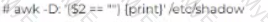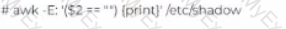Which type of training can create awareness among employees regarding compliance issues?
Clement is the CEO of an IT firm. He wants to implement a policy allowing employees with a preapproved set of devices from which the employees choose devices (laptops, smartphones, and tablets) to access company data as per the organization's access privileges. Which among the following policies does Clement want to enforce?
Wallcot, a retail chain in US and Canada, wants to improve the security of their administration
offices. They want to implement a mechanism with two doors. Only one of the doors can be opened at a
time. Once people enter from the first door, they have to be authorized to open the next one. Failing
the authorization, the person will be locked between the doors until an authorized person lets him or
her out. What is such a mechanism called?
An US-based organization decided to implement a RAID storage technology for their data backup plan. John wants to setup a RAID level that require a minimum of six drives but will meet high fault tolerance and with a
high speed for the data read and write operations. What RAID level is John considering to meet this requirement?
The CEO of Max Rager wants to send a confidential message regarding the new formula for its coveted soft drink, SuperMax, to its manufacturer in Texas. However, he fears the message could be altered in
transit. How can he prevent this incident from happening and what element of the message ensures the success of this method?
Alex is administrating the firewall in the organization's network. What command will he use to check the ports applications open?
An organization’s web server was recently compromised triggering its admin team into action to
defend the network. The admin team wants to place the web server in such a way that, even if it is
attacked, the other network resources will be unavailable to the attacker. Moreover, the network
monitoring will easily detect the future attacks. How can the admin team implement this plan?
Will is working as a Network Administrator. Management wants to maintain a backup of all the company data as soon as it starts operations. They decided to use a RAID backup storage technology for their data backup
plan. To implement the RAID data backup storage, Will sets up a pair of RAID disks so that all the data written to one disk is copied automatically to the other disk as well. This maintains an additional copy of the data.
Which RAID level is used here?
Sean has built a site-to-site VPN architecture between the head office and the branch office of his company. When users in the branch office and head office try to communicate with each other, the traffic is
encapsulated. As the traffic passes though the gateway, it is encapsulated again. The header and payload both are encapsulated. This second encapsulation occurs only in the __________implementation of a VPN.
Dan and Alex are business partners working together. Their Business-Partner Policy states that they should encrypt their emails before sending to each other. How will they ensure the authenticity of their emails?
An IDS or IDPS can be deployed in two modes. Which deployment mode allows the IDS to both
detect and stop malicious traffic?
Blake is working on the company's updated disaster and business continuity plan. The last section of the plan covers computer and data incidence response. Blake is outlining the level of severity for each type of
incident in the plan. Unsuccessful scans and probes are at what severity level?
Which among the following is used to limit the number of cmdlets or administrative privileges of administrator, user, or service accounts?
As a network administrator, you have implemented WPA2 encryption in your corporate wireless network. The WPA2's_________integrity check mechanism provides security against a replay attack
Henry needs to design a backup strategy for the organization with no service level downtime. Which backup method will he select?
Fred is a network technician working for Johnson Services, a temporary employment agency in Boston. Johnson Services has three remote offices in New England and the headquarters in Boston where Fred works.
The company relies on a number of customized applications to perform daily tasks and unfortunately these applications require users to be local administrators. Because of this, Fred's supervisor wants to implement
tighter security measures in other areas to compensate for the inherent risks in making those users local admins. Fred's boss wants a solution that will be placed on all computers throughout the company and
monitored by Fred. This solution will gather information on all network traffic to and from the local computers without actually affecting the traffic. What type of solution does Fred's boss want to implement?
John wants to implement a firewall service that works at the session layer of the OSI model. The firewall must also have the ability to hide the private network information. Which type of firewall service is John thinking of
implementing?
How can organizations obtain information about threats through human intelligence?
George was conducting a recovery drill test as a part of his network operation. Recovery drill tests are conducted on the______________.
In Public Key Infrastructure (PKI), which authority is responsible for issuing and verifying the certificates?
A network designer needs to submit a proposal for a company, which has just published a web
portal for its clients on the internet. Such a server needs to be isolated from the internal network,
placing itself in a DMZ. Faced with this need, the designer will present a proposal for a firewall with
three interfaces, one for the internet network, another for the DMZ server farm and another for the
internal network. What kind of topology will the designer propose?
