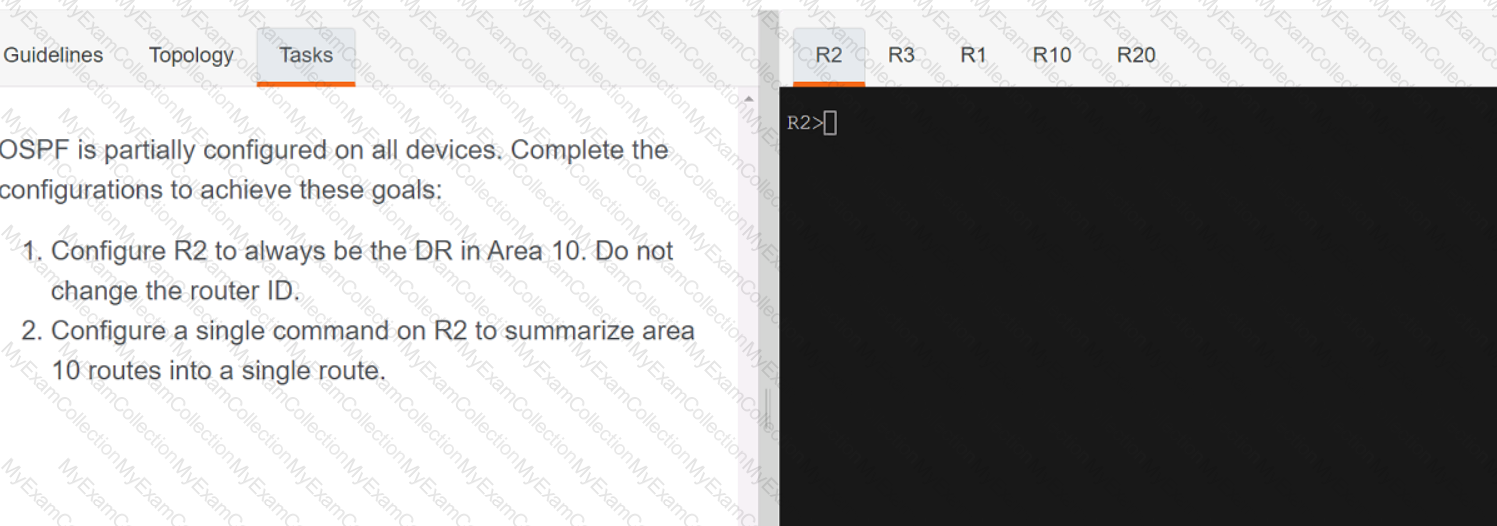
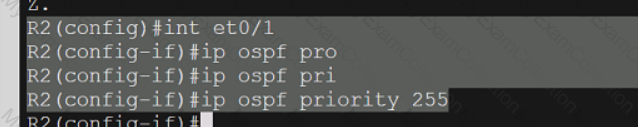
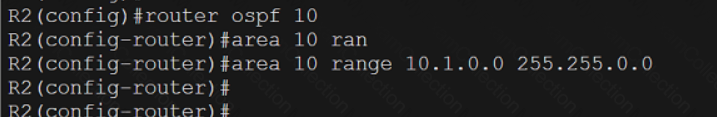
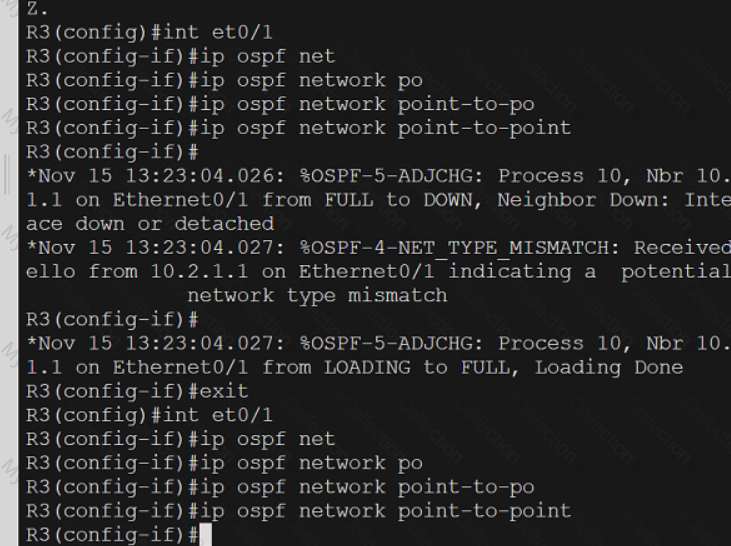
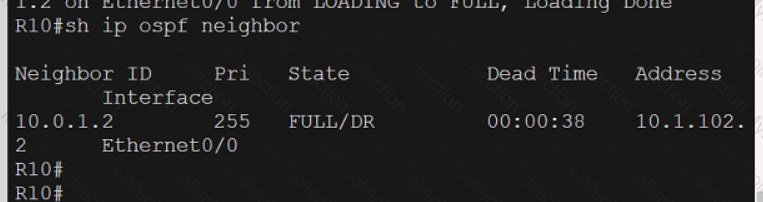

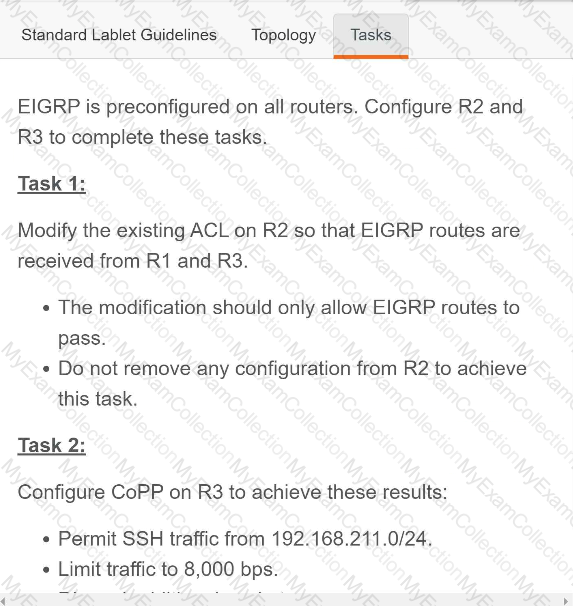
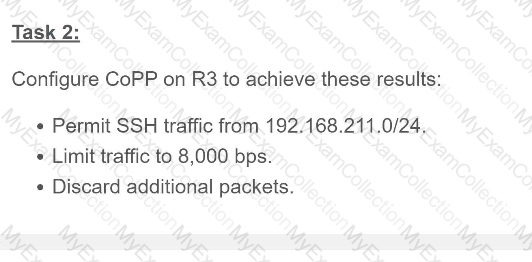
