Which of the following programs is usually targeted at Microsoft Office products?
Which of the following is an application that requires a host application for replication?
Which statement is TRUE regarding network firewalls preventing Web Application attacks?
Which of the following can the administrator do to verify that a tape backup can be recovered in its entirety?
Which of the following is a hardware requirement that either an IDS/IPS system or a proxy server must have in order to properly function?
Bluetooth uses which digital modulation technique to exchange information between paired devices?
Which of the following guidelines or standards is associated with the credit card industry?
International Organization for Standardization (ISO) standard 27002 provides guidance for compliance by outlining
An attacker uses a communication channel within an operating system that is neither designed nor intended to transfer information. What is the name of the communications channel?
Which of the following business challenges could be solved by using a vulnerability scanner?
Which of the following cryptography attack methods is usually performed without the use of a computer?
Which of the following conditions must be given to allow a tester to exploit a Cross-Site Request Forgery (CSRF) vulnerable web application?
While conducting a penetration test, the tester determines that there is a firewall between the tester's machine and the target machine. The firewall is only monitoring TCP handshaking of packets at the session layer of the OSI model. Which type of firewall is the tester trying to traverse?
What technique is used to perform a Connection Stream Parameter Pollution (CSPP) attack?
Windows file servers commonly hold sensitive files, databases, passwords and more. Which of the following choices would be a common vulnerability that usually exposes them?
A consultant is hired to do physical penetration testing at a large financial company. In the first day of his assessment, the consultant goes to the company`s building dressed like an electrician and waits in the lobby for an employee to pass through the main access gate, then the consultant follows the employee behind to get into the restricted area. Which type of attack did the consultant perform?
A pentester gains access to a Windows application server and needs to determine the settings of the built-in Windows firewall. Which command would be used?
At a Windows Server command prompt, which command could be used to list the running services?
What is the most secure way to mitigate the theft of corporate information from a laptop that was left in a hotel room?
A company firewall engineer has configured a new DMZ to allow public systems to be located away from the internal network. The engineer has three security zones set:
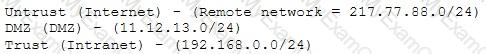
The engineer wants to configure remote desktop access from a fixed IP on the remote network to a remote desktop server in the DMZ. Which rule would best fit this requirement?
Which of the following is a client-server tool utilized to evade firewall inspection?
Which type of intrusion detection system can monitor and alert on attacks, but cannot stop them?
An engineer is learning to write exploits in C++ and is using the exploit tool Backtrack. The engineer wants to compile the newest C++ exploit and name it calc.exe. Which command would the engineer use to accomplish this?
How can a rootkit bypass Windows 7 operating system’s kernel mode, code signing policy?
Fingerprinting VPN firewalls is possible with which of the following tools?
Diffie-Hellman (DH) groups determine the strength of the key used in the key exchange process. Which of the following is the correct bit size of the Diffie-Hellman (DH) group 5?
Which of the following does proper basic configuration of snort as a network intrusion detection system require?
A pentester is using Metasploit to exploit an FTP server and pivot to a LAN. How will the pentester pivot using Metasploit?
Which system consists of a publicly available set of databases that contain domain name registration contact information?
If the final set of security controls does not eliminate all risk in a system, what could be done next?
Which of the following techniques will identify if computer files have been changed?
An NMAP scan of a server shows port 69 is open. What risk could this pose?
An NMAP scan of a server shows port 25 is open. What risk could this pose?
What is one thing a tester can do to ensure that the software is trusted and is not changing or tampering with critical data on the back end of a system it is loaded on?
Passive reconnaissance involves collecting information through which of the following?
John the Ripper is a technical assessment tool used to test the weakness of which of the following?
When utilizing technical assessment methods to assess the security posture of a network, which of the following techniques would be most effective in determining whether end-user security training would be beneficial?
A user on your Windows 2000 network has discovered that he can use L0phtcrack to sniff the SMB exchanges which carry user logons. The user is plugged into a hub with 23 other systems.
However, he is unable to capture any logons though he knows that other users are logging in.
What do you think is the most likely reason behind this?
You are attempting to crack LM Manager hashed from Windows 2000 SAM file. You will be using LM Brute force hacking tool for decryption. What encryption algorithm will you be decrypting?
It is a kind of malware (malicious software) that criminals install on your computer so they can lock it from a remote location. This malware generates a pop-up window, webpage, or email warning from what looks like an official authority. It explains that your computer has been locked because of possible illegal activities on it and demands payment before you can access your files and programs again.
Which of the following terms best matches the definition?
An Internet Service Provider (ISP) has a need to authenticate users connecting using analog modems, Digital Subscriber Lines (DSL), wireless data services, and Virtual Private Networks (VPN) over a Frame Relay network.
Which AAA protocol is most likely able to handle this requirement?
A hacker has managed to gain access to a Linux host and stolen the password file from /etc/passwd. How can he use it?
Which of the following is a vulnerability in GNU’s bash shell (discovered in September of 2014) that gives attackers access to run remote commands on a vulnerable system?
Supposed you are the Chief Network Engineer of a certain Telco. Your company is planning for a big business expansion and it requires that your network authenticate users connecting using analog modems, Digital Subscriber Lines (DSL), wireless data services, and Virtual Private Networks (VPN) over a Frame Relay network. Which AAA protocol would you implement?
In which phase of the ethical hacking process can Google hacking be employed? This is a technique that involves manipulating a search string with specific operators to search for vulnerabilities.
Example:
allintitle: root passwd
Which of the following tools is used to analyze the files produced by several packet-capture programs such as tcpdump, WinDump, Wireshark, and EtherPeek?
Which type of Nmap scan is the most reliable, but also the most visible, and likely to be picked up by and IDS?
Which of the following statements about a zone transfer is correct? (Choose three.)
A computer technician is using a new version of a word processing software package when it is discovered that a special sequence of characters causes the entire computer to crash. The technician researches the bug and discovers that no one else experienced the problem. What is the appropriate next step?
A certified ethical hacker (CEH) is approached by a friend who believes her husband is cheating. She offers to pay to break into her husband's email account in order to find proof so she can take him to court. What is the ethical response?
An ethical hacker for a large security research firm performs penetration tests, vulnerability tests, and risk assessments. A friend recently started a company and asks the hacker to perform a penetration test and vulnerability assessment of the new company as a favor. What should the hacker's next step be before starting work on this job?
A certified ethical hacker (CEH) completed a penetration test of the main headquarters of a company almost two months ago, but has yet to get paid. The customer is suffering from financial problems, and the CEH is worried that the company will go out of business and end up not paying. What actions should the CEH take?
A consultant has been hired by the V.P. of a large financial organization to assess the company's security posture. During the security testing, the consultant comes across child pornography on the V.P.'s computer. What is the consultant's obligation to the financial organization?
Which initial procedure should an ethical hacker perform after being brought into an organization?
Which of the following describes a component of Public Key Infrastructure (PKI) where a copy of a private key is stored to provide third-party access and to facilitate recovery operations?
If an e-commerce site was put into a live environment and the programmers failed to remove the secret entry point that was used during the application development, what is this secret entry point known as?
Advanced encryption standard is an algorithm used for which of the following?
An IT security engineer notices that the company’s web server is currently being hacked. What should the engineer do next?
Which of the following network attacks relies on sending an abnormally large packet size that exceeds TCP/IP specifications?
Which statement best describes a server type under an N-tier architecture?