Byron, a new network administrator at FBI, would like to ensure that Windows PCs there are up-to-date and have less internal security flaws. What can he do?
_______________ is a structured and continuous process which integrates information security
and risk management activities into the system development life cycle (SDLC).
Which type of wireless network attack is characterized by an attacker using a high gain amplifier from a nearby location to drown out the legitimate access point signal?
According to standard loT security practice, loT Gateway should be connected to a -------------
Which of the following manages the Docker images, containers, networks, and storage volume and processes the request of Docker API?
Based on which of the following registry key, the Windows Event log audit configurations are recorded?
Which of the following includes examining the probability, impact status, and exposure of risk?
Patrick wants to change the file permission of a file with permission value 755 to 744. He used a Linux command chmod [permission Value] [File Name] to make these changes. What will be the change
in the file access?
Which firewall technology can filler application-specific commands such as CET and POST requests?
Which of the following filters car be applied to detect an ICMP ping sweep attempt using Wireshark?
Harry has sued the company claiming they made his personal information public on a social networking site in the United States. The company denies the allegations and consulted a/an _______ for legal
advice to defend them against this allegation.
John is a network administrator and is monitoring his network traffic with the help of Wireshark. He suspects that someone from outside is making a TCP OS fingerprinting attempt on his organization's network. Which
of the following Wireshark filter(s) will he use to locate the TCP OS fingerprinting attempt?
Which of the following intrusion detection techniques observes the network for abnormal usage patterns by determining the performance parameters for regular activities and monitoring for actions
beyond the normal parameters?
Harry has successfully completed the vulnerability scanning process and found serious vulnerabilities exist in the organization's network. Identify the vulnerability management phases through which he will proceed to
ensure all the detected vulnerabilities are addressed and eradicated. (Select all that apply)
If a network is at risk from unskilled individuals, what type of threat is this?
Which wireless networking topology setup requires same channel name and SSID?
Which of the following is consumed into SIEM solutions to take control of chaos, gain in-depth knowledge of threats, eliminate false positives, and implement proactive intelligence-driven defense?
Fargo, head of network defense at Globadyne Tech, has discovered an undesirable process in several Linux systems, which causes machines to hang every 1 hour. Fargo would like to eliminate it; what
command should he execute?
Bryson is the IT manager and sole IT employee working for a federal agency in California. The agency was just given a grant and was able to hire on 30 more employees for a new extended project. Because of this,
Bryson has hired on two more IT employees to train up and work. Both of his new hires are straight out of college and do not have any practical IT experience. Bryson has spent the last two weeks teaching the new
employees the basics of computers, networking, troubleshooting techniques etc. To see how these two new hires are doing, he asks them at what layer of the OSI model do Network Interface Cards (NIC) work on. What
should the new employees answer?
Which of the following refers to the clues, artifacts, or evidence that indicate a potential intrusion or malicious activity in an organization's infrastructure?
Which of the following examines Recovery Point Objectives (RPOs) and Recovery Time Objectives (RTOs) for a disaster recovery strategy?
Who oversees all the incident response activities in an organization and is responsible for all actions of the IR team and IR function?
An enterprise recently moved to a new office and the new neighborhood is a little risky. The CEO wants to monitor the physical perimeter and the entrance doors 24 hours. What is the best option to do this job?
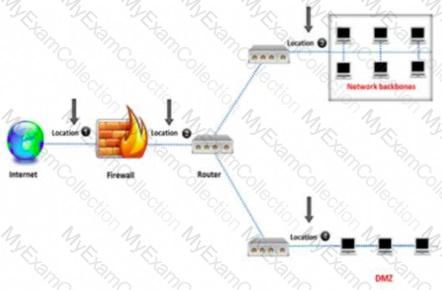
An administrator wants to monitor and inspect large amounts of traffic and detect unauthorized attempts from inside the organization, with the help of an IDS. They are not able to
recognize the exact location to deploy the IDS sensor. Can you help him spot the location where the IDS sensor should be placed?
Phishing-like attempts that present users a fake usage bill of the cloud provider is an example of a:
Which of the following information security standards defines security policies, technologies and ongoing processes for organizations that handle cardholder information for debit, credit, prepaid, epurse, ATM, and POS cards?
Sophie has been working as a Windows network administrator at an MNC over the past 7 years. She wants to check whether SMB1 is enabled or disabled. Which of the following command allows Sophie
to do so?