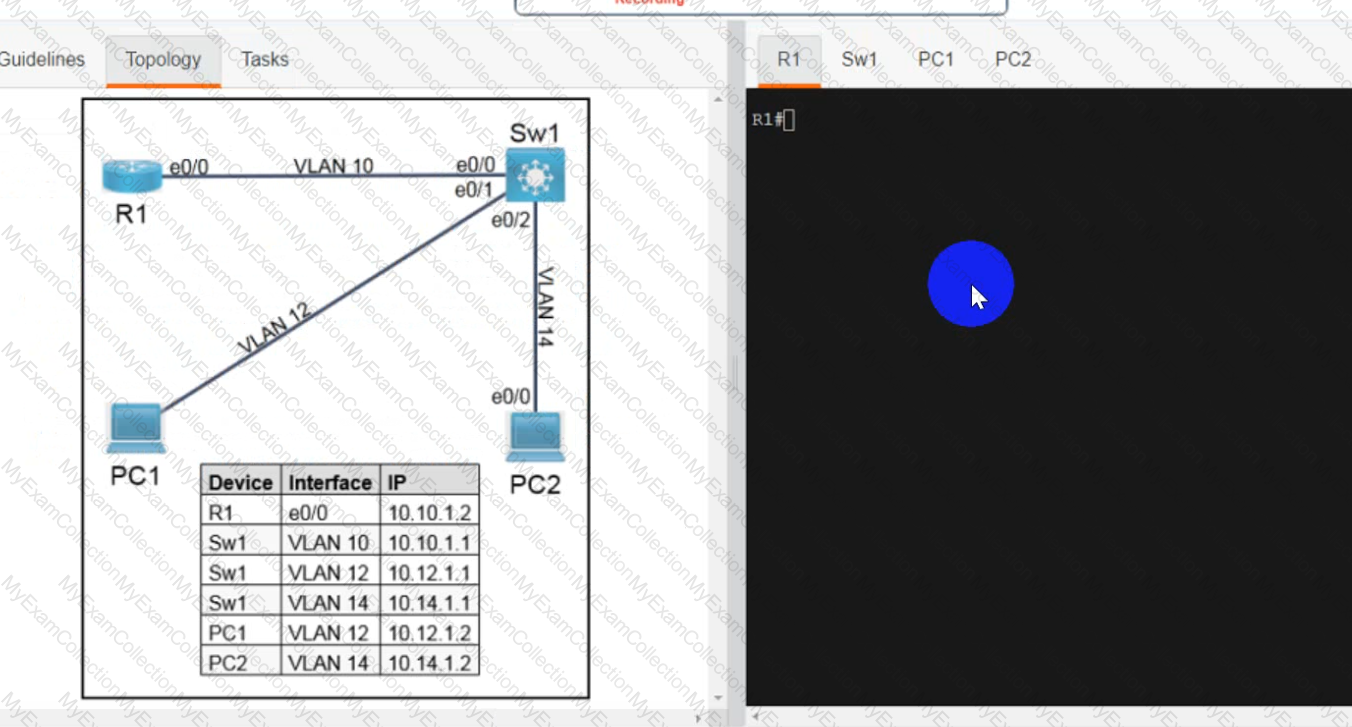
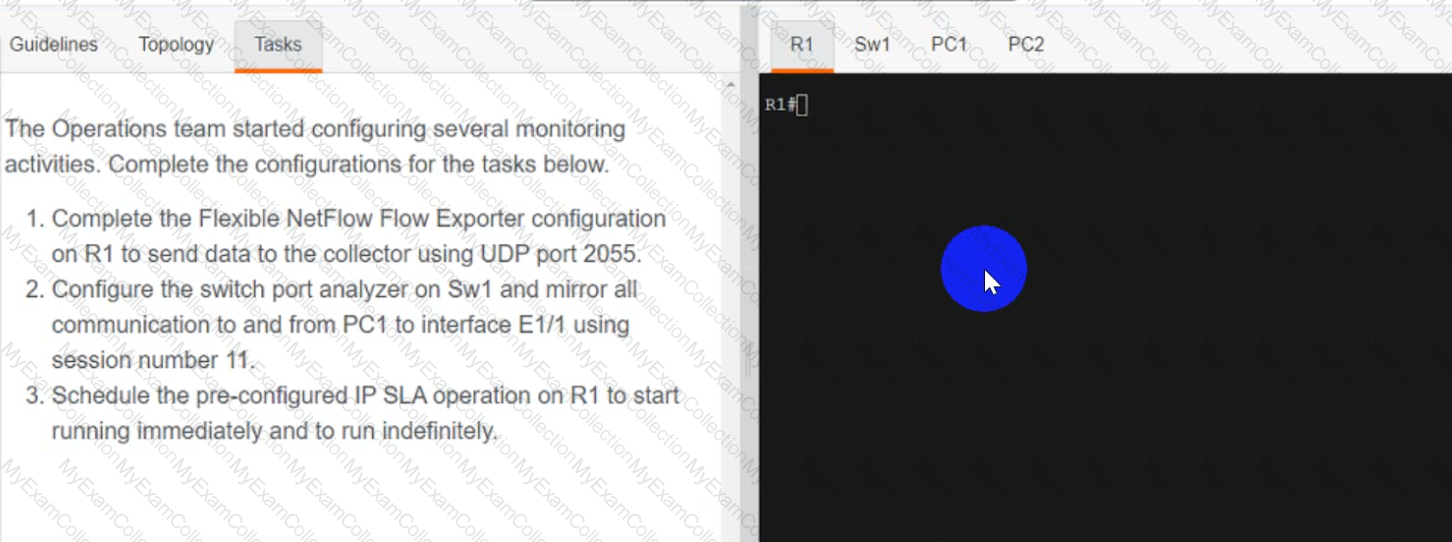
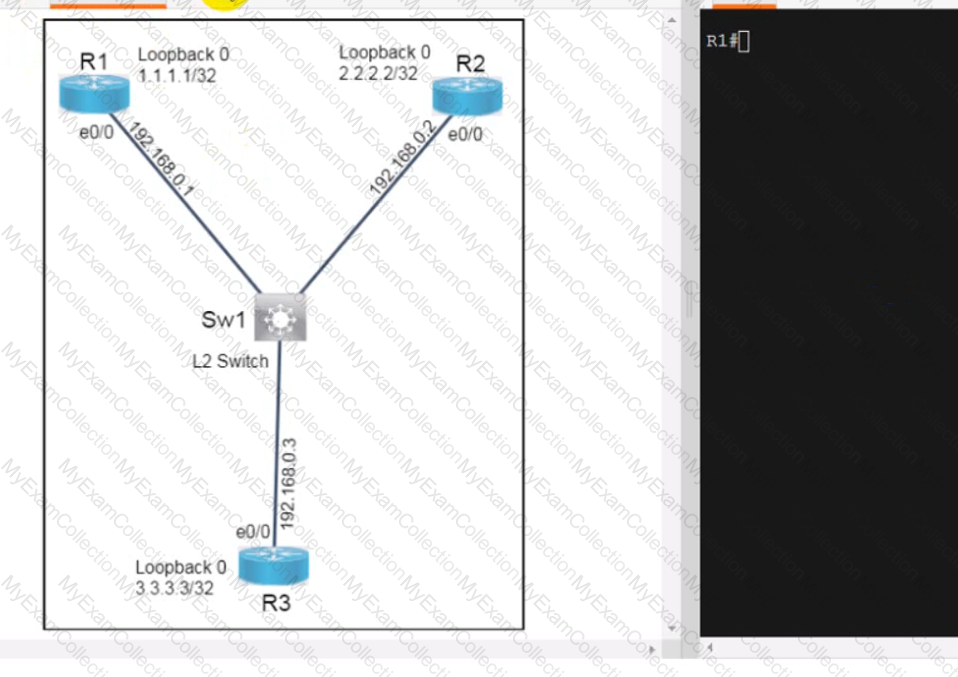
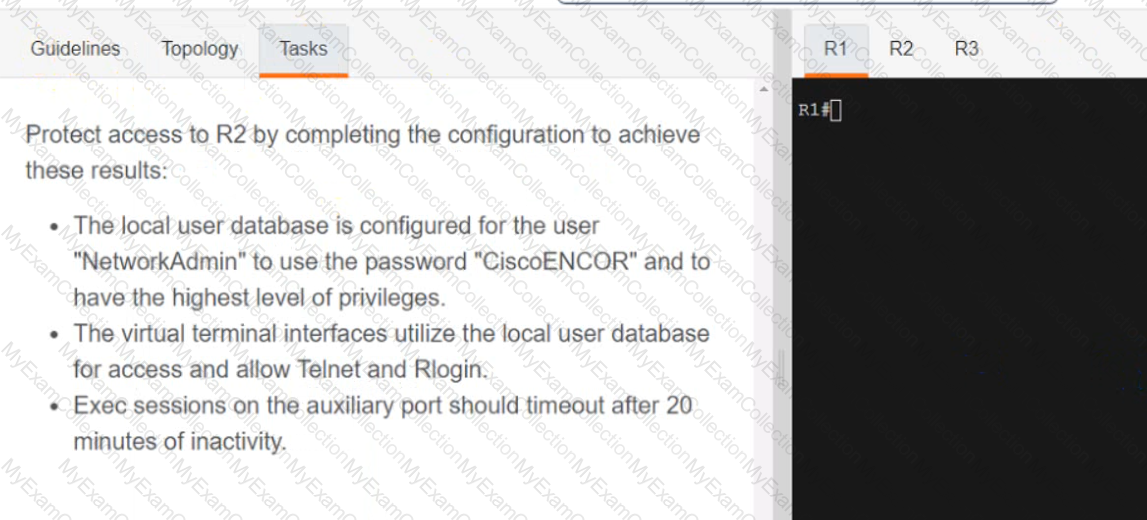
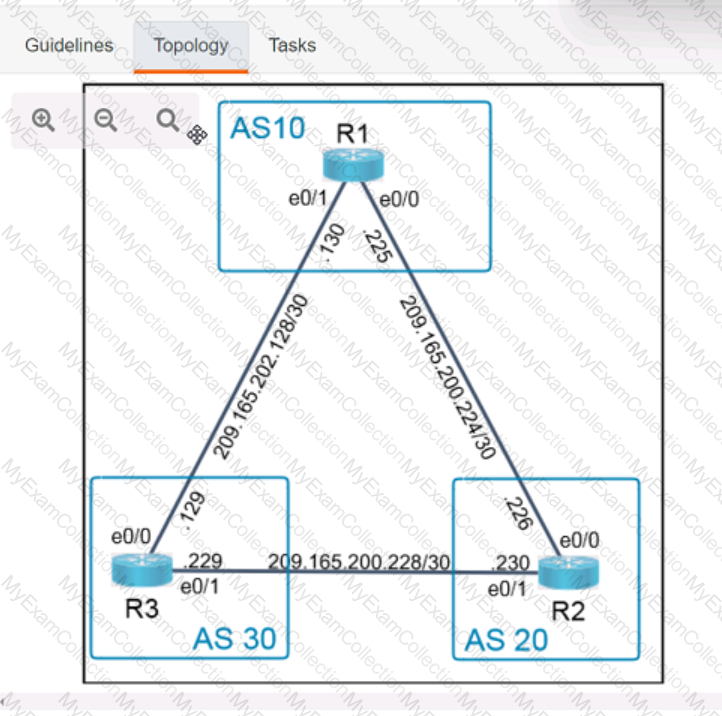
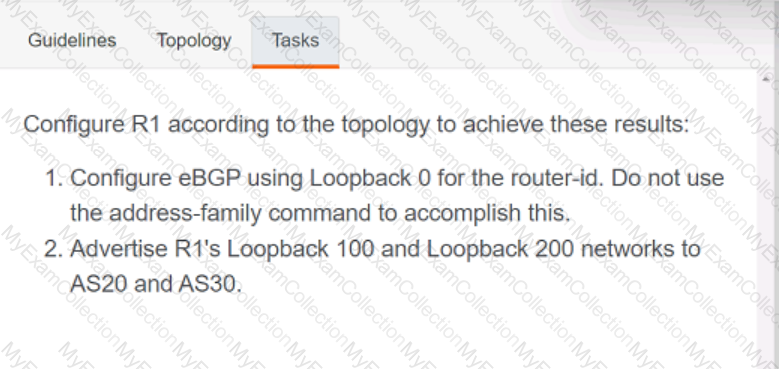
