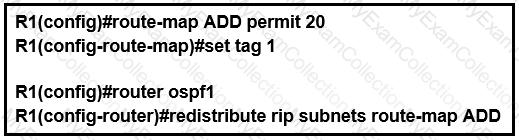
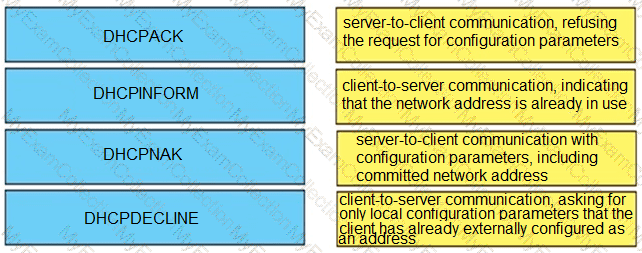
Drag and drop the DHCP messages from the left onto the correct uses on the right.
Refer to the exhibit.

Which control plane policy limits BGP traffic that is destined to the CPU to 1 Mbps and
ignores BGP traffic that is sent at higher rate?
A network engineer needs to verify IP SLA operations on an interface that shows on indication of
excessive traffic.
Which command should the engineer use to complete this action?
Refer to the exhibit.
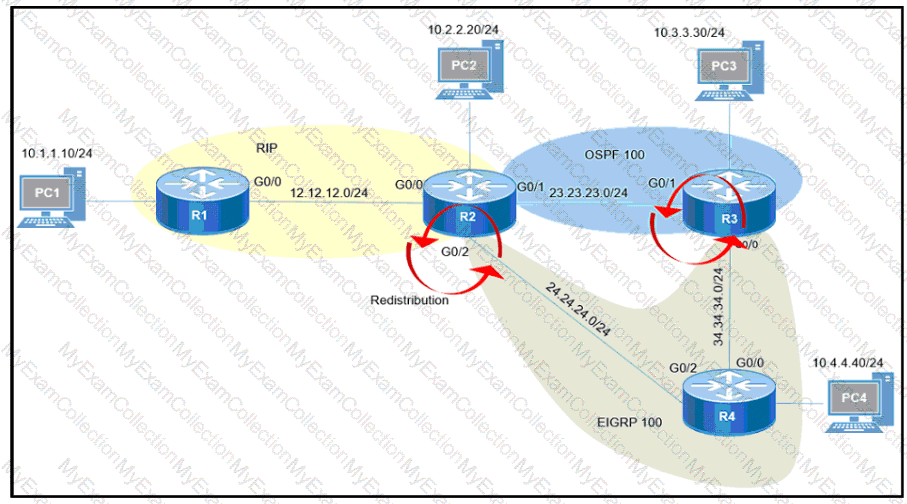
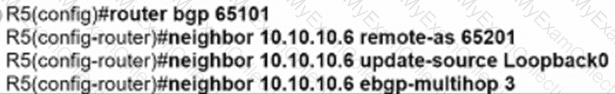
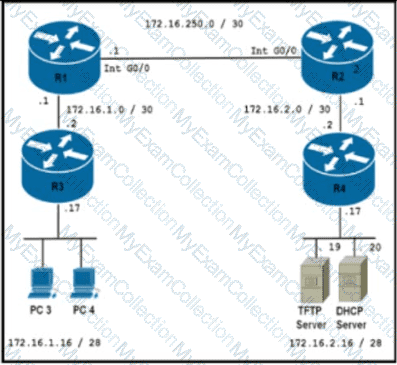
After redistribution is enabled between the routing protocols; PC2, PC3, and PC4 cannot reach PC1. Which action can the engineer take to solve the issue so that all the PCs are reachable?
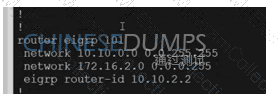
Refer to the exhibit.
