An LTM Specialist needs to create two virtual servers.
The application has links for both HTTP and HTTPS version of application. The client must be persistence to a pool member, no matter which virtual server is accessed.
What must be selected in the Source Address Affinity persistence profile?
Refer to the exhibit

Given the bigip conf extract shown where the servers only talk http on port 80, which node will receive the next user request?
A new iRule needs to be tested. The LTM Specialist needs to measure page load times and monitor potential changes in memory usage A load test is scheduled.
Which two features should the LTM Specialist use to monitor these requirements? (Choose two.)
An LTM specialist needs to upgrade a VCMP quest in an HA Setup with minimum interruption for all VCMP guest instances.
In which should the LTM Specialist perform this upgrade?
An LTM Specialist is configuring a new virtual server on an LTM device and assigning a SNAT pool that is already is use another virtual server. Both virtual servers use the same pool members to load balance traffic. A maximum of 35,000 users needs to be able to access each virtual server ta any time. The network architecture does NOT allow the backend servers to use the LTM device as a default gateway.
What is the minimum number of SNAT addresses required in the SNAT pool to meet the needs of the virtual servers?
An LTM Specialist needs to load balance an application using an LTM device to meet the requirements:
The application servers do NOT Support SSL, but client access to the application should be secured.
Multiple requests from the same client should be sent to the same pool member.
All pool members will have roughly the same processing power, and traffic should be distributed evenly.
The LTM device is NOT the pool members' default gateway.
which configuration should the LTM Specialist.
A design requires the LTM device to become HA standby when the one of the two physical interface on the External trunk is down the External trunk is an interface on the External VLAN
Which TMOS command enables this behavior?
An LTM Specialist regularly provides analytics reports that show that traffic generated by different subnets within the organization. The LTM Specialist needs show the associate department names next the IP addresses in the reports.
Which step should the LTM Specialist take to meet this requirement?
An LTM Specialist has trouble with SNMP traps in the management network The ITM Specialist takes the network capture shown to troubleshoot:

What should the UM Specialist change to capture packets related to this workflow?
Exhibit.

An LTM Specialist needs to configure VS^HTTP and VS_DB for an online shopping site. The VS HTTP passes the client requests to the webservers. The webservers query the database servers through the VS_DB. Initially, the LTM Specialist finds the database servers directly return the packets to the webservers.
which setting must be enabled for the configuration to function correctly?
Exhibit.

The three VLANS shown provide connectivity to backend servers. The backend servers are being moved to unmanaged switches and require separate interfaces.
How should the F5 device interfaces be configured?
A VCMP guest has the following characteristics:
• Resources allocated for CPU memory, network interfaces, and disk space
• Virtual disk created
• The guest is NOT running
The guest is NOT running in which state is the VCMP guest
A new HITP server has been deployed on an LTM device. The application running on the server must be monitored by the LIM device. The following is required:
A new HITP server has been deployed on an LTM device. The application running on the server must be monitored by the LIM device. The following is required:
When the server is unavailable, it will send an HTTP status code of 200 in response to a request for the status html page.
When the server is available. I will send and HTTP status code of 201 in response to a request for the status html page.
When the 200 status code is received, the pool member should receive No new connections.
Which configuration change should be made to meet these requirements?
RADIUS authentication has been configured on the LTM device. The default remote user access requirements are as shown:
- Read only access to the configuration Utility
- Access to TMOS shell
Which two items need to be configured in this situation? (Choose two)
An TLM Specialist needs to configure a virtual server to terminate SSL connection on the LTM device.
Cryptographic information must be re-authorized for SSL sessions that remain open for longer than 30 seconds.
Which settings should the LTM Specialist configure in the client SSL profile?
The network team has recently added a new syslog server with IP address 10.1.1.1.
Which command adds the new syslog entry on the F5 LTM device?
A)
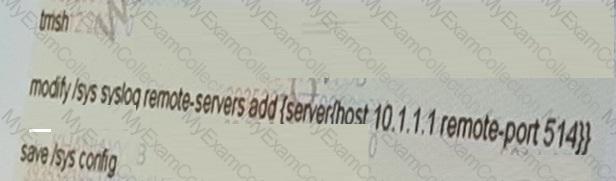
B)
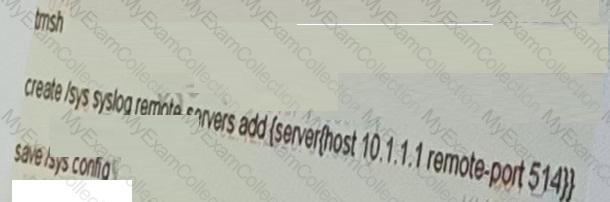
C)
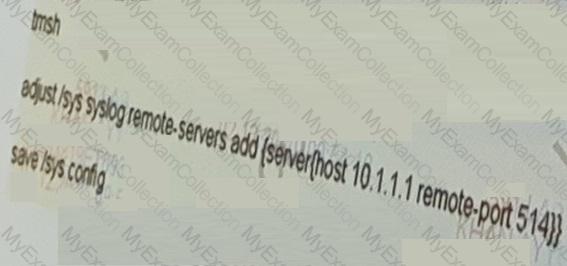
D)
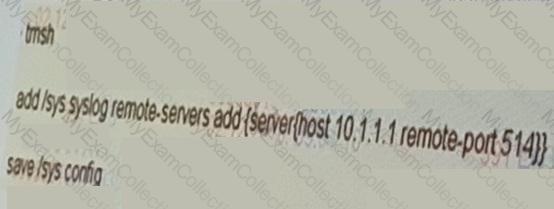
An LTM Specialist needs to create an iRule that creates persistence records based on a JSESSIONID cookie. If a persistence record already exists, then the iRule must persist the client connection according to the existing record.
Which persistence profile enables the iRule to meet these requirements?
AN LIM Specialist must upgrade the VCMP Guest active/standby LTM pair from version 11.3 to 11.5.3 on two VCMP Hosts.
where should the LTM Specialist import the latest 11.5.3 ISO images?
AN LTM Specialist is deploying an iRule designed to determine the country of origin of an incoming client connection. The iRule needs to be used with an SSL-enabled web application.
Which profile required for the iRule to function properly?