 A screen shot of a computer
Description automatically generated
A screen shot of a computer
Description automatically generated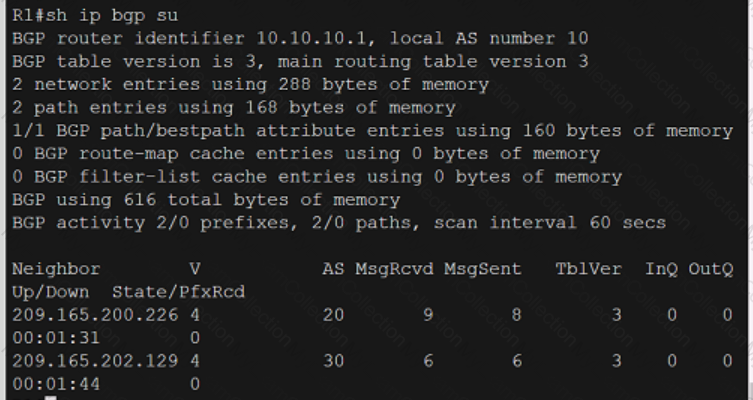 A computer screen shot of a black screen
Description automatically generated
A computer screen shot of a black screen
Description automatically generated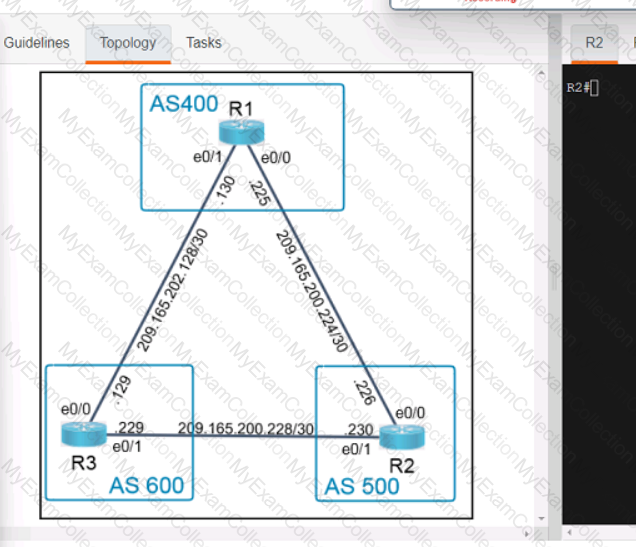 A screenshot of a computer
Description automatically generated
A screenshot of a computer
Description automatically generated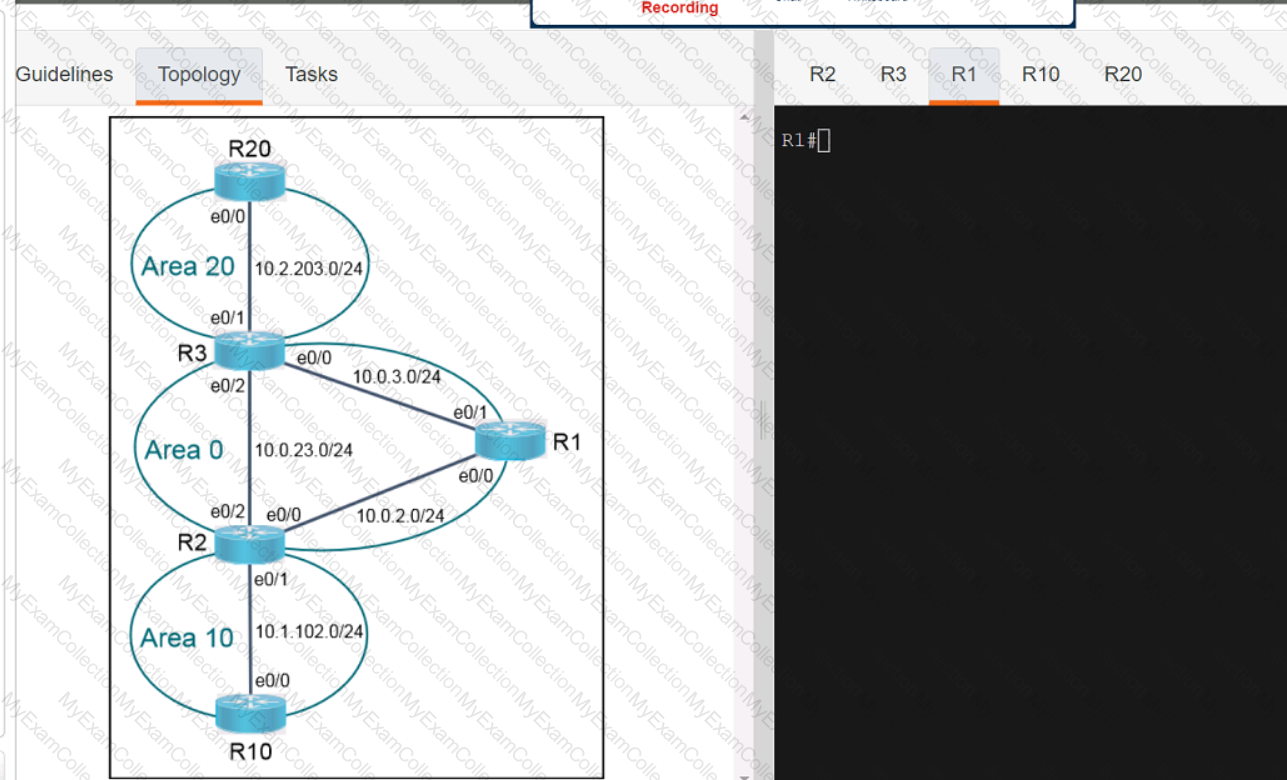
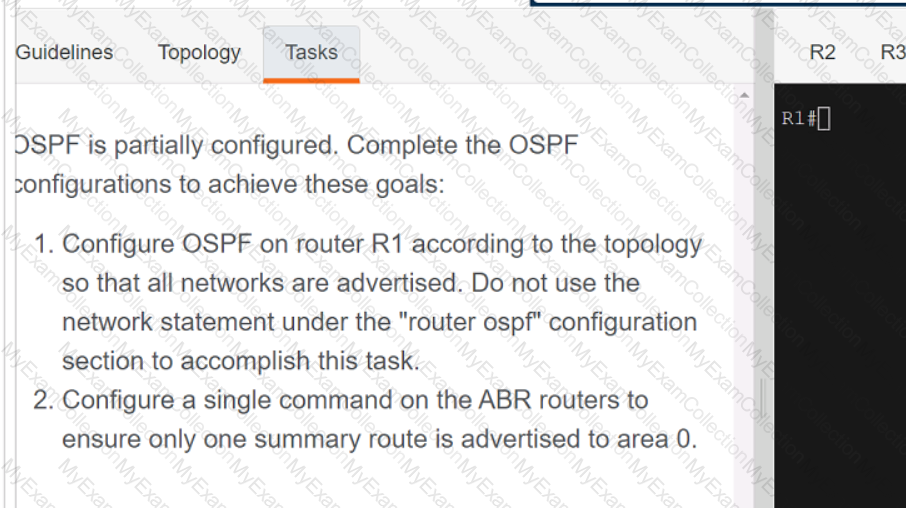