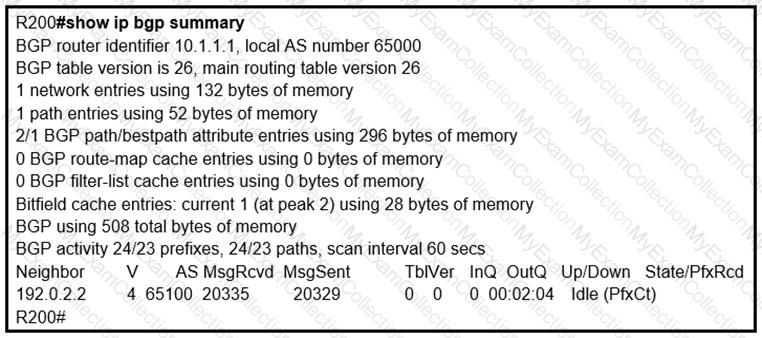
In which circumstance does the BGP neighbor remain in the idle condition?
Exhibit:
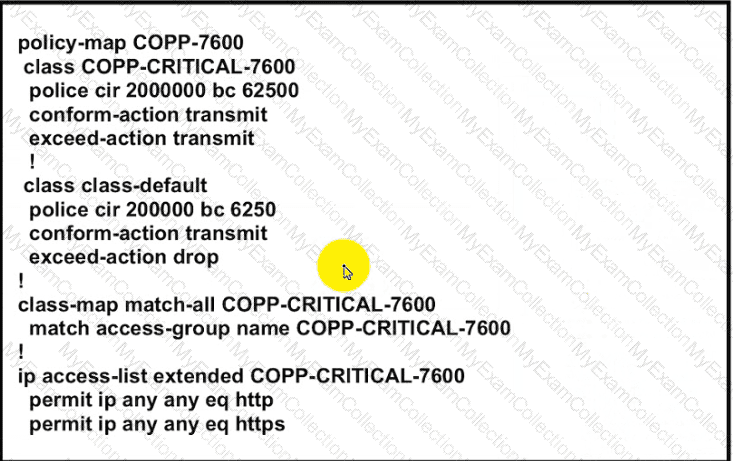
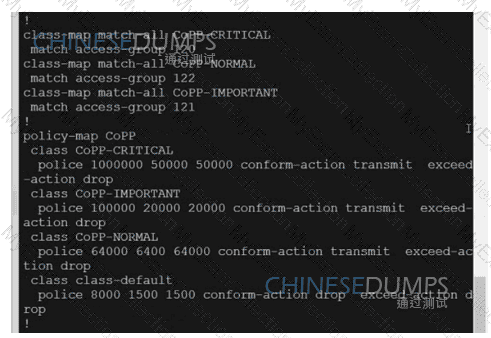
BGP is flapping after the Copp policy is applied. What are the two solutions to fix the issue?
(Choose two)
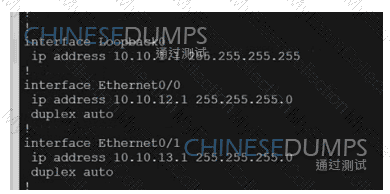
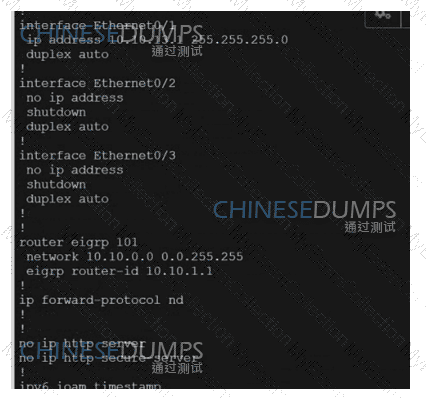
Refer to the exhibit.
