Using the NX-API CLI JSON-RPC interface, which two Python data structure and requests call create an SVI? (Choose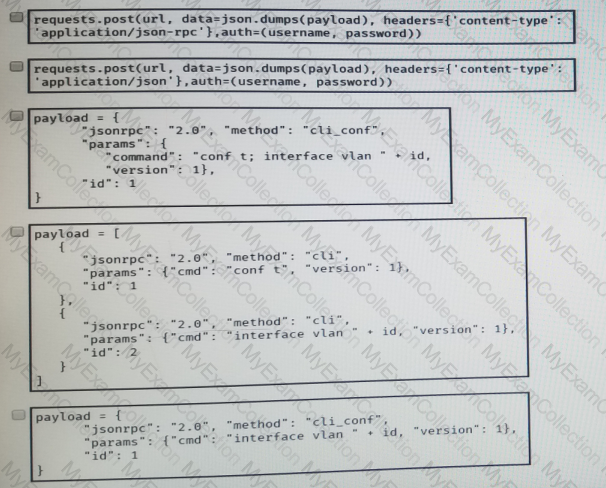
Which two bootstrap technologies are supported by Cisco NX-OS platforms? (Choose two )
Which authentication method is used when the REST API of the Cisco UCS Director is accessed?
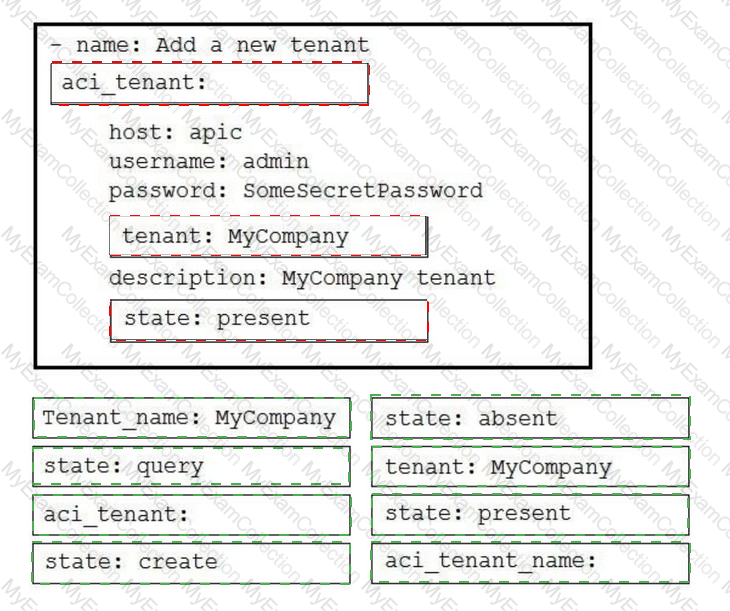
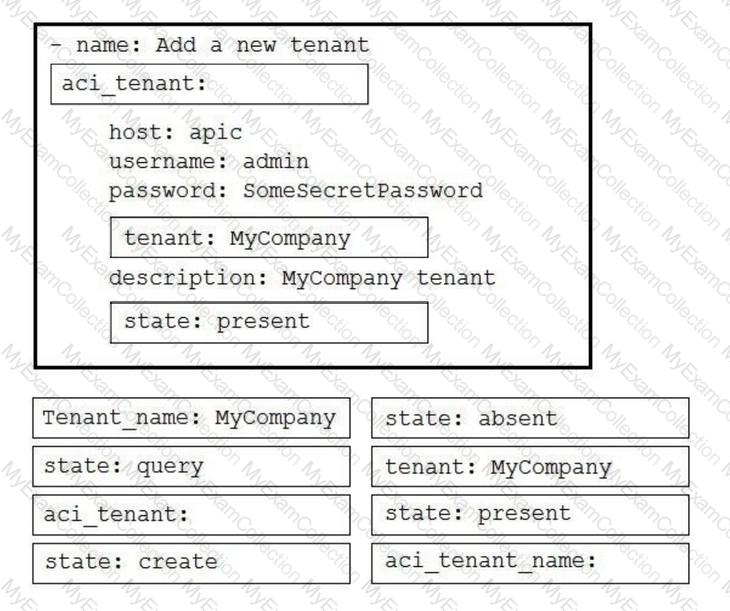
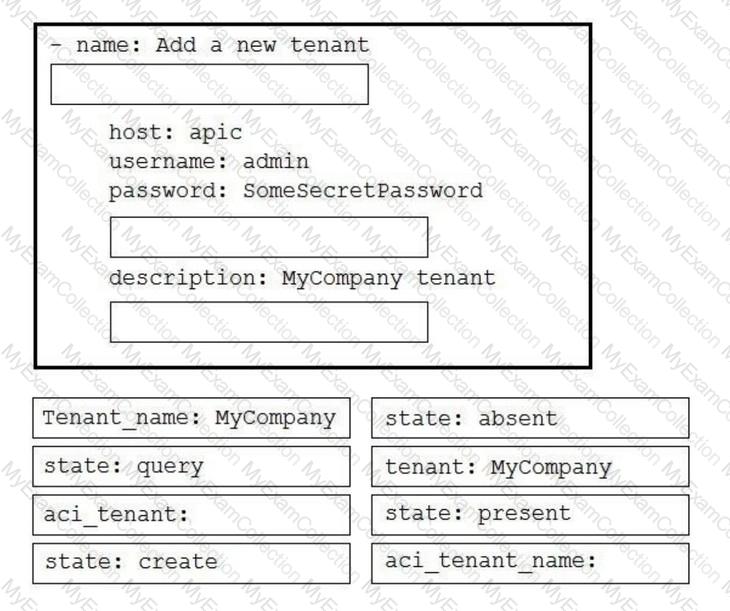
Drag and drop the code to complete an Ansible playbook that creates a new tenant. Not all options are used.