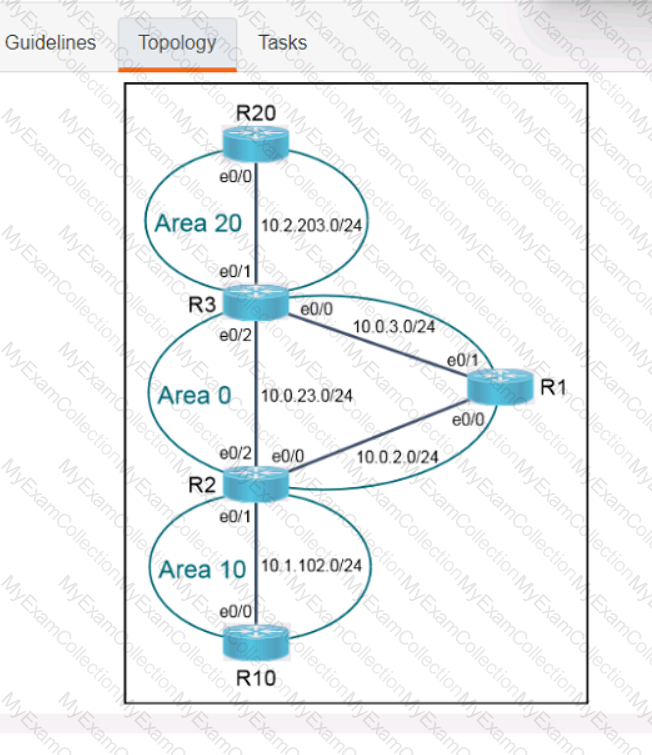

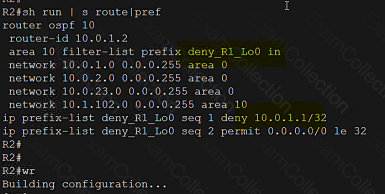

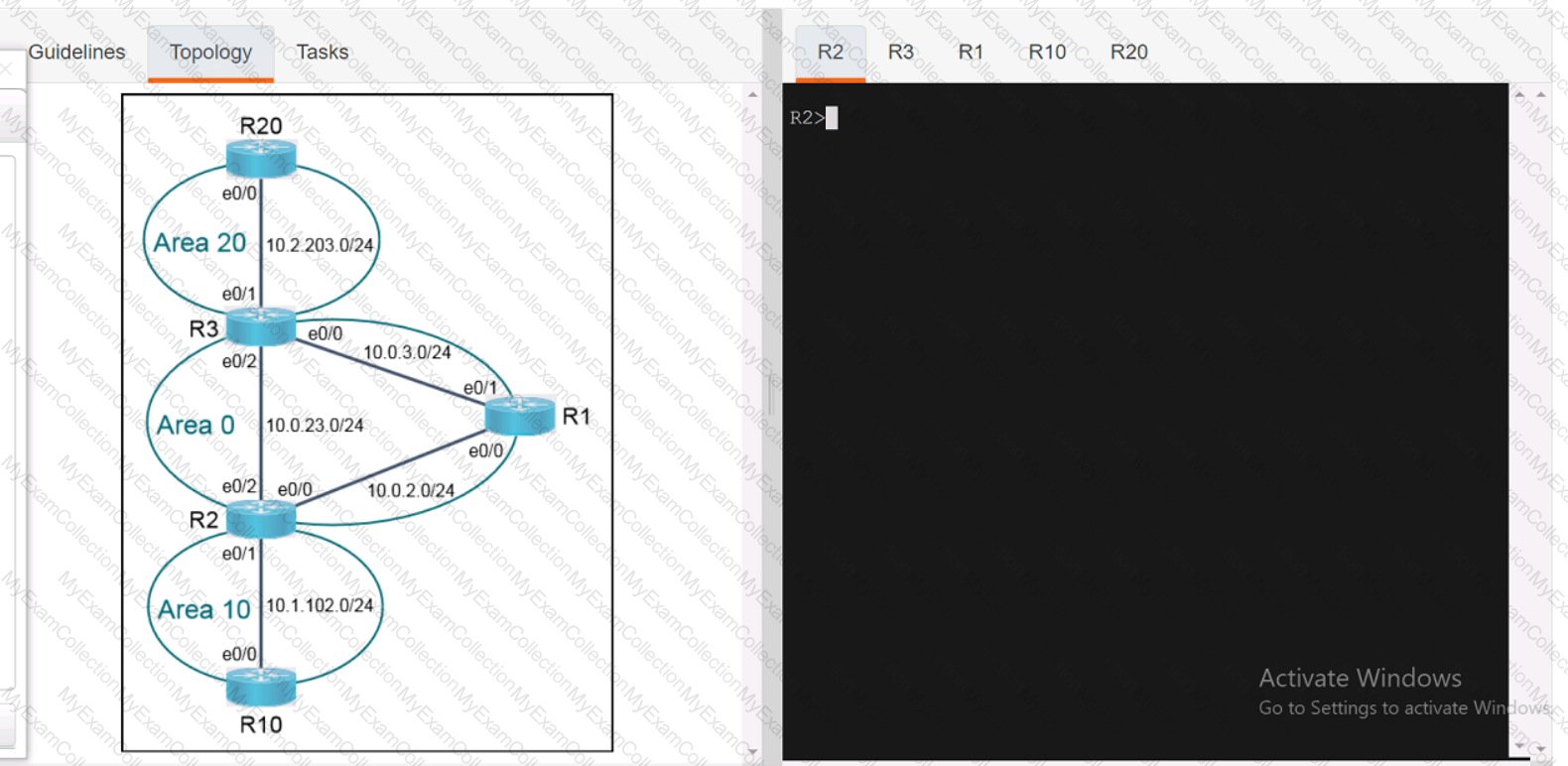
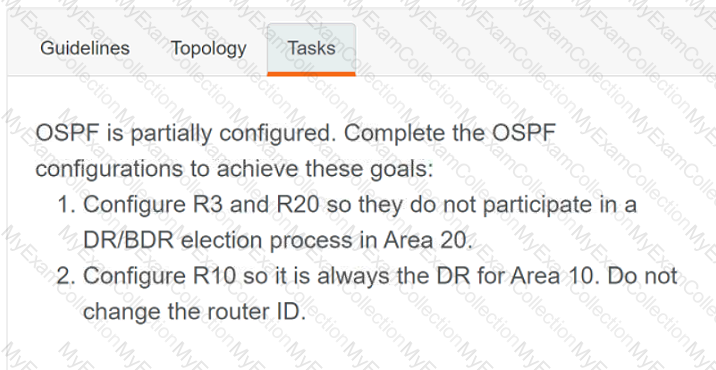
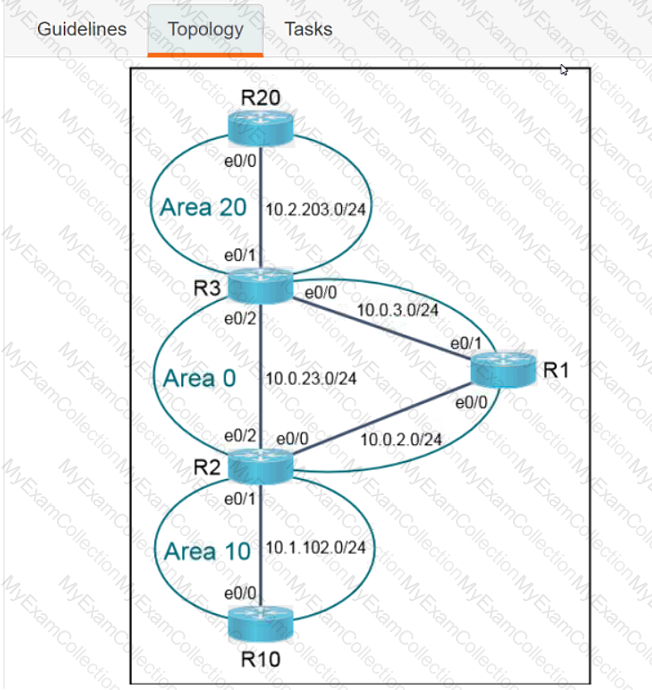
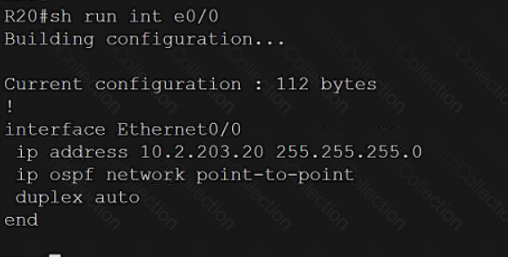