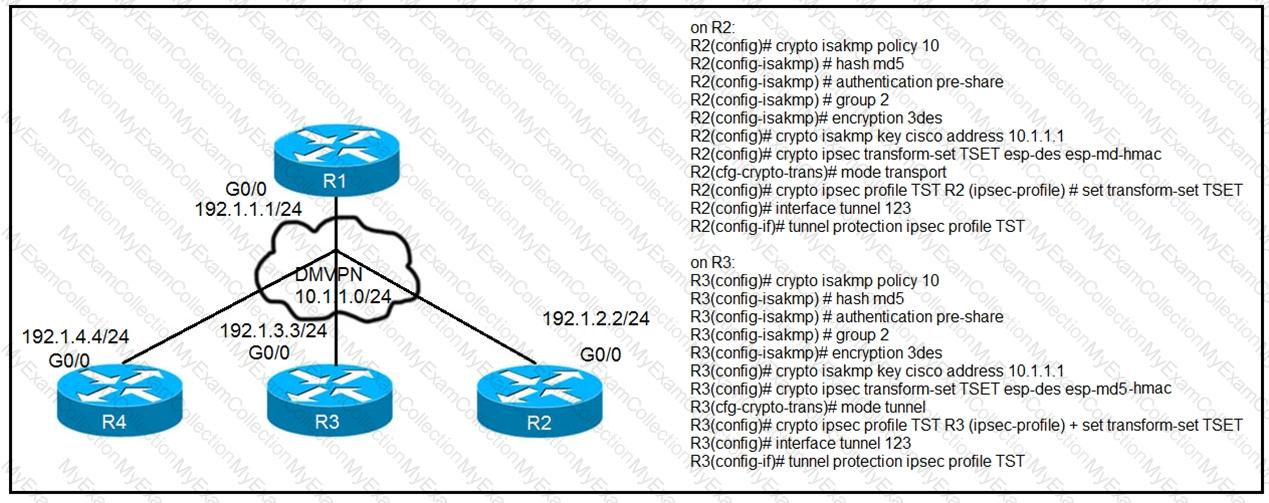
After applying IPsec, the engineer observed that the DMVPN tunnel went down, and both
spoke-to-spoke and hub were not establishing. Which two actions resolve the issue? (Choose two.)
Refer to the exhibit.
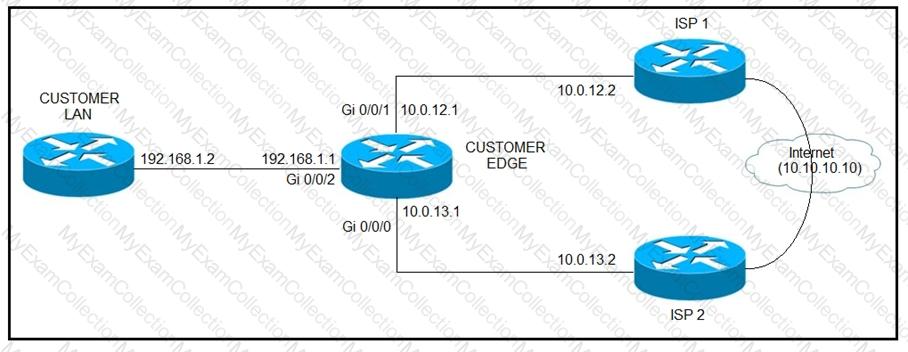
ISP 1 and ISP 2 directly connect to the Internet. A customer is tracking both ISP links to
achieve redundancy and cannot see the Cisco IOS IP SLA tracking output on the router console. Which command is missing from the IP SLA configuration?
Which command displays the IP routing table information that is associated with VRF-Lite?
Refer to the exhibit.
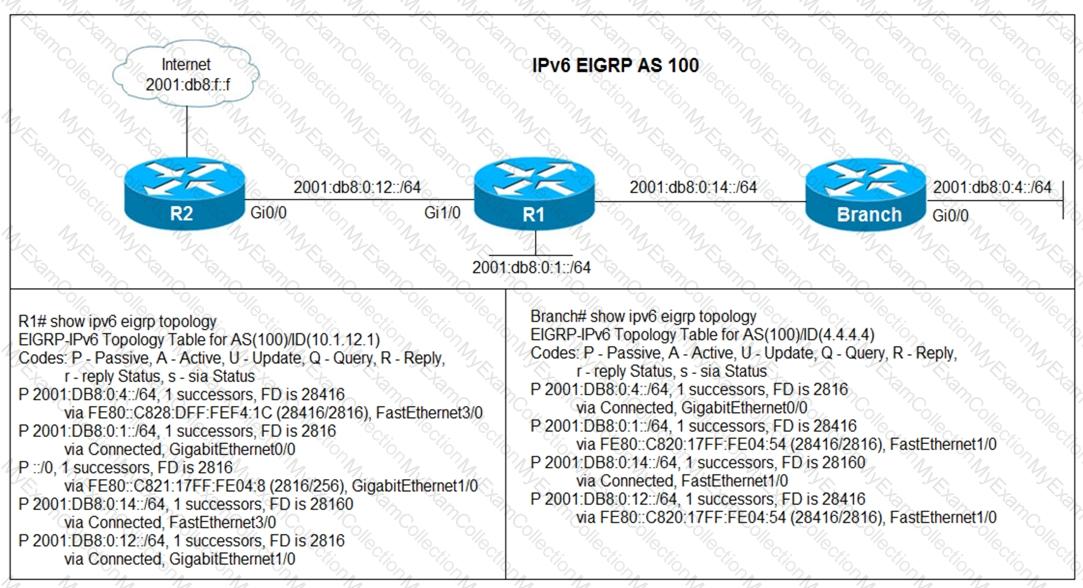
Users in the branch network of 2001:db8:0:4::/64 report that they cannot access the Internet. Which command is issued in IPv6 router EIGRP 100 configuration mode to solve this issue?
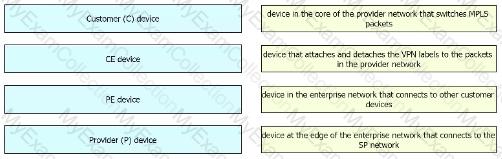
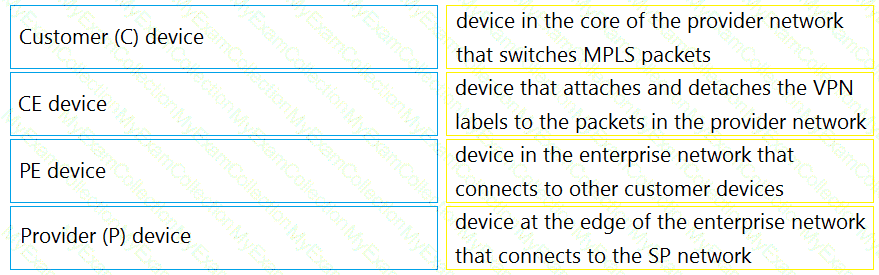
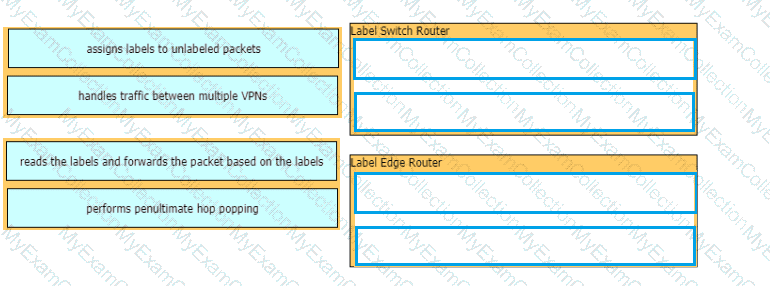
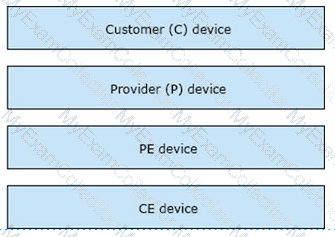
Drag and drop the MPLS VPN device types from me left onto the definitions on the right.
Refer to the exhibit.
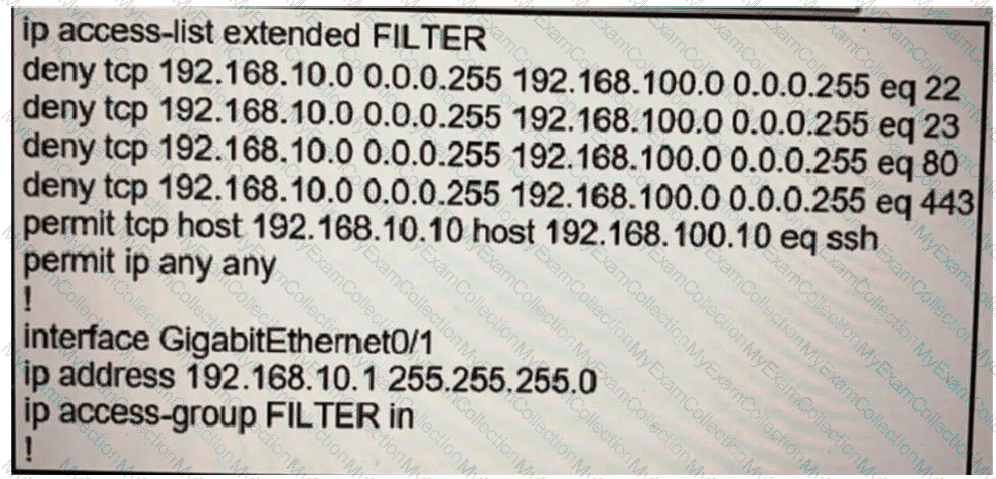
The ACL is placed on the inbound Gigabit 0/1 interface of the router. Host
192.168.10.10cannot SSH to host 192.168.100.10 even though the flow is permitted. Which action
resolves the issue without opening full access to this router?
Which configuration enabled the VRF that is labeled “Inet†on FastEthernet0/0?
Refer to the exhibit.
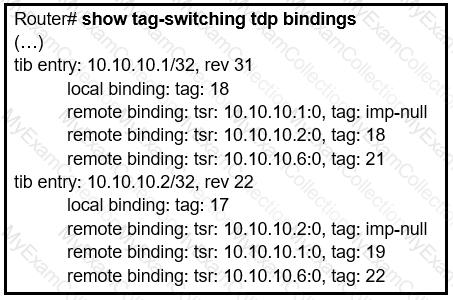
What does the imp-null tag represent in the MPLS VPN cloud?
Drag and Drop the IPv6 First-Hop Security features from the left onto the definitions on the right.

Which method changes the forwarding decision that a router makes without first changing the routing table or influencing the IP data plane?
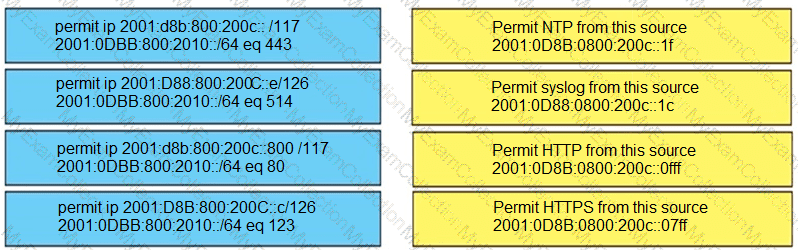
Drag and drop the addresses from the left onto the correct IPv6 filter purposes on the right.
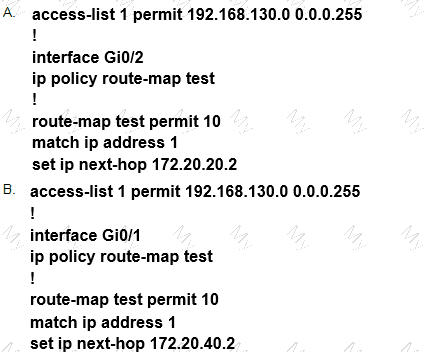
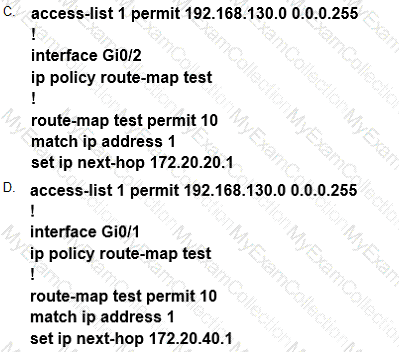
Refer to the exhibit.
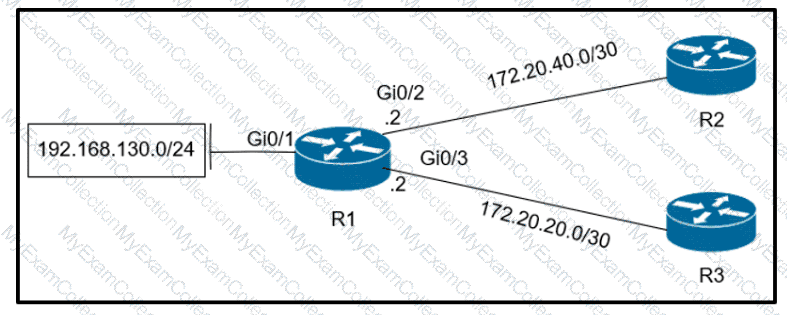
Which configuration configures a policy on R1 to forward any traffic that is sourced from
the 192.168.130.0/24 network to R2?
Which command is used to check IP SLA when an interface is suspected to receive lots of traffic with options?
Refer to the exhibit.

An IP SLA is configured to use the backup default route when the primary is down, but it is not working as desired. Which command fixes the issue?
Drag and drop the MPLS VPN concepts from the left onto the correct descriptions on the right.
Refer to the exhibit.
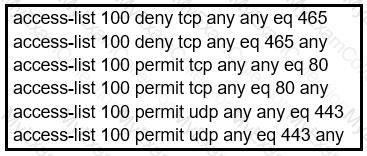
During troubleshooting it was discovered that the device is not reachable using a secure
web browser. What is needed to fix the problem?
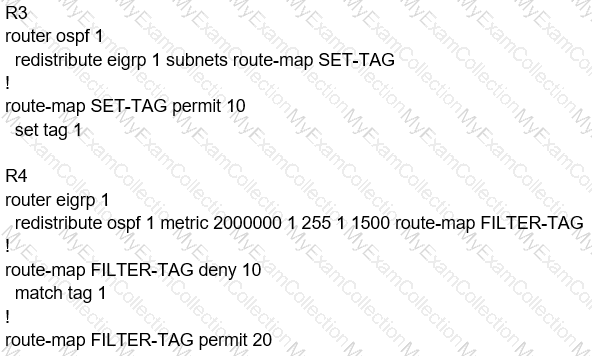
Refer to the exhibit.
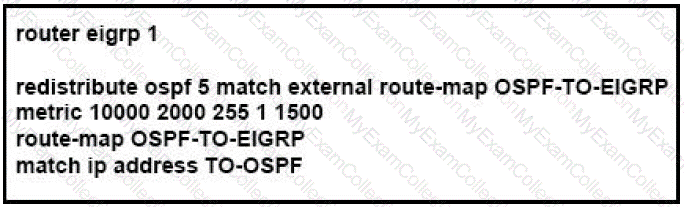
Which routes from OSPF process 5 are redistributed into EIGRP?
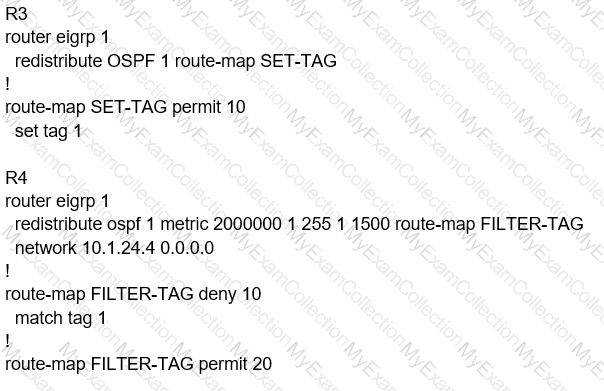
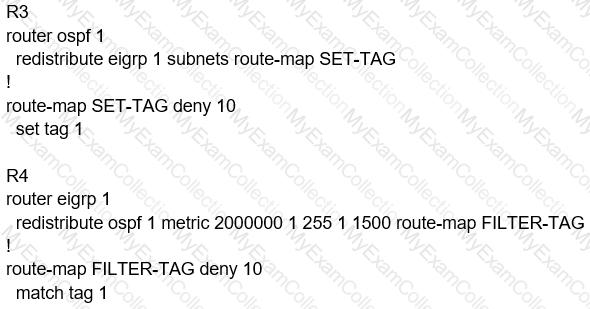
Refer to the exhibit.
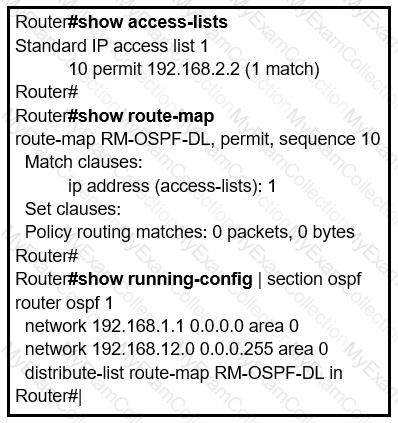
An engineer is trying to block the route to 192.168.2.2 from the routing table by using the
configuration that is shown. The route is still present in the routing table as an OSPF route. Which action blocks the route?
Refer to the exhibit.