Which of the following Event Correlation Approach checks and compares all the fields systematically and intentionally for positive and negative correlation with each other to determine the correlation across one or
multiple fields?
Blake is working on the company's updated disaster and business continuity plan. The last section of the plan covers computer and data incidence response. Blake is outlining the level of severity for each type of
incident in the plan. Unsuccessful scans and probes are at what severity level?
In what type of IoT communication model do devices interact with each other through the internet, primarily using protocols such as ZigBee, Z-Wave, or Bluetooth?
Which of the following things need to be identified during attack surface visualization?
Arman transferred some money to his friend’s account using a net banking service. After a few hours, his friend informed him that he hadn’t received the money yet. Arman logged on to the bank’s website to investigate and discovered that the amount had been transferred to an unknown account instead. The bank, upon receiving Arman’s complaint, discovered that someone had established a station between Arman’s and the bank server’s communication system. The station intercepted the communication and inserted another account number replacing his friend’s account number. What is
such an attack called?
Which type of attack is used to hack an IoT device and direct large amounts of network traffic toward a web server, resulting in overloading the server with connections and preventing any new connections?
Which of the following VPN topologies establishes a persistent connection between an organization's main office and its branch offices using a third-party network or the Internet?
You want to increase your network security implementing a technology that only allows certain MAC addresses in specific ports in the switches; which one of the above is the best choice?
Your company is planning to use an uninterruptible power supply (UPS) to avoid damage from power fluctuations. As a network administrator, you need to suggest an appropriate UPS solution suitable for specific resources or conditions. Match the type of UPS with the use and advantage:
Hacktivists are threat actors, who can be described as -------------------
A stateful multilayer inspection firewall combines the aspects of Application level gateway, Circuit level gateway and Packet filtering firewall. On which layers of the OSI model, does the Stateful
multilayer inspection firewall works?
An insider in Hexagon, a leading IT company in USA, was testing a packet crafting tool. This tool
generated a lot of malformed TCP/IP packets which crashed the main server’s operating system leading
to restricting the employees’ accesses. Which attack did the insider use in the above situation?
Which type of antenna is based on the principle of a satellite dish and can pick up Wi-Fi signals from a distance of ten miles of more?
------------is a group of broadband wireless communications standards for Metropolitan Area Networks (MANs)
Identify the virtualization level that creates a massive pool of storage areas for different virtual machines running on the hardware.
Which of the following technologies can be used to leverage zero-trust model security?
The company has implemented a backup plan. James is working as a network administrator for the company and is taking full backups of the data every time a backup is initiated. Alex who is a senior security manager
talks to him about using a differential backup instead and asks him to implement this once a full backup of the data is completed. What is/are the reason(s) Alex is suggesting that James use a differential backup?
(Select all that apply)
Simon had all his systems administrators implement hardware and software firewalls to ensure network security. They implemented IDS/IPS systems throughout the network to check for and stop any unauthorized
traffic that may attempt to enter. Although Simon and his administrators believed they were secure, a hacker group was able to get into the network and modify files hosted on the company's website. After searching
through the firewall and server logs, no one could find how the attackers were able to get in. He decides that the entire network needs to be monitored for critical and essential file changes. This monitoring tool alerts
administrators when a critical file is altered. What tool could Simon and his administrators implement to accomplish this?
Jason works as a System Administrator for www.company.com Inc. The company has a Windows
based network. Sam, an employee of the company, accidentally changes some of the applications and
system settings. He complains to Jason that his system is not working properly. To troubleshoot the
problem, Jason diagnoses the internals of his computer and observes that some changes have been
made in Sam's computer registry. To rectify the issue, Jason has to restore the registry. Which of the
following utilities can Jason use to accomplish the task? Each correct answer represents a complete
solution. Choose all that apply.
Which of the following statements holds true in terms of virtual machines?
Syslog and SNMP are the two main _______ protocols through which log records are transferred.
Stephanie is currently setting up email security so all company data is secured when passed through email. Stephanie first sets up encryption to make sure that a specific user's email is protected. Next, she needs to
ensure that the incoming and the outgoing mail has not been modified or altered using digital signatures. What is Stephanie working on?
Jeanne is working as a network administrator in an IT company. She wants to control/limit container
access to CPU, memory, swap, block IO (rates), network. Which Linux kernel feature allows Jeanne to
manage, restrict, and audit groups of the process?