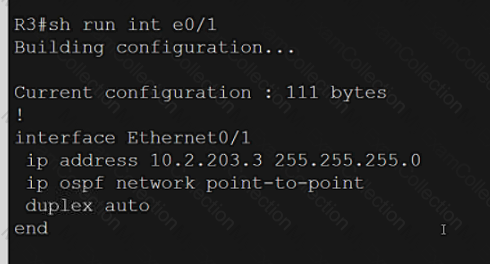
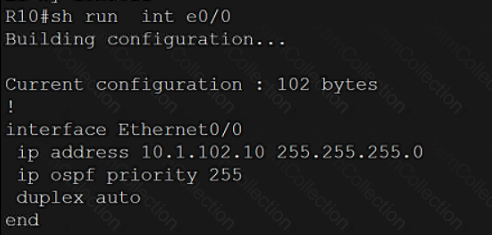
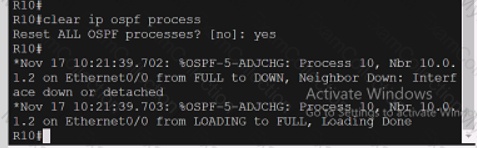
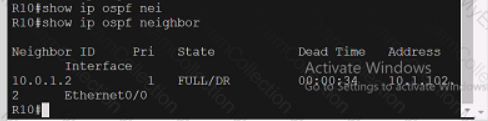

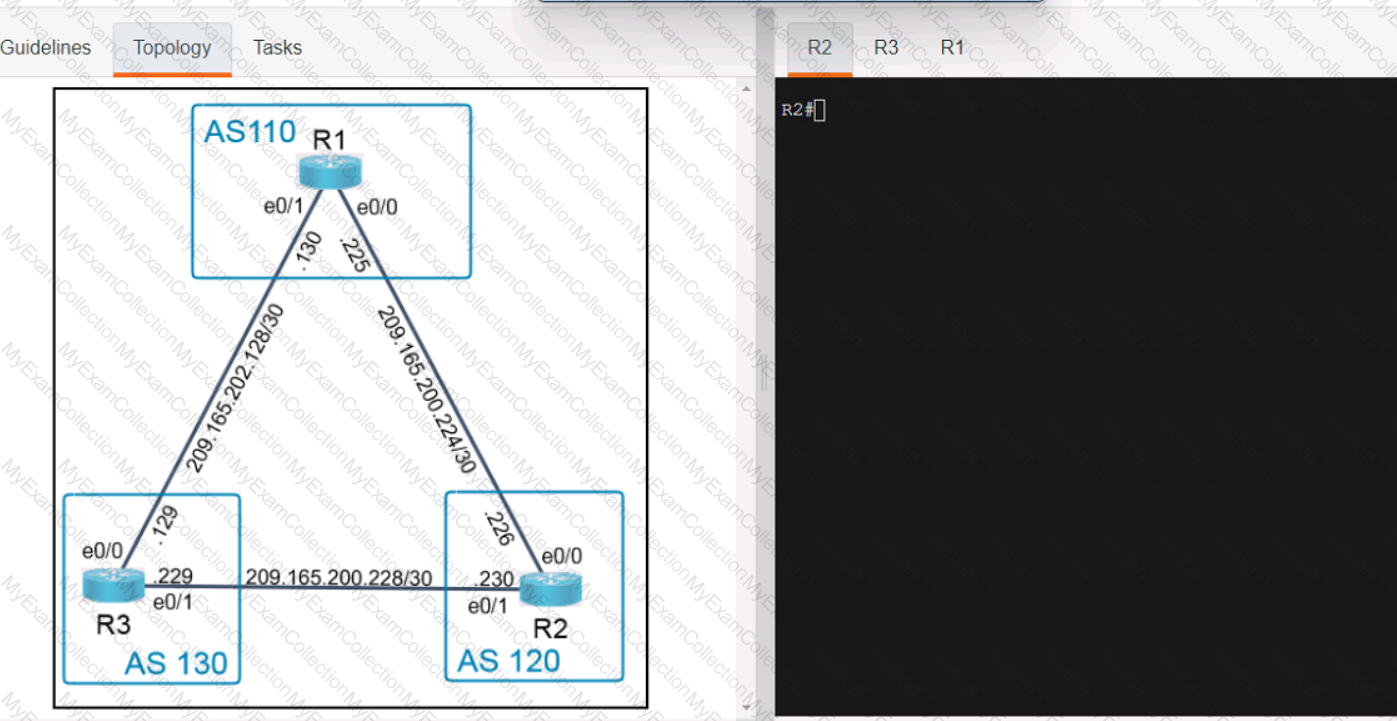
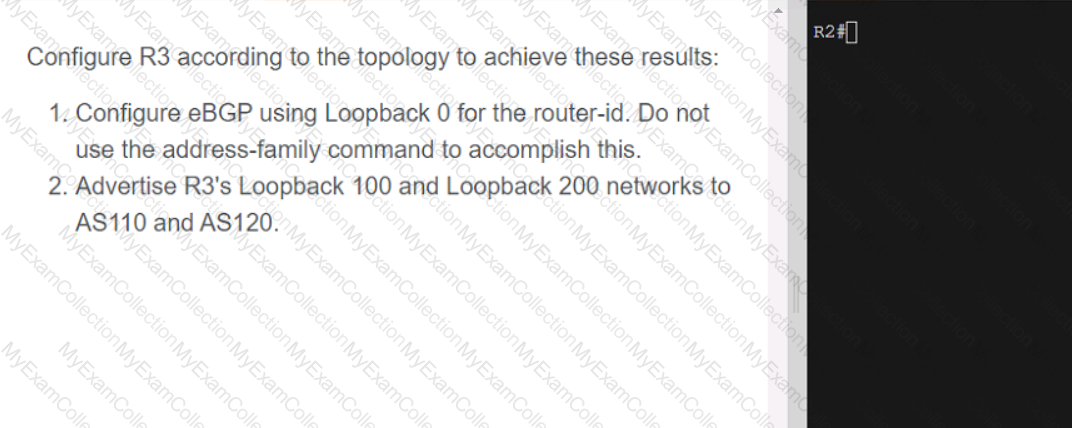
 A computer screen shot of a program