Which two benefits of using network configuration tools such as Ansible and Puppet to automate data center platforms are valid? (Choose two )
Refer to the Exhibit:
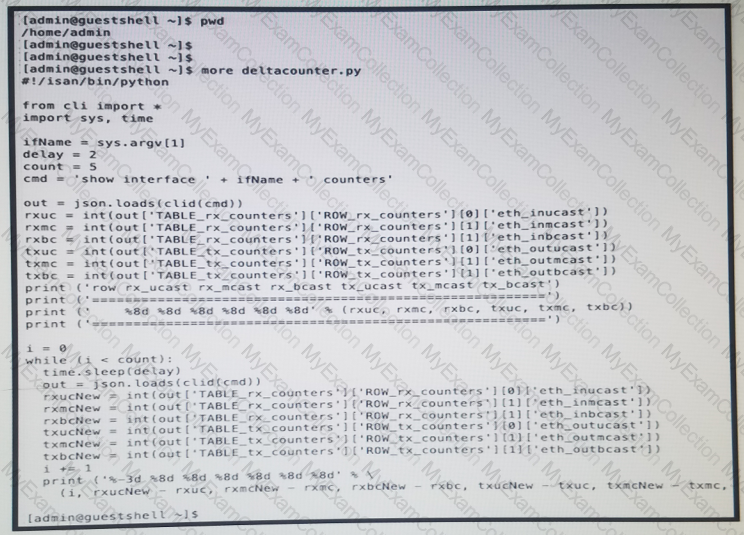
Refer to the exhibit: The script is called deltacounters.py and it is currently inside a Guest Shell container running inside a Cisco NX-OS switch.
Which Cisco NX-OS command results in a successful execution of this script?
An engineer is implementing a Cisco Nexus switch. Which command executes an Ansible playbook called n9k.yml?
Which two statements apply to authentication when using the Cisco Intersight API? (Choose two.)
When the Cisco bigmuddy-network-telematry-collector from GitHub is used, which command displays only the message headers?
Which two statements describe the authentication method used with Cisco Intersight REST API Requests? (Choose two.)
During the process of starting a Python network telemetry collector, which command starts the Cisco bigmuddy-network-telemetry-collector from GitHub?
A set of automation scripts work with no issue from a local machine, but an experiment needs to take place with a new package found online.
How is this new package isolated from the main code base?
When Cisco Nexus switches are implemented, which command requires the method key to perform a POST operation using the NXAPI-CLIJSON-RPC interface?
Which two application isolation options are available when Kubernetes is deployed with the ACI CNI plug-in? (Choose two.)
Which two initial actions should be taken when exploring automation capabilities for ACI? (Choose Two)
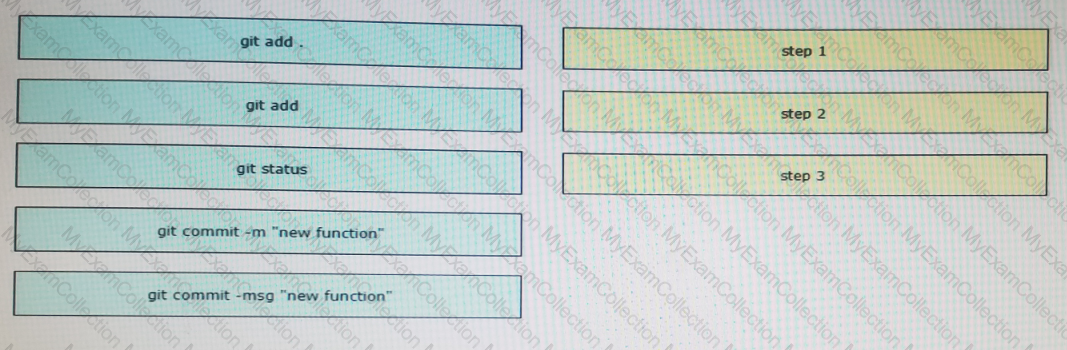
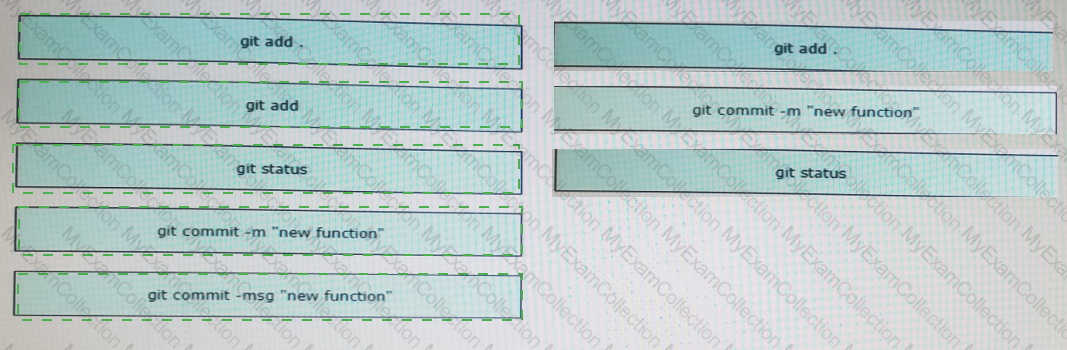
A file named myfunc.py has been edited. Drag and drop the steps from left that ensure that this file is committed to the local Git repository and verify its status into the correct order on the right. NOt all options are used.