What is the process of monitoring and capturing all data packets passing through a given network using different tools?
Identify the attack, where an attacker tries to discover all the possible information about a target network before launching a further attack.
Which of the following stage executed after identifying the required event sources?
Chloe, a SOC analyst with Jake Tech, is checking Linux systems logs. She is investigating files at /var/log/ wtmp.
What Chloe is looking at?
Which of the following attack can be eradicated by disabling of "allow_url_fopen and allow_url_include" in the php.ini file?
Which of the following fields in Windows logs defines the type of event occurred, such as Correlation Hint, Response Time, SQM, WDI Context, and so on?
Which of the following technique protects from flooding attacks originated from the valid prefixes (IP addresses) so that they can be traced to its true source?
The threat intelligence, which will help you, understand adversary intent and make informed decision to ensure appropriate security in alignment with risk.
What kind of threat intelligence described above?
Which of the following tool can be used to filter web requests associated with the SQL Injection attack?
John as a SOC analyst is worried about the amount of Tor traffic hitting the network. He wants to prepare a dashboard in the SIEM to get a graph to identify the locations from where the TOR traffic is coming.
Which of the following data source will he use to prepare the dashboard?
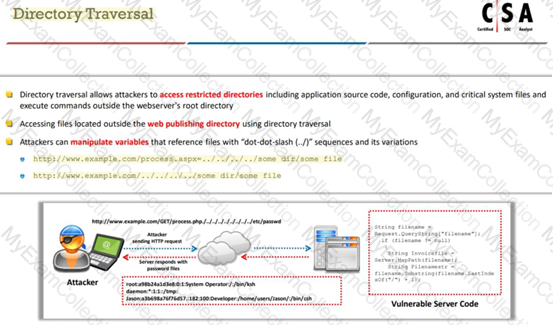
Identify the attack when an attacker by several trial and error can read the contents of a password file present in the restricted etc folder just by manipulating the URL in the browser as shown:
http://www.terabytes.com/process.php./../../../../etc/passwd
Identify the type of attack, an attacker is attempting on www.example.com website.
Which of the following formula is used to calculate the EPS of the organization?
Wesley is an incident handler in a company named Maddison Tech. One day, he was learning techniques for eradicating the insecure deserialization attacks.
What among the following should Wesley avoid from considering?
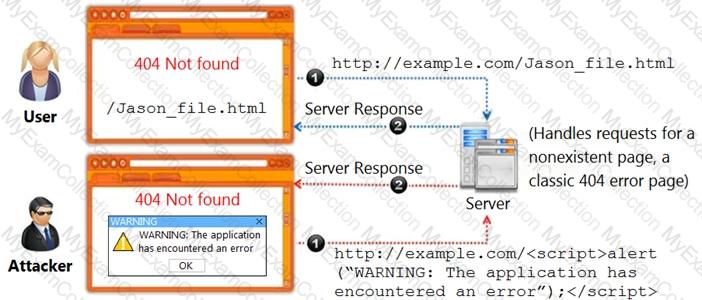
An attacker, in an attempt to exploit the vulnerability in the dynamically generated welcome page, inserted code at the end of the company’s URL as follows:
http://technosoft.com.com/ . Identify the attack demonstrated in the above scenario.