Description automatically generated
A computer screen shot of a program
Description automatically generated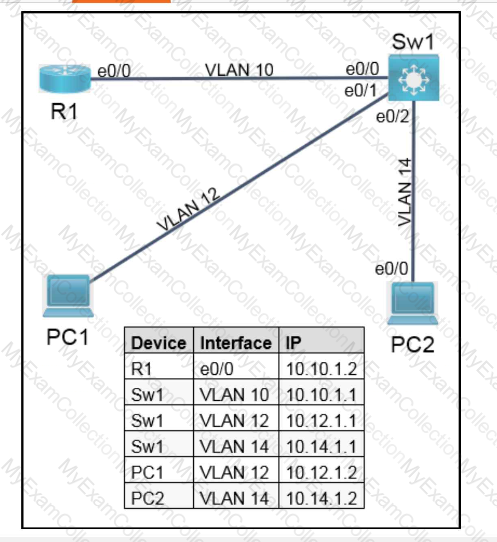
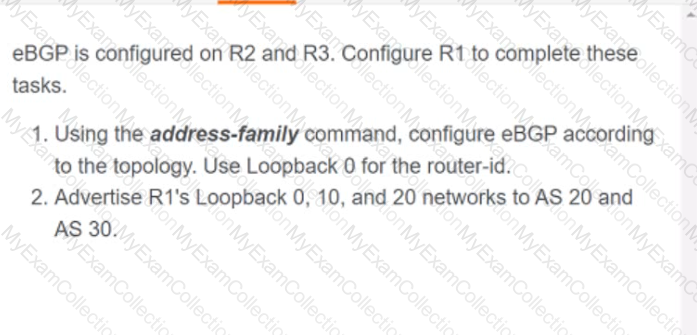

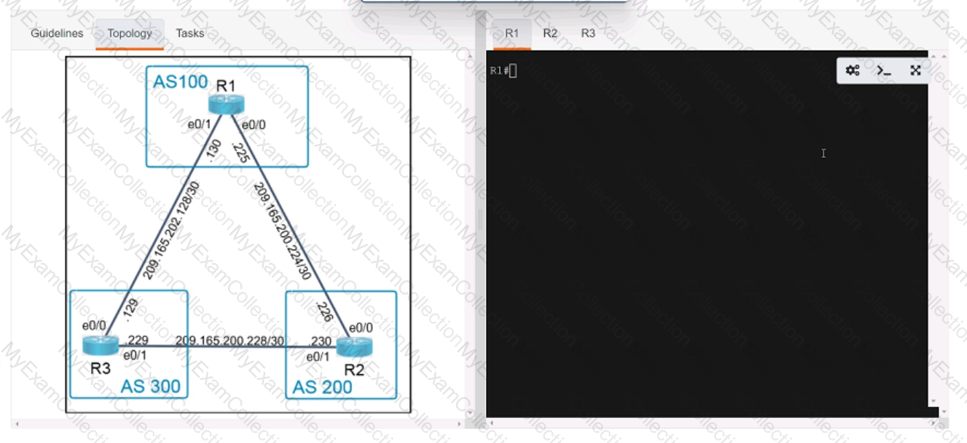
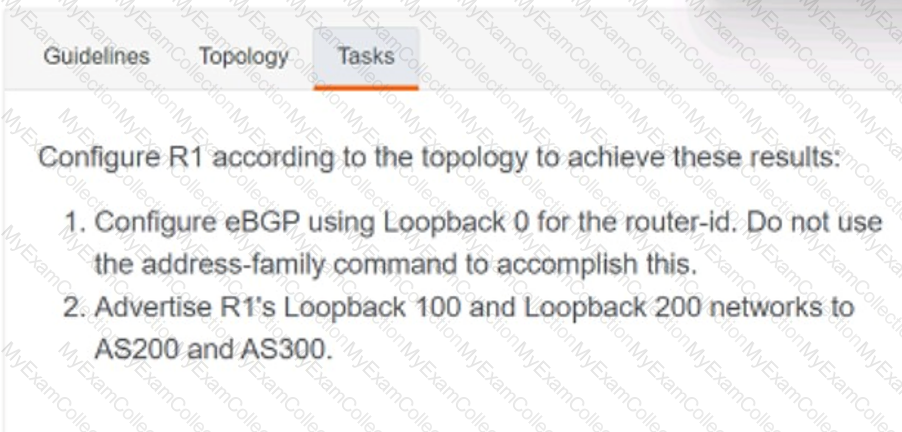

 A computer screen with white text
Description automatically generated
A computer screen with white text
Description automatically generated A computer screen with white text
Description automatically generated
A computer screen with white text
Description automatically generated