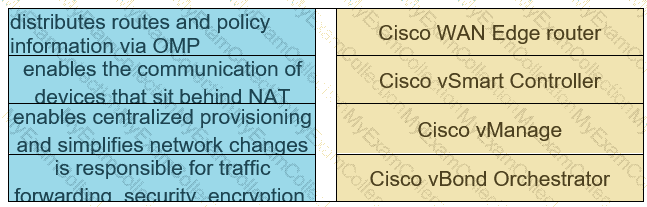
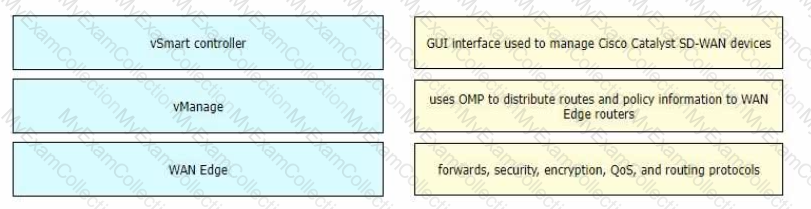
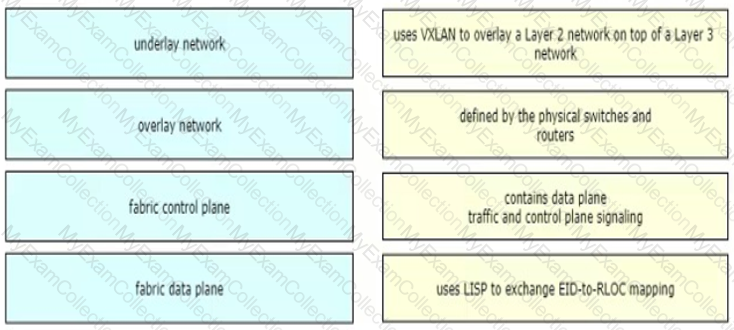
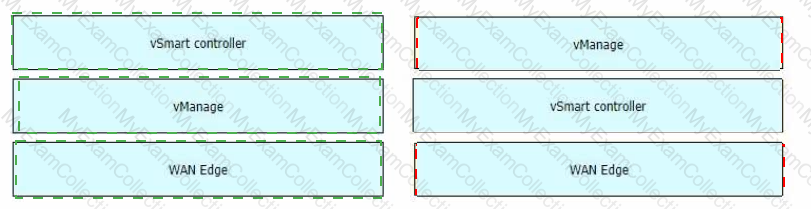
Drag and drop the Cisco SD-WAN components from the left onto their definitions on the right.
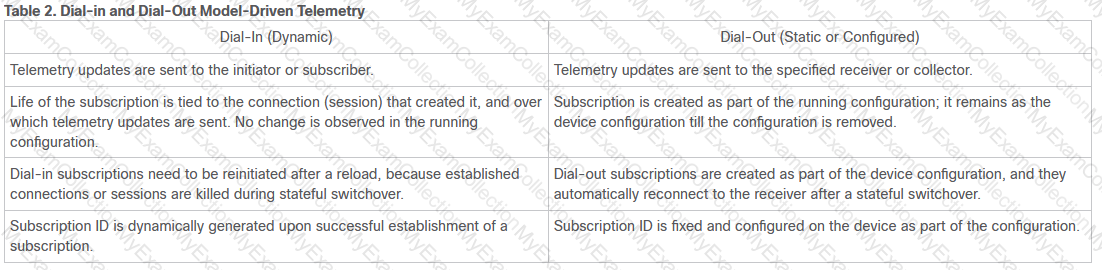
In an SD-WAN architecture, which methods are used to bootstrap a vEdge router?
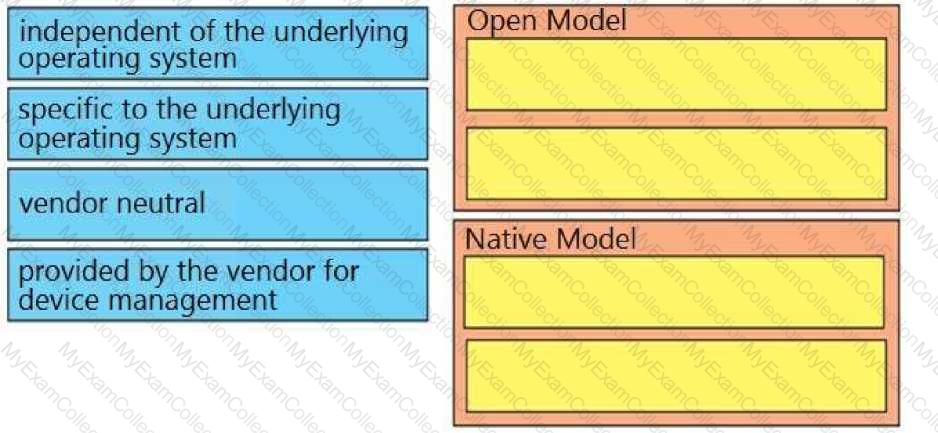
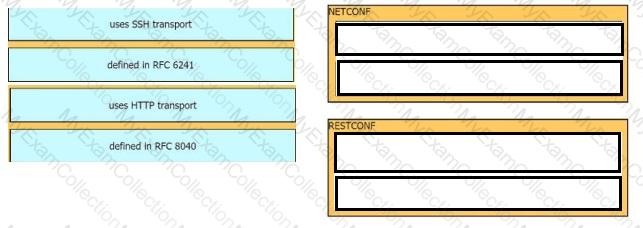
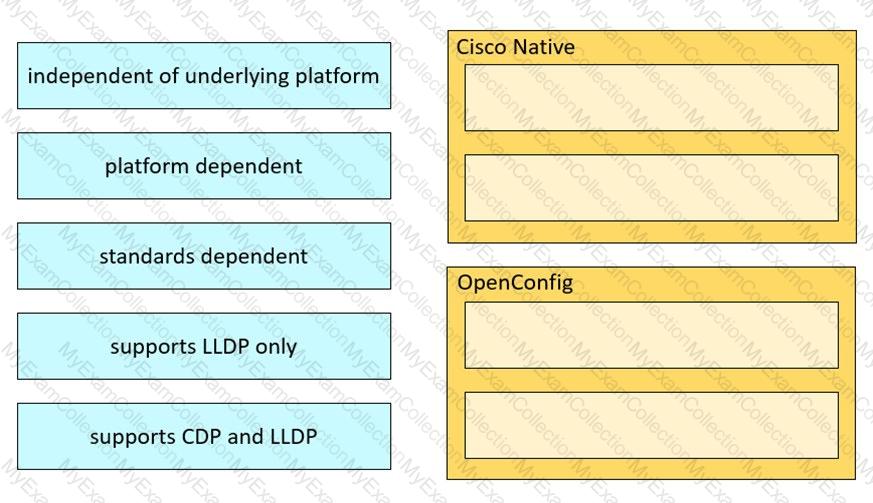
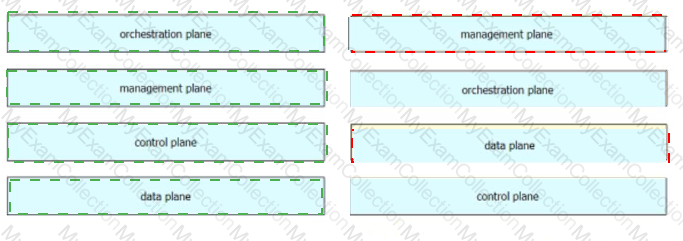
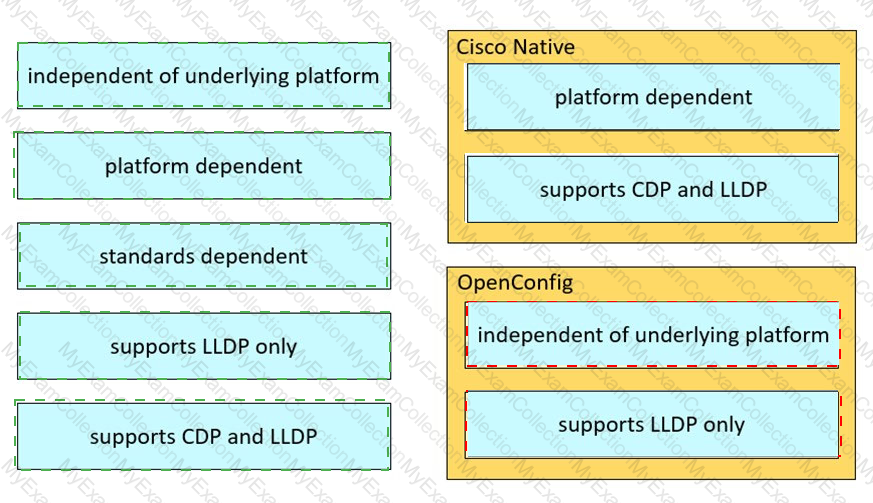
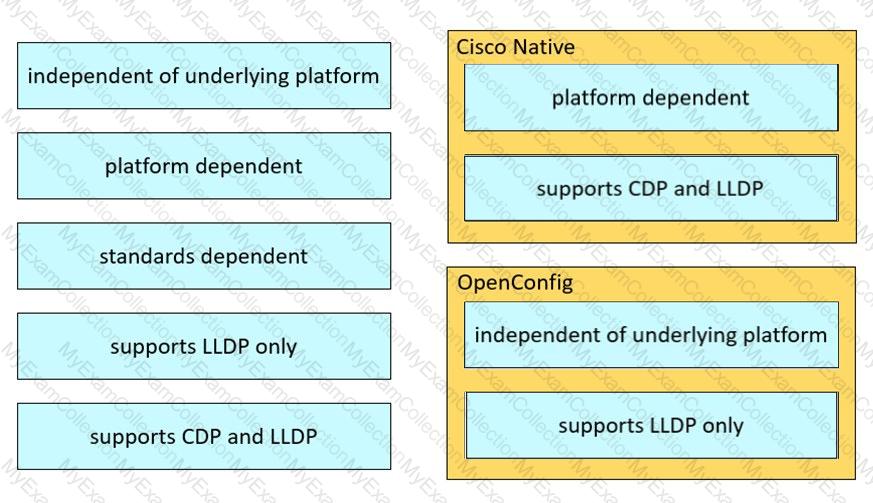
Drag and drop the characteristics from the left onto the Yang model they describe on the right.
Select and Place:
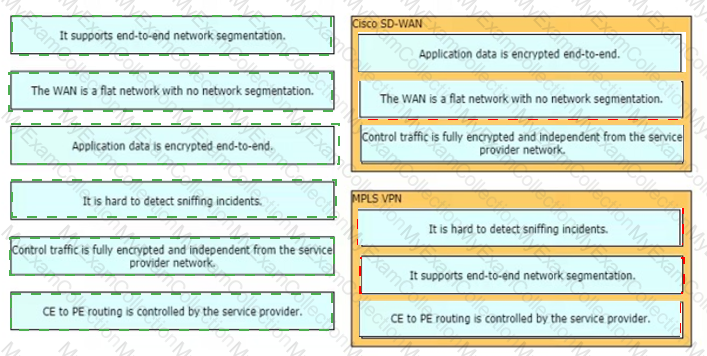
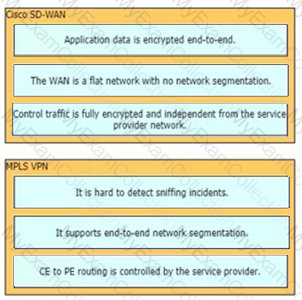
What are two characteristics of a migration from an IP-VPN service to a Cisco SD-WAN architecture? (Choose two.)
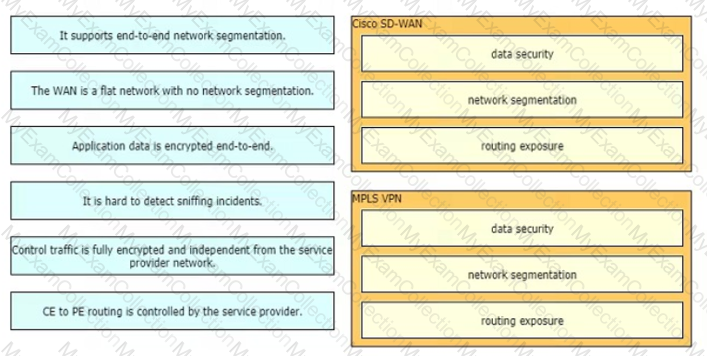
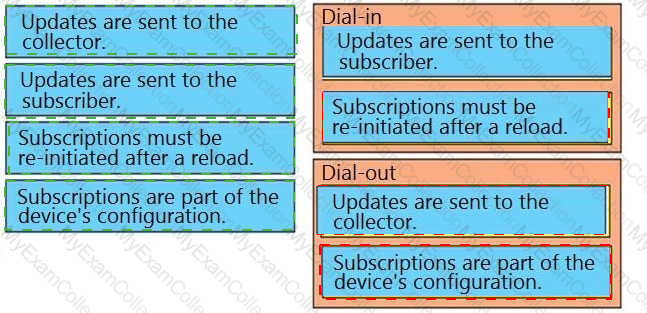
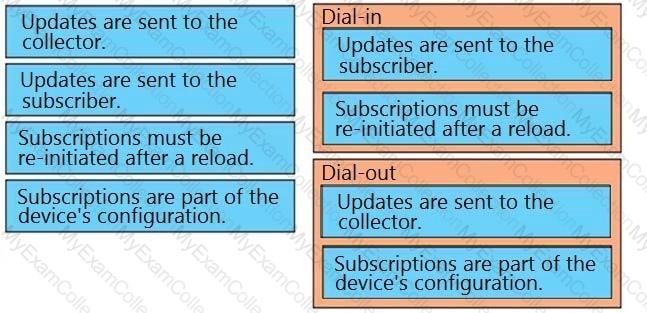
Drag and drop the description from the left onto the corresponding WAN connectivity types and categories on the right.
When expanding an existing Cisco SD-Access network, in addition to the control plane, which two device roles are needed to create an additional fabric site? (Choose two.)
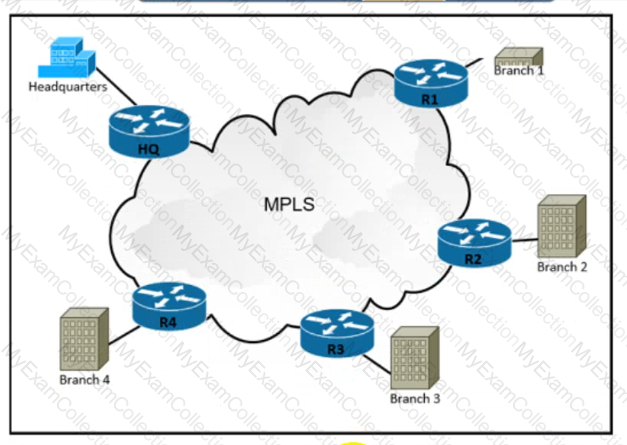
Refer to the exhibit. Currently, the network uses a single-homed solution for connecting to the internet. An engineer must design a more resilient WAN using the internet circuits at each site. The design must provide failover connectivity, support load-sharing of traffic, and QoS. Which solution must the engineer choose?
An architect is designing a multicast solution for a network that contains over 100 routers. The architect plans to create several multicast domains and balance the PIM-SM traffic within the network. Which technology should the architect include in the design?
Refer to the exhibit. An architect is developing a solution to consolidate networks while retaining device redundancy. The routing protocol for the WAN routers must be open standard, ensure high availability, and provide the fastest convergence time. Which solution must the design include?
Drag and drop the descriptions from the left onto the Cisco SD-WAN component they describe on the right.
Refer to the exhibit.
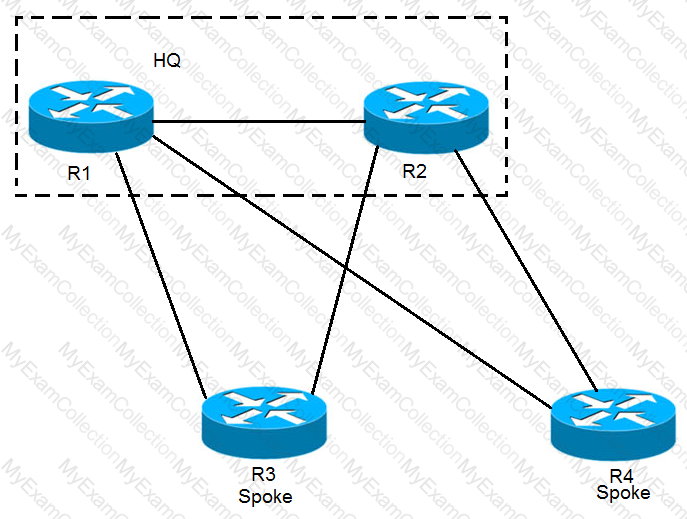
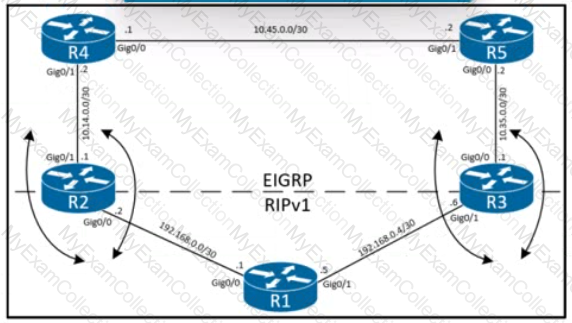
EIGRP has been configured on all links. The spoke nodes have been configured as EIGRP stubs, and the WAN links to R3 have higher bandwidth and lower delay than the links to R4. When a link failure occurs at the R1-R2 link, what happens to traffic on R1 that is destined for a subnet attached to R2?
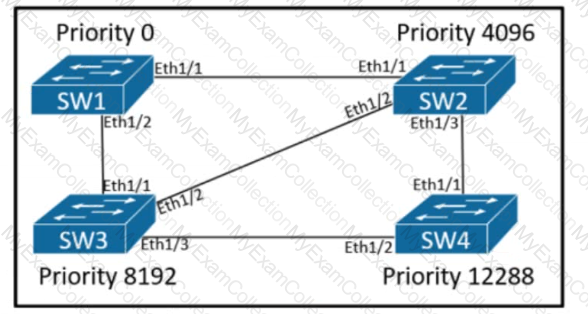
Refer to the exhibit. An engineer proposed this solution for a company that requires a loop-free. Layer 2 network design. The network will run 802.1W, and all links will be 1 Gbps. If all interfaces are up as point- to-point adjacencies, what are the expected port end states based on the design?
Refer to the exhibit.
C0FD9 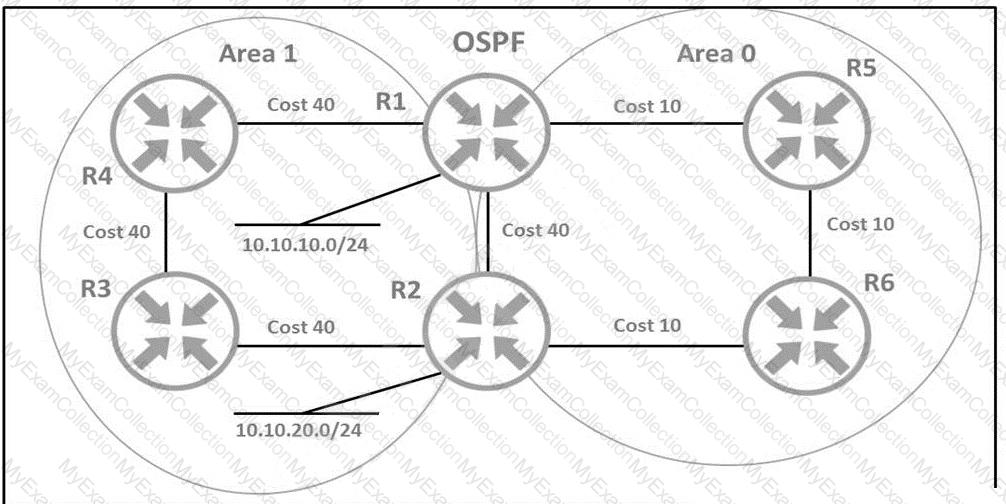 F48C9ACDC725EA850EC2476EE1E
F48C9ACDC725EA850EC2476EE1E
An architect must design a solution that uses the direct link between R1 and R2 for traffic from 10.10.10.0/24
toward network 10.10.20.0/24. Which solution should the architect include in the design?
Which component of Cisco SD-Access integrates with Cisco DNA Center to perform policy segmentation and enforcement through the use of security group access control lists and security group tags?
Which control-plane technology allows the same subnet to exist across multiple network locations?
Refer to the exhibit. A company has some offices that are connected via dark fiber in New York. A network architect must optimize the network design based on the EIGRP routing protocol. The network has hierarchical addressing between 10 and 12 routers in each office. Routing convergence time must be at the minimum. What must the network architect do to reduce the query range?
What is the purpose of a control plane node in a Cisco SD-Access network fabric?
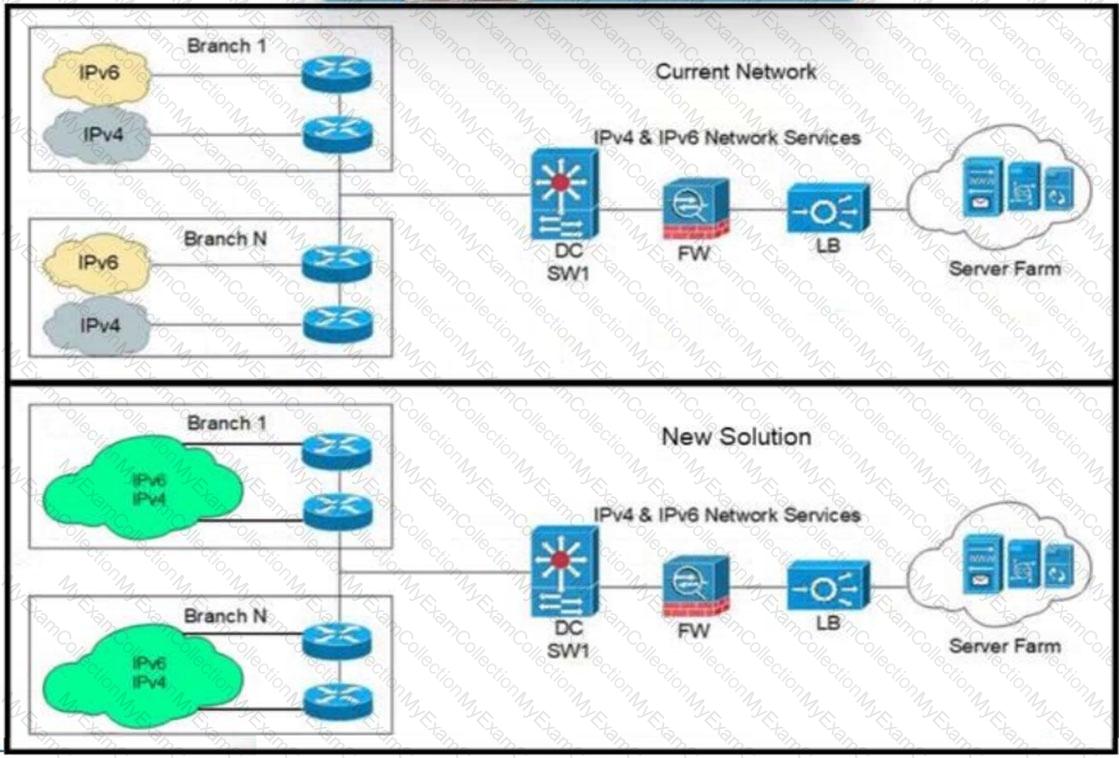
A company requested that an architect propose a new IPv4 and IPv6 deployment strategy. The company wants a solution that is straightforward, with no information hiding or forwarding overhead. Which solution meets these requirements?
A company is planning to open two new branches and allocate the 2a01:c30:16:7009::3800/118 IPv6 network for the region. Each branch should have the capacity to accommodate maximum of 200 hosts. Which two networks should the company use? (Choose two.)
An engineer must propose a solution for a campus network that includes the capability to create multiple Layer 3 virtual networks. Each network must have its own addressing structure and routing table for data forwarding. The solution must be scalable to support hundreds of virtual networks and allow simple configuration and management with minimal administrative overhead. Which solution does the engineer recommend?
A company uses cloud-based applications for voice and video calls, file sharing, content sharing, and messaging. During business hours, these applications randomly become slow and unresponsive. However, other applications work smoothly with the current applied QoS polices. Which solution must the company choose to resolve the issue?
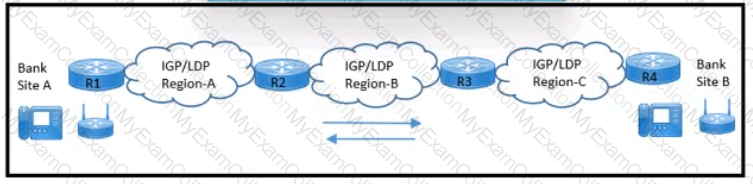
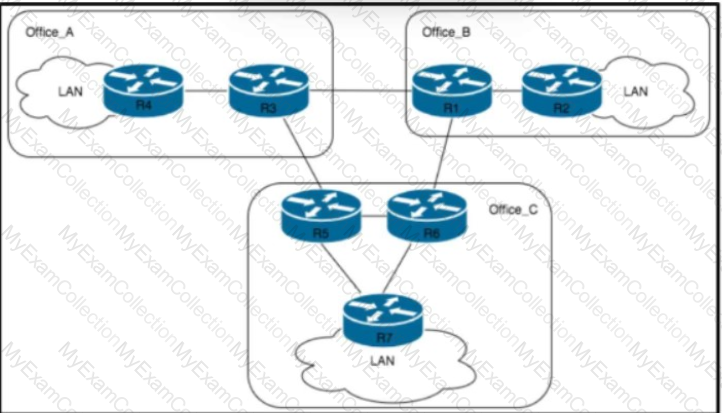
Refer to the exhibit. An architect must design a solution to connect bank site A with bank site B and support:
network operation center monitoring end-to-end L3VPN and L2VPN traffic
company adding thousands of routes in the next two years
Which two BGP solutions must the design include? (Choose two.)
A customer’s environment includes hosts that support IPv6-only. Several of these hosts must communicate with a public web server that has only IPv4 domain name resolution. Which solution should the customer use in this environment?
An enterprise customer has these requirements:
end-to-end QoS for the business-critical applications and VoIP services based on CoS marking.
flexibility to offer services such as IPv6 and multicast without any reliance on the service provider.
support for full-mesh connectivity at Layer 2.
Which WAN connectivity option meets these requirements?
At which layer does Cisco Express Forwarding use adjacency tables to populate addressing information?
In Cisco SD-Access. virtual networks create segmentation that allows for separation of users and resources. How is this type of segmentation described?
An engineer is designing a network for a customer running a wireless network with a common VLAN for all APs. The customer is experiencing unicast flooding in the Layer 2 network between the aggregation and access layers. The customer wants to reduce the flooding and improve convergence time. Which solution meets these requirements?
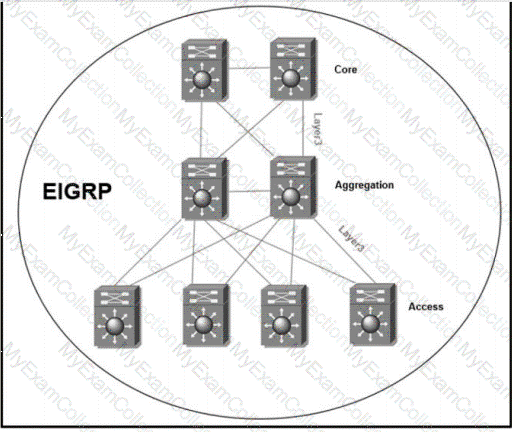
Refer to the exhibit. The full EIGRP routing table is advertised throughout the network. Currently, users experience data loss when any one link in the network fails. An architect optimizes the network to reduce the impact when a link fails. Which solution should the architect include in the design?
Which information update is carried by OMP and enables the Cisco SD-WAN to build a secure overlay fabric on top of any public or private transport without regard for the actual link IP?
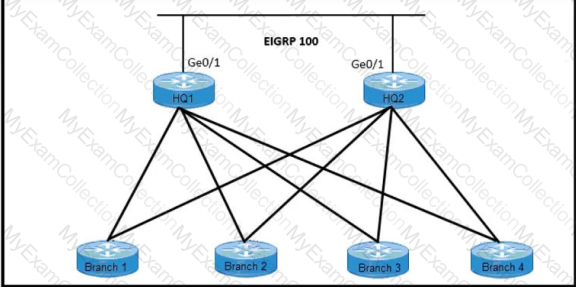
Refer to the exhibit. An architect must create a stable and scalable EIGRP solution for a customer. The design must:
•conserve bandwidth, memory, and CPU processing
•prevent suboptimal routing
•avoid any unnecessary queries
Which two solutions must the architect select? (Choose two.)
Drag and drop the Cisco Catalyst SD-WAN components from the left to their definitions on the nght
An engineer must design a scalable QoS architecture that allows the separation of the traffic into classes on predefined business requirements. The design must also utilize the differentiated services code points as the QoS priority descriptor value and support at least 10 levels of classification. Which QoS technology should the engineer include in the design?
Which type of rendezvous point deployment is standards-based and support dynamic RP discovery?
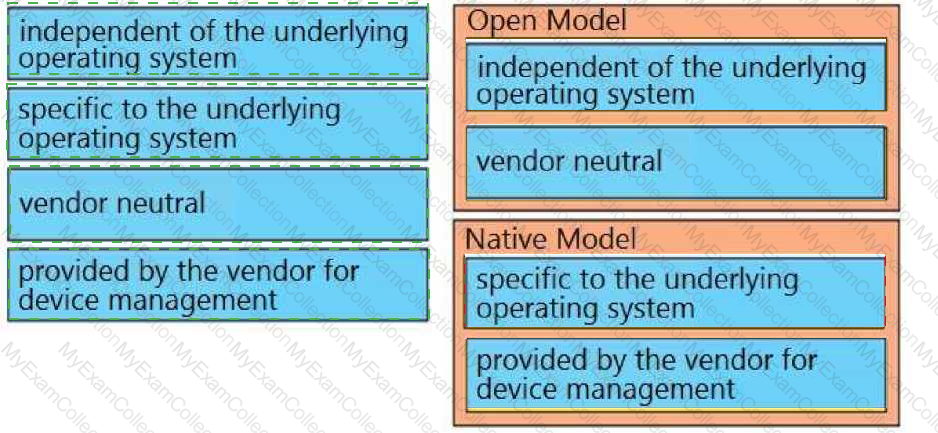
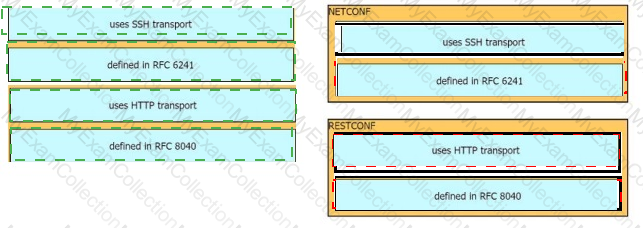
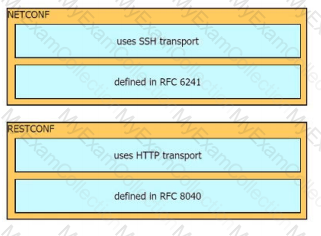
Drag and drop the characteristics from the left onto the configuration protocols they describe on the right.
Which control plane protocol is responsible for ElD-to-RLOC mapping concerning SO-Access Architecture?
Which two border nodes are available in the Cisco SD-Access architecture? (Choose two.)
A network solution is being designed for a company that connects to multiple Internet service providers. Which Cisco proprietary BGP path attribute will influence outbound traffic flow?
A customer plans to adopt distributed QoS in their enterprise WAN. The policy must allow for individual packet marking according to the type of treatment required and for forwarding based on hop-by-hop treatment locally defined on each device. Which technology must the customer select?
A company needs to increase access port capacity on one floor of a building. They want to leverage the existing catalyst access switch. There is no problem with uplink bandwidth capacity. However, no additional uplinks can be added because no ports are available on the distribution switches. Which solution must the company choose to provide additional access ports?
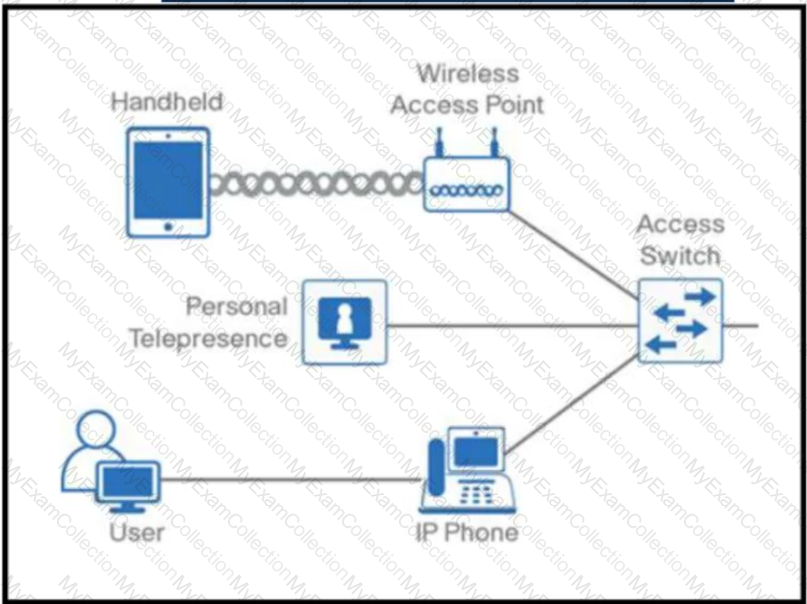
Refer to the exhibit. An architect with an employee ID: 4542:60:170 is designing a campus Layer 2 infrastructure. The design requires a PoE power budget that varies from 30-60 W. In addition, power must be provided continuously to some endpoints and must be supported even during the reloading of edge switches. Which solution must the architect select?
An engineer must design an in-band management solution for a customer with branch sites. The solution must allow remote management of the branch sites using management protocols over an MPLS WAN. Queueing is implemented at the remote sites using these classes:

How must the solution prioritize the management traffic over the WAN?
An engineer is tasked with designing a dual BGP peering solution with a service provider. The design must meet these conditions:
The routers will not learn any prefix with a subnet mask greater than /24.
The routers will determine the routes to include in the routing table based on the length of the mask alone.
The routers will make this selection regardless of the service provider configuration.
Which solution should the engineer include in the design?
An enterprise needs to enhance its WAN availability after a recent outage with its only MPLS provider. The proposed solution must have a quick deployment, be affordable, be reliable, and work as a backup for the enterprise's primary MPLS connection. Which solution meets these requirements?
An engineer must design a VPN solution for a company that has multiple branches connecting to a main office. What are two advantages of using DMVPN instead of IPsec tunnels to accomplish this task? (Choose
two.)
An engineer is designing a QoS solution for a customer The customer's internet connection has a bandwidth of 10 Mbps. The design must ensure that traffic bursts of data do not exceed the bandwidth of the connection and that received traffic does not starve out business-critical traffic Which solution must the engineer choose?
A company’s branch location uses redundant routers and links for connectivity to the headquarters. Also, to use the entire available bandwidth, the branch uses a dynamic routing protocol. An architect must design a multicast streaming solution to avoid RPF check failures because of the current network design. Which deployment model must the architect choose?
An engineer is working with NETCONF and Cisco NX-OS based devices. The engineer needs a YANG model that supports a specific feature relevant only to Cisco NX-OS. Which model must the engineer choose?
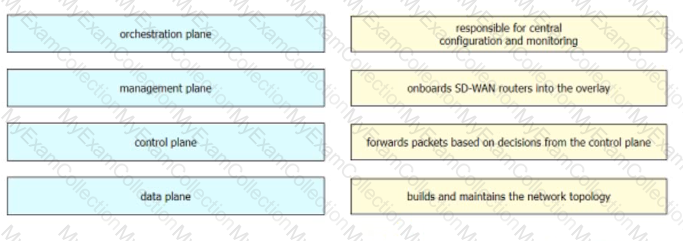
Which two functions are provided by the Cisco SD-WAN orchestration plane? (Choose two.)
A network engineer must design a multicast solution to prevent the spoofing of multicast streams and ensure efficient bandwidth utilization. The network will be merged with another multicast domain in the future, and the merge must require minimum effort. Which two solutions meet the customer requirements? (Choose two.)
Which two functions does the control plane node provide in a Cisco SD-Access architecture? (Choose two.)
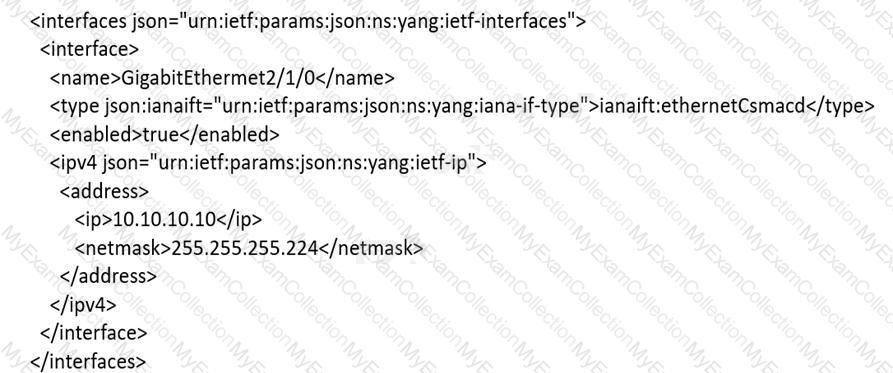
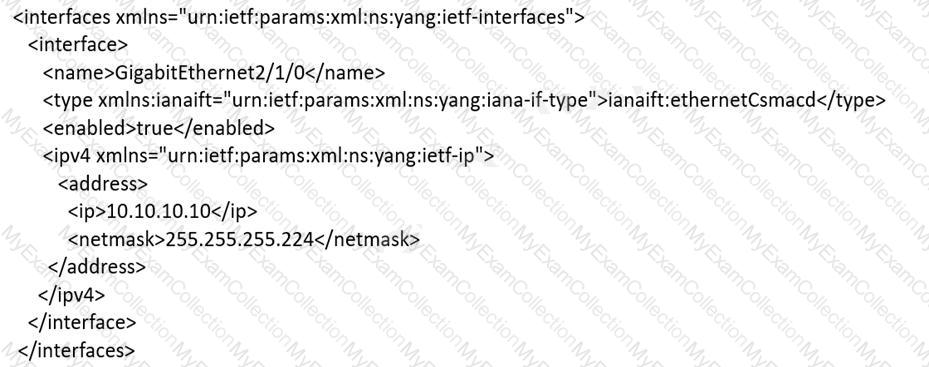
An engineer must use YANG with an XML representation to configure a Cisco IOS XE switch with these specifications:
IP address 10.10.10.10/27 configured on the interface GigabitEthernet2/1/0
connectivity from a directly connected host 10.10.10.1/27
Which YANG data model set must the engineer choose?
A)
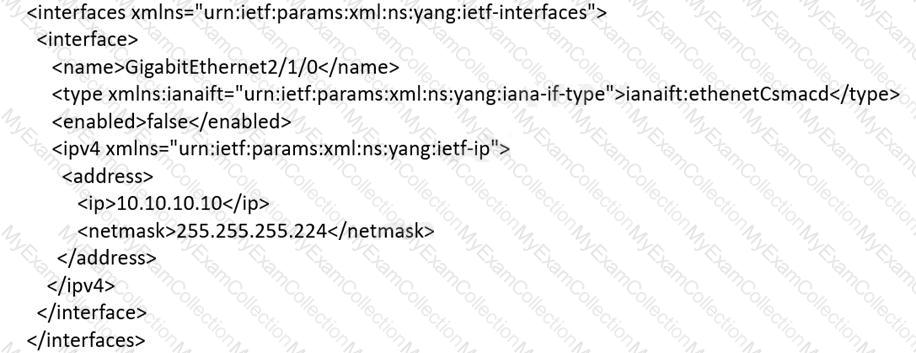
B)
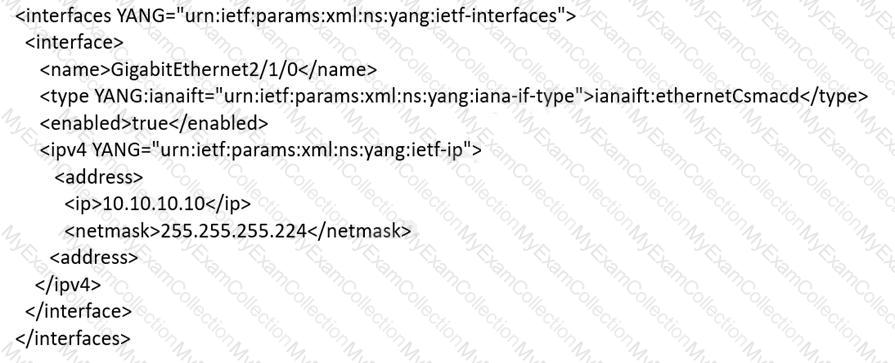
C)
D)
Which feature minimizes HOC connections and reduces strain on the vSmart controller m an SO-WAN architecture?
Refer to the exhibit. An engineer Is designing a redistribution solution for a customer. The customer recently acquired another company and decided to integrate the new network running RlPv1 with the company's existing network. Which redistribution technique must the engineer select to ensure the multipoint two-way redistribution does not cause routing loops?
Drag and drop the characteristics from the left onto the YANG models they describe on the right. Not all options are used.
Which two statements describe source trees in a multicast environment? (Choose two.)
An architect is designing a network solution for a customer The network is IPv6-only with 1000 hosts. The design must provide external access to up to 10 concurrent IPv6 hosts to allow communication with legacy IPv4 devices on an adjacent network. The customer set aside 10 IPv4 addresses to allow for one-to-one communication between hosts. Which solution must the architect select?
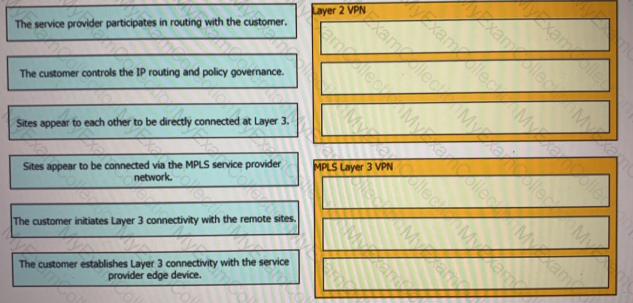
Drag and drop the descriptions from the left onto the corresponding VPN types on the rights.
A network architect Is enabling TV services In the LAN. The source will be streaming to the 239.1.1.1 group IP address. Dense mode Is not allowed In the network. Multicast has already been enabled on all network devices In the LAN segment. Which action must the architect take to finalize the design?
Drag and drop the components in a Cisco SD-Access architecture from the left onto their descriptions on the right.
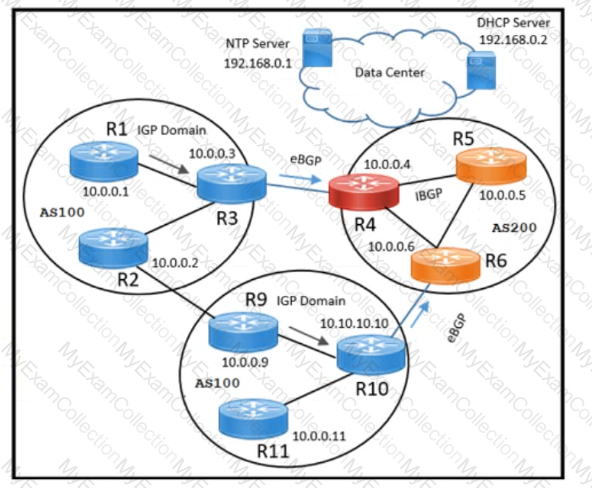
Refer to the exhibit. A network engineer working for a private service provider with an employee ID: 4670:71:451 must design a BGP solution based on:
All traffic originating from AS100 must pass through AS200 to reach the NTP and DHCP server
When a link failure occurs between R3 and R4, traffic must follow the R2-R9 link to reach the NTP and DHCP server.
Which solution must the design include?
What is an advantage of designing an out-of-band network management solution?
Which design consideration must be made when dual WAN Edge routers are deployed at a branch site?
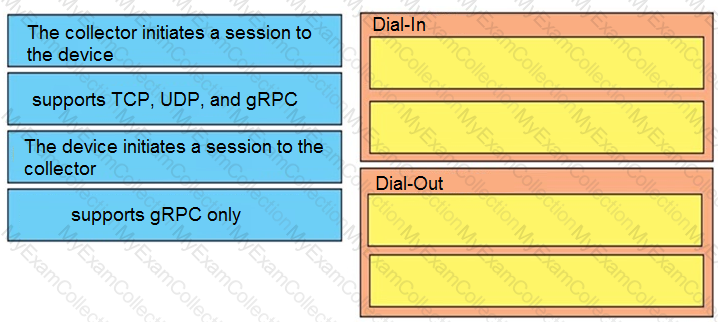
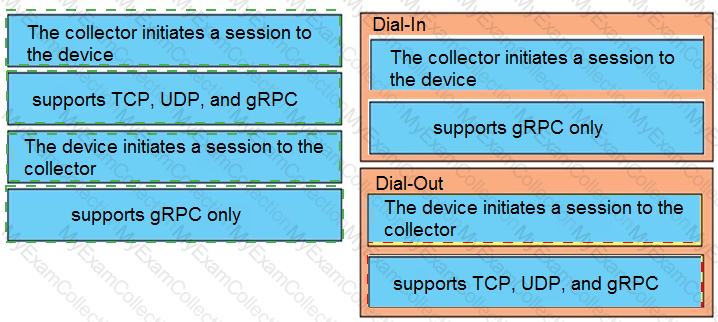
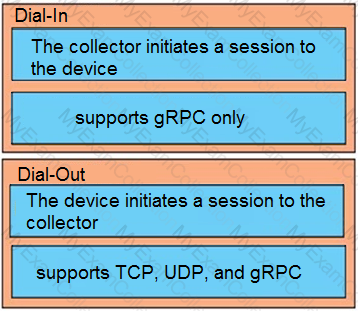
Drag and drop the characteristics from the left onto the correct telemetry mode on the right.
Refer to the exhibit.
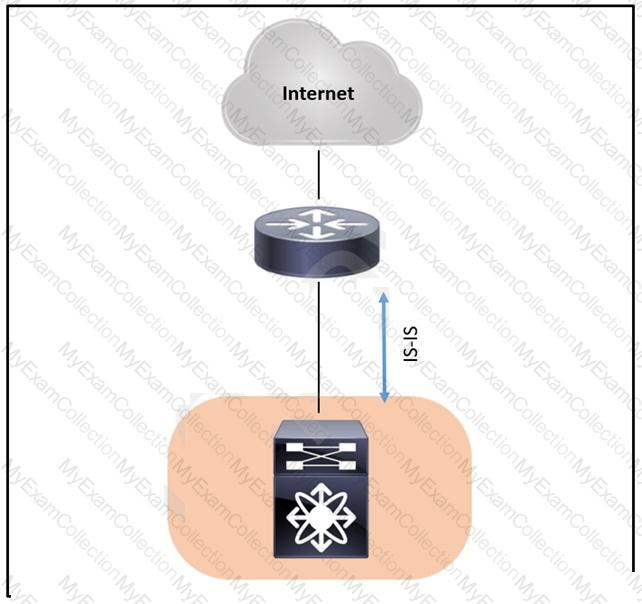
A network engineer must improve the current IS-IS environment. The Catalyst switch is equipped with dual supervisors. Each time a stateful switchover occurs, the network experiences unnecessary route recomputation. Which solution addresses this issue if the upstream router does not understand graceful restart messaging?
A large chain of stores currently uses MPLS-based T1 lines to connect their stores to their data center. An architect must design a new solution to improve availability and reduce costs while keeping these considerations in mind:
» The company uses multicast to deliver training to the stores.
» The company uses dynamic routing protocols and has implemented QoS.
» To simplify deployments, tunnels should be created dynamically on the hub when additional stores open.
Which solution should be included in this design?
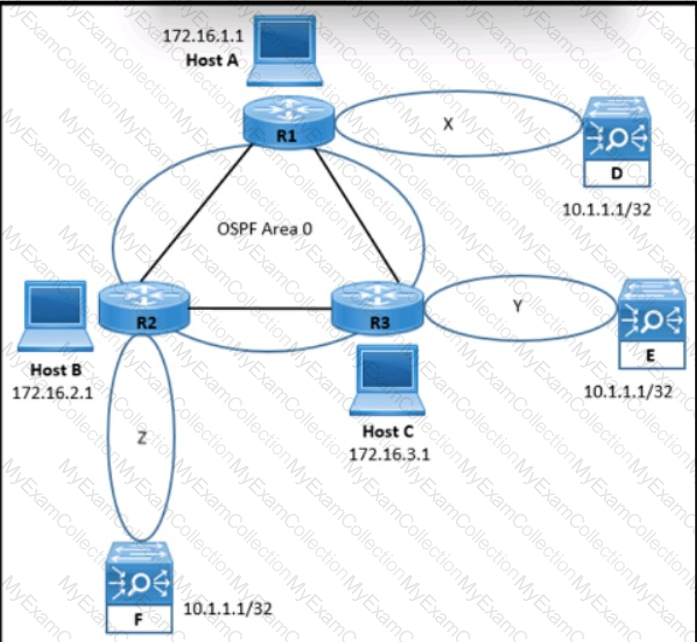
Refer to the exhibit. An engineer is designing an OSPF solution for a customer. The design must take into consideration:
Application load balancers D. E. and F are in different geographical locations and are OSPF-enabled.
Hosts A, B. and C connect to an application through the load balancers using IP address 10.1.1.1/32.
In the event of a failure of one of the load balancers, hosts must still have access to the application.
Which solution must the engineer choose?
A global organization with several branches hired a network architect to design an overlay VPN solution. The branches communicate with each other frequently. The customer expects to add more branches in the future. To meet the customer's security requirements, the architect plans to provide traffic protection using dynamic IPsec tunnels. Which solution should the architect choose?
Refer to the exhibit.
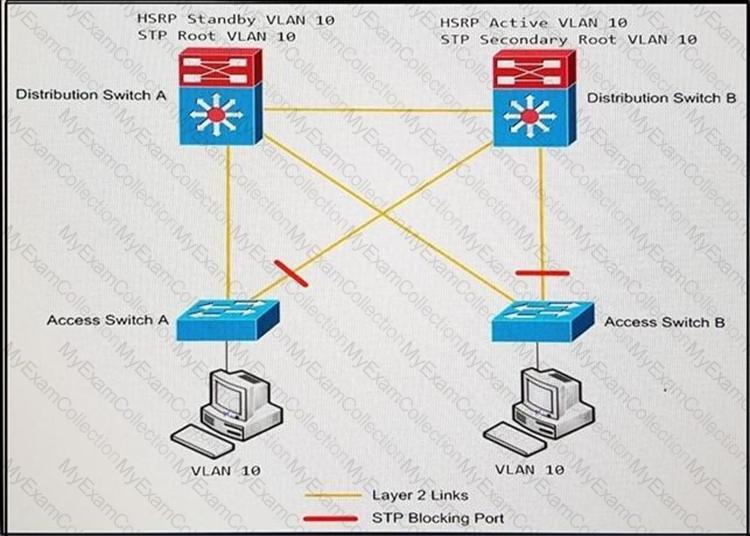
An engineer must optimize the traffic flow of the network. Which change provides a more
efficient design between the access and the distribution layer?
A company has many spoke sites with two data centers. The company wants to exchange the routing information between the data centers and the spoke sites using EIGRP. All locations belong to a single AS. and auto-summarization Is disabled. Which two actions must the company choose? (Choose two.)
A company wants to enable several third-party video conferencing networks based on multicast services. The video conferencing platform can accommodate numerous and dispersed senders and receivers in third-party networks The interior routing protocol is OSPF and the exterior routing protocol is BGP Which multicast mode must be selected to achieve this goal?
Which protocol is deployed through LAN automation to build node-to-node underlay adjacencies in SDA?
Which element in a Cisco SD-WAN architecture maintains a centralized routing table?
Drag and drop the model driven telemetry characteristics from the left onto the mode they belong to on the right.
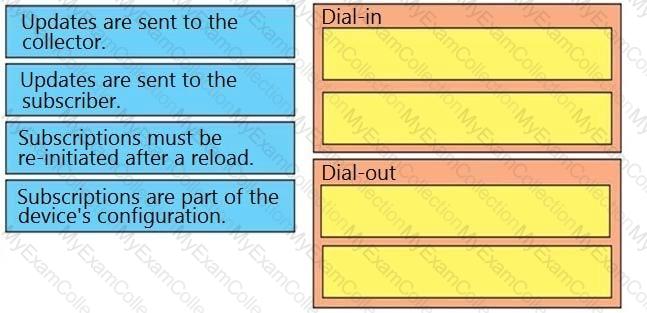
A network engineer prepares a script to configure a loopback interface with IP address 172.16.15.12/32. To comply with the company security policies, 'Content-type':
‘application/yang-data+json‘ is added to the script. Connection to the network devices must be secured. Which code snippet must the network engineer use to meet this requirement?


A customer with an IPv4 only network topology wants to enable IPv6 connectivity while preserving the IPv4 topology services. The customer plans to migrate IPv4 services to the IPv6 topology, then decommission the IPv4 topology. Which topology supports these requirements?
Which two routing protocols allow for unequal cost load balancing? (Choose two.)
Which function are fabric intermediate nodes responsible for in an SD-Access Architecture?
Which design element should an engineer consider when multicast is included in a Cisco SD-Access architecture?
Refer to the exhibit. A customer experienced an unexpected network outage when the link between R1 and R2 went down. An architect must design a solution to ensure network continuity in the event the link fails again. Which solution should the design include?
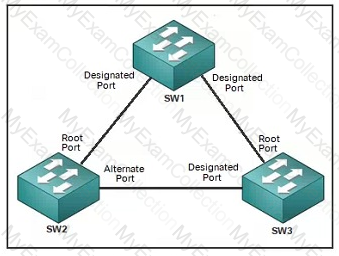
Refer to the exhibit. The connection between SW2 and SW3 is fiber and occasionally experiences unidirectional link failure. An architect must optimize the network to reduce the change of layer2 forwarding loops when the link fails. Which solution should the architect include?
A customer requested that a guaranteed service line be enabled for a manufacturing business in different countries. On the customer side, the QoS-aware application is used to process large data chunks. The application cannot tolerate drops and latency should be as low as possible. Which QoS model must an engineer employ to use the minimum required resources on the ISP network nodes?
Drag and drop the characteristics from the left onto the telemetry mode they apply to on the right.
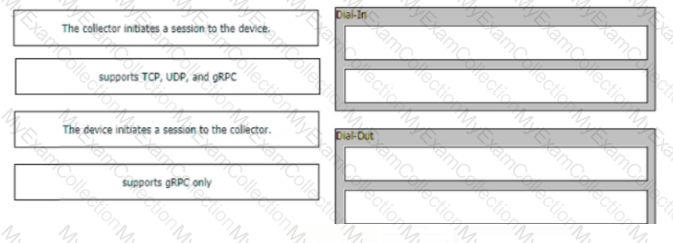
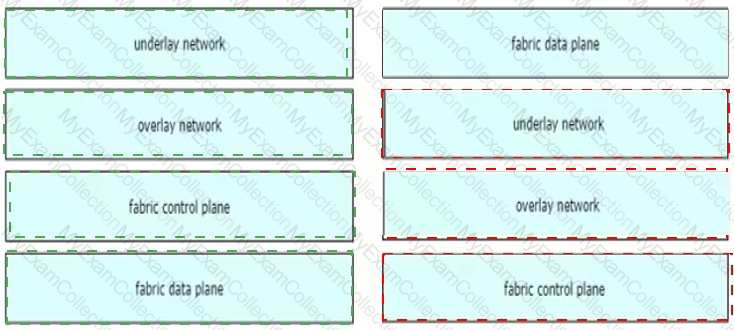
Which two considerations must be made regarding the overlay network for a Cisco SD-Access architecture? (Choose two.)
A network engineer must segregate three interconnected campus networks using IS-IS routing. A two-layer hierarchy must be used to support large routing domains and to avoid more specific routes from each campus network being advertised to other campus network routers automatically. Which two actions does the engineer take to accomplish this segregation? (Choose two.)

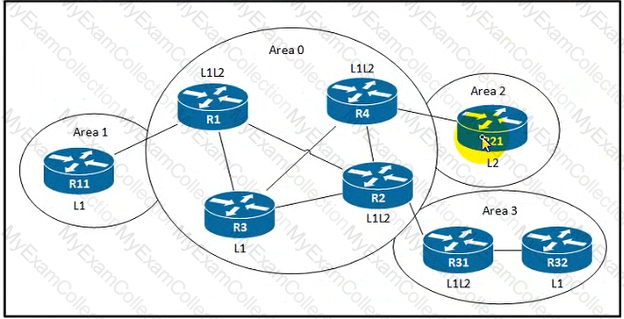
Refer to the exhibit. An engineer is designing an OSPF network for a client. Requirements dictate that the routers in Area 1 should receive all routes belonging to the network, including EIGRP, except the ones originated in the RIP domain. Which action should the engineer take?
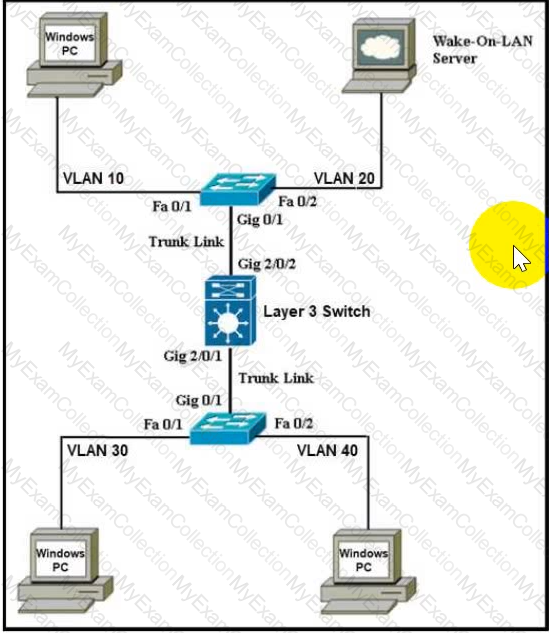
Refer to the exhibit An engineer with an employee ID: 1234 56:789 must design a WoL deployment for a client, and the design must ensure that the Windows PCs are responsive to the WoL magic packets with no delays when the server-side initiates the instruction Which action must the engineer choose?
What is the purpose of the fabric control plane in a Cisco SD-Access architecture?
An engineer must propose a QoS architecture model that allows an application to inform the network of its traffic profile and to request a particular type of service to support its bandwidth and delay requirements. The application requires consistent and dedicated bandwidth end to end. Which QoS architecture model meets these requirements?
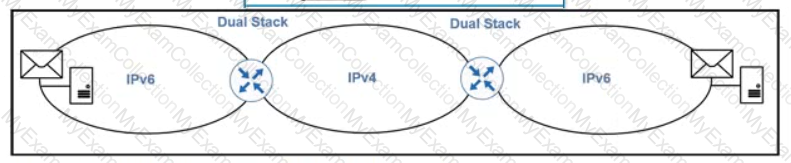
Refer to the exhibit. Which method must an architect use to provide connectivity between the mail servers?
A branch office has a primary L3VPN MPLS connection back to the main office and an IPSEC VPN tunnel that serves as backup. Which design ensures that data is sent over the backup connection only if the primary MPLS circuit is down?
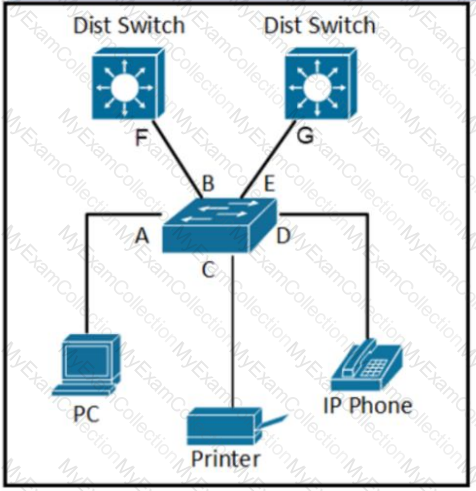
Refer to the exhibit. Which two points in the network must an engineer configure the ports for explicit trust when using a DiffServ model?
 Diagram
Description automatically generated
Diagram
Description automatically generated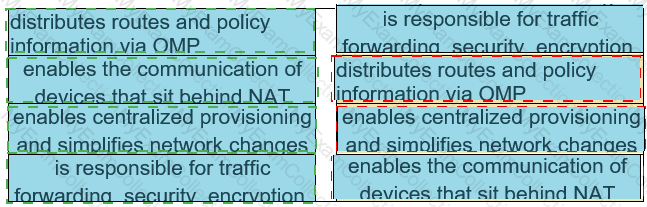
 Diagram
Description automatically generated
Diagram
Description automatically generated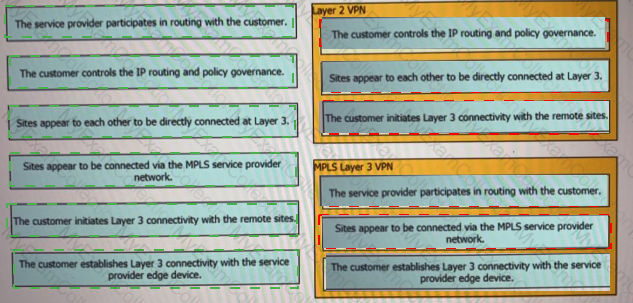
 Graphical user interface, diagram
Description automatically generated with medium confidence
Graphical user interface, diagram
Description automatically generated with medium confidence