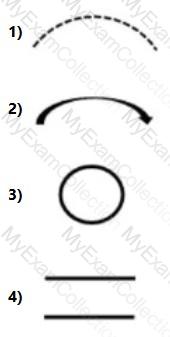
Which of the following DFD component is used to represent the change in privilege levels?
3
4
1
2
Answer:
Explanation:
 In a DFD, different components represent different aspects of the system:
- Circles or ovals usually represent processes or functions where data is processed or transformed.
- Arrows represent data flows moving from one part of the system to another.
- Open rectangles represent external entities or actors that interact with the system.
- Parallel lines represent data stores or repositories where data is held.
Given these conventions, a change in privilege levels would most likely be associated with a process, as it involves a transformation or decision within the system. Therefore, the component that represents a process (typically a circle or oval) would be used to depict a change in privilege levels.
References:Â For accurate and verified answers, please refer to the official EC-Council Application Security Engineer (CASE) JAVA study guides and course materials12. These resources will provide the most reliable information regarding the specifics of DFD components as they pertain to the CASE JAVA certification.
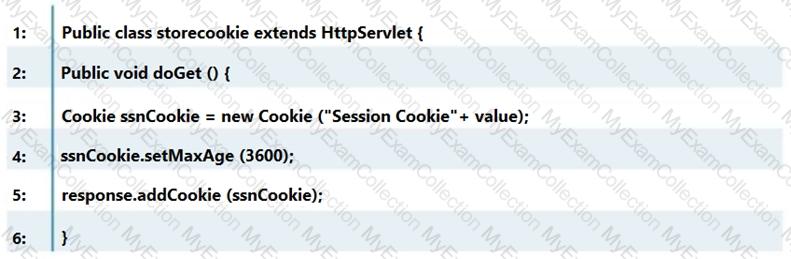
Which line of the following example of Java Code can make application vulnerable to a session attack?
Line No. 1
Line No. 3
Line No. 4
Line No. 5
Answer:
Explanation:
In general, session management is a critical aspect of application security. A common vulnerability related to session management is the improper handling of session tokens, which can lead to session hijacking or fixation attacks. Without seeing the specific code, it’s difficult to determine which line would be vulnerable. However, typical issues include:
- Line No. 1: If this line declares the servlet without proper security configuration, it could be vulnerable.
- Line No. 3: If this line involves the creation or handling of a session token without secure attributes (such as HttpOnly or Secure flags), it could make the application vulnerable.
- Line No. 4: If this line sets the session token’s expiration too long, it could increase the risk of token theft.
- Line No. 5: If this line sends the session token to the client without encryption, it could be intercepted.
References:For verified answers and detailed explanations, please refer to the official EC-Council Application Security Engineer (CASE) JAVA study guides and courses. You can find more information and resources on their official website and iClass platform.
Which of the following relationship is used to describe security use case scenario?
Threatens Relationship
Extend Relationship
Mitigates Relationship
Include Relationship
Answer:
Explanation:
 In the context of security use case scenarios, a ‘Mitigates Relationship’ is used to describe how a security control, policy, or guideline is intended to prevent or mitigate an attack scenario1. This relationship is crucial in defining how a particular security measure addresses a potential threat or vulnerability within the system.
For example, if a security use case scenario involves preventing a phishing attack, the ‘Mitigates Relationship’ would describe how anti-phishing controls or user training programs are designed to reduce the risk or impact of such attacks. This relationship helps in mapping out the defense mechanisms against the identified threats in a structured manner.
References: The concept of a ‘Mitigates Relationship’ in security use case scenarios can be found in various security frameworks and guidelines. While I cannot provide direct references to EC-Council Application Security Engineer (CASE) JAVA documents, this relationship is aligned with industry-standard practices for describing how security measures counteract specific threats. For detailed information, one would refer to the EC-Council’s CASE JAVA courses and study guides, which provide insights into security use cases and the relationships between different components within those scenarios.
Which of the risk assessment model is used to rate the threats-based risk to the application during threat modeling process?
DREAD
SMART
STRIDE
RED
Answer:
Explanation:
STRIDE is a risk assessment model used to identify and rate threats during the threat modeling process. It stands for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. Each element of STRIDE represents a specific type of threat that could potentially affect an application, and it is used to systematically assess the security of an application by identifying possible vulnerabilities that could be exploited by these threats.
References: The EC-Council’s Certified Application Security Engineer (CASE) JAVA course emphasizes the importance of threat modeling in the software development lifecycle and specifically mentions the use of models like STRIDE to assess and mitigate risks12.
In which phase of secure development lifecycle the threat modeling is performed?
Coding phase
Testing phase
Deployment phase
Design phase
Answer:
Explanation:
Threat modeling is an essential process in the secure development lifecycle that is typically performed during the design phase. This process involves identifying, predicting, and defining potential threats, as well as determining the likelihood and impact of these threats on the application. By conducting threat modeling in the design phase, developers and security teams can proactively address security issues and integrate necessary countermeasures before the coding begins. This approach helps to minimize vulnerabilities and ensures that security considerations are embedded into the application from the early stages of development.
References: The EC-Council’s Certified Application Security Engineer (CASE) JAVA training and certification program emphasizes the importance of implementing secure methodologies and practices throughout the Software Development Lifecycle (SDLC), including the planning, creation, testing, and deployment of an application. The program specifically highlights the role of threat modeling in the design phase as a critical security activity1234.
Which of the following configurations can help you avoid displaying server names in server response header?
< Connector port="8080" protocol="HTTP/1.1" connectionTimeout="20000" redirectPort= "8443" / >
< Connector port="8080" protocol="HTTP/1.1" connectionTimeout="20000" ServerName=" disable" redirectPort="8443" / >
< Connector port="8080" protocol="HTTP/1.1" connectionTimeout="20000" Server = " " redirectPort="8443" / >
< Connector port="8080" protocol="HTTP/1.1" connectionTimeout="20000" ServerName ="null " redirectPort="8443'' / >
Answer:
Explanation:
To prevent the server name from being displayed in the server response header, you should set the Server attribute to an empty string. This is because the server name is included in the HTTP response headers by default, and setting it to an empty string effectively removes this information, thus not disclosing the identity of the server software being used.
References: The EC-Council’s Certified Application Security Engineer (CASE) JAVA materials cover various aspects of secure application development, including the configuration of servers to enhance security. While the exact configuration details can vary based on the server and environment, the principle of setting the Server attribute to an empty string to hide the server information is a common practice in securing web applications as per the guidelines of secure application development.
Which of the following relationship is used to describe abuse case scenarios?
Include Relationship
Threatens Relationship
Extend Relationship
Mitigates Relationship
Answer:
Explanation:
 In the context of abuse case scenarios, the ‘Threatens Relationship’ is used to describe the interaction between an abuse case and the use case it threatens. This relationship helps to identify potential security threats and the ways in which they can exploit the functionalities of a system. By mapping out these relationships, developers and security engineers can better understand the attack vectors and design appropriate security measures to mitigate them.
References: The information provided is aligned with the EC-Council’s Certified Application Security Engineer (CASE) JAVA training and certification program, which emphasizes the importance of understanding application security threats and attacks within the Software Development Lifecycle (SDLC). For more detailed information, please refer to the EC-Council’s official CASE JAVA documentation and study guides12.
According to secure logging practices, programmers should ensure that logging processes are not disrupted by:
Catching incorrect exceptions
Multiple catching of incorrect exceptions
Re-throwing incorrect exceptions
Throwing incorrect exceptions
Answer:
Explanation:
 In secure logging practices, it is crucial to ensure that the logging process is robust and not disrupted by errors within the application itself. Throwing incorrect exceptions can disrupt the logging process because it may lead to unhandled exceptions that terminate the logging operation. This can result in a loss of critical log information which is essential for monitoring and troubleshooting. To prevent this, programmers should:
- Validate exceptions: Ensure that the exceptions thrown are accurate and relevant to the operation that failed.
- Handle exceptions properly: Use try-catch blocks to manage exceptions and maintain the logging process even when an error occurs.
- Avoid excessive logging: Do not log unnecessary information or sensitive data that could clutter the logs or expose vulnerabilities.
- Use appropriate log levels: Differentiate between error levels (e.g., info, debug, error) to categorize the severity of the logged events.
References: The EC-Council’s Certified Application Security Engineer (CASE) Java documentation emphasizes the importance of implementing secure methodologies and practices throughout the software development lifecycle (SDLC), including secure logging practices12. Additionally, best practices for logging in Java suggest protecting the logging process from disruption by managing exceptions correctly345.
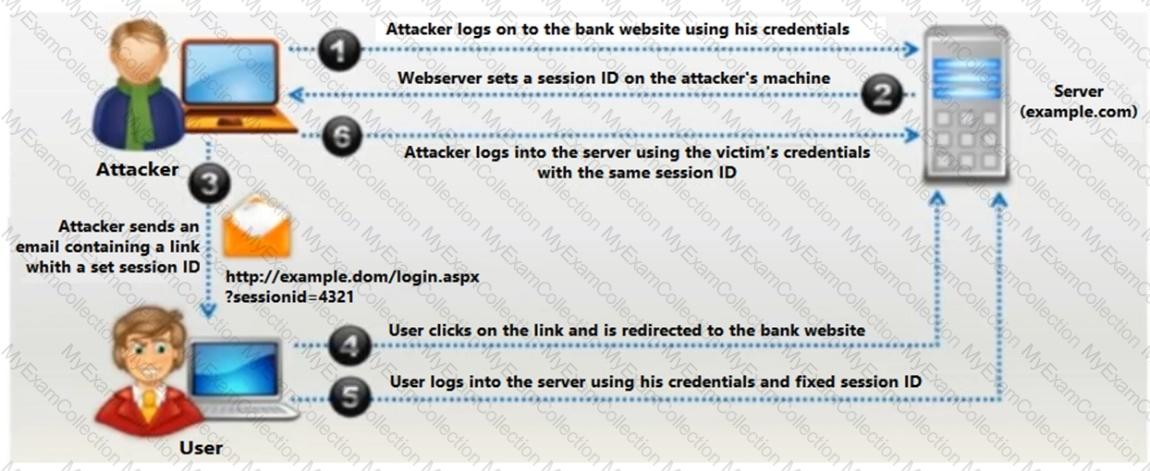
Identify the type of attack depicted in the figure below:
SQL injection attack
Parameter/form attack
Directory traversal attack
Session fixation attack
Answer:
Explanation:
The type of attack depicted in the figure is a session fixation attack. Here’s a step-by-step explanation of how this attack works:
- The attacker creates a new session on a website and obtains a valid session ID.
- The attacker then tricks the user into using this session ID, often by sending a link that includes the session ID as a parameter.
- When the user logs in using this session ID, the attacker, who now knows the session ID, can hijack the session.
- This allows the attacker to impersonate the user and carry out actions on their behalf.
In the context of the image, the steps are as follows:
- The attacker logs into a bank website using his credentials.
- The webserver sets a session ID on the attacker’s machine.
- The attacker logs into the server using the victim’s credentials with the same session ID.
- The attacker sends an email containing a link with a set session ID to the user.
- The user clicks on the link and is redirected to the bank website.
- The user logs into the server using his credentials and the fixed session ID.
- The attacker can then use the same session ID to gain unauthorized access.
References:Â For more information on session fixation attacks, you can refer to security resources such as OWASP (Open Web Application Security Project) and other cybersecurity publications that discuss common web vulnerabilities and their mitigation strategies.
Which of the following can be derived from abuse cases to elicit security requirements for software system?
Misuse cases
Data flow diagram
Use cases
Security use cases
Answer:
Explanation:
Misuse cases are derived from abuse cases and are used to elicit security requirements for a software system. They help in identifying and understanding how an application can be attacked or misused, which is essential for defining the security measures needed to protect the system. By analyzing misuse cases, developers and security engineers can anticipate potential threats and design the system to be resilient against them.
References: The concept of misuse cases is supported by various resources on application security and is aligned with the teachings of the EC-Council’s Certified Application Security Engineer (CASE) JAVA program. The references from the web search results and the EC-Council’s own documentation on the CASE JAVA certification emphasize the importance of understanding abuse cases to derive misuse cases for better security requirement elicitation123.
Which of the threat classification model is used to classify threats during threat modeling process?
RED
STRIDE
DREAD
SMART
Answer:
Explanation:
STRIDE is a threat classification model used during the threat modeling process. It stands for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. These categories represent the types of threats that can be posed to software systems. STRIDE helps in identifying potential security threats to a system and is commonly used to classify threats in threat modeling.
The STRIDE model is particularly useful because it covers a broad range of security threats and is designed to be easy to understand and apply. Each category of STRIDE addresses a specific area of security concern:
- Spoofing:Â Impersonating something or someone else.
- Tampering:Â Modifying data or code.
- Repudiation:Â Claiming not to have performed an action.
- Information Disclosure:Â Exposing information to someone not authorized to see it.
- Denial of Service (DoS):Â Interrupting access to resources.
- Elevation of Privilege:Â Gaining capabilities without proper authorization.
By using STRIDE, security professionals can systematically identify and address potential vulnerabilities within an application.
References:For detailed information and learning resources, please refer to the EC-Council’s Certified Application Security Engineer (CASE) JAVA courses and study guides, which provide extensive coverage on threat modeling and the STRIDE methodology12. These resources will offer a comprehensive understanding of the application of STRIDE in threat modeling. Additionally, the OWASP Foundation provides valuable insights into the threat modeling process, including the use of STRIDE13.