Steven's company has recently grown from 5 employees to over 50. Every workstation has a public IP address and navigated to the Internet with little to no protection. Steven wants to use a firewall. He also wants IP
addresses to be private addresses, to prevent public Internet devices direct access to them. What should Steven implement on the firewall to ensure this happens?
Ross manages 30 employees and only 25 computers in the organization. The network the company uses is a peer-to-peer. Ross configures access control measures allowing the employees to set their own control
measures for their files and folders. Which access control did Ross implement?
An organization needs to adhere to the______________rules for safeguarding and protecting the electronically stored health information of employees.
Which of the following DDoS attacks overloads a service by sending inundate packets?
Which subdirectory in /var/log directory stores information related to Apache web server?
Identify the network topology where each computer acts as a repeater and the data passes from one computer to the other in a single direction until it reaches the destination.
Which type of information security policy addresses the implementation and configuration of technology and user behavior?
Andrew would like to configure IPsec in a manner that provides confidentiality for the content of packets. What component of IPsec provides this capability?
You are responsible for network functions and logical security throughout the corporation. Your company has over 250 servers running Windows Server 2012, 5000 workstations running Windows 10, and 200 mobile
users working from laptops on Windows 8. Last week 10 of your company's laptops were stolen from a salesman, while at a conference in Barcelona. These laptops contained proprietary company information. While
doing a damage assessment, a news story leaks about a blog post containing information about the stolen laptops and the sensitive information. What built-in Windows feature could you have implemented to protect the
sensitive information on these laptops?
You are using Wireshark to monitor your network traffic and you see a lot of packages with FIN,
PUSH and URG flags activated; what can you infer about this behavior?
Which firewall technology provides the best of both packet filtering and application-based filtering and is used in Cisco Adaptive Security Appliances?
Timothy works as a network administrator in a multinational organization. He decides to implement a dedicated network for sharing storage resources. He uses a_______as it seperates the storage units from the
servers and the user network.
Which of the following indicators are discovered through an attacker's intent, their end goal or purpose, and a series of actions that they must take before being able to successfully launch an attack?
A VPN Concentrator acts as a bidirectional tunnel endpoint among host machines. What are the other f unction(s) of the device? (Select all that apply)
Which of the following interfaces uses hot plugging technique to replace computer components without the need to shut down the system?
A local bank wants to protect their cardholder data. Which standard should the bark comply with in order to ensure security of this data?
Identify the attack where an attacker manipulates or tricks people into revealing their confidential details like bank account information, credit card details, etc.?
What is the name of the authority that verifies the certificate authority in digital certificates?
Implementing access control mechanisms, such as a firewall, to protect the network is an example of which of the following network defense approach?
Which of the following standards does a cloud service provider has to comply with, to protect the privacy of its customer’s personal information?
Damian is the chief security officer of Enigma Electronics. To block intruders and prevent any environmental accidents, he needs to set a two-factor authenticated keypad lock at the entrance, rig a fire
suppression system, and link any video cameras at various corridors to view the feeds in the surveillance room. What layer of network defense-in-depth strategy is he trying to follow?
An attacker uses different types of password cracking techniques to crack the password and gain unauthorized access to a system. An attacker uses a file containing a list of commonly used passwords. They then
upload this file into the cracking application that runs against the user accounts. Which of the following password cracking techniques is the attacker trying?
John has been working a* a network administrator at an IT company. He wants to prevent misuse of accounts by unauthorized users. He wants to ensure that no accounts have empty passwords. Which of the following commands does John use to list all the accounts with an empty password?
Geon Solutions INC., had only 10 employees when it started. But as business grew, the organization had to increase the amount of staff. The network administrator is finding it difficult to accommodate an increasing
number of employees in the existing network topology. So the organization is planning to implement a new topology where it will be easy to accommodate an increasing number of employees. Which network topology
will help the administrator solve the problem of needing to add new employees and expand?
John has implemented________in the network to restrict the limit of public IP addresses in his organization and to enhance the firewall filtering technique.
Malone is finishing up his incident handling plan for IT before giving it to his boss for review. He is outlining the incident response methodology and the steps that are involved. Which step should Malone list as the last step in the incident response methodology?
David is working in a mid-sized IT company. Management asks him to suggest a framework that can be used effectively to align the IT goals to the business goals of the company. David suggests the______framework,
as it provides a set of controls over IT and consolidates them to form a framework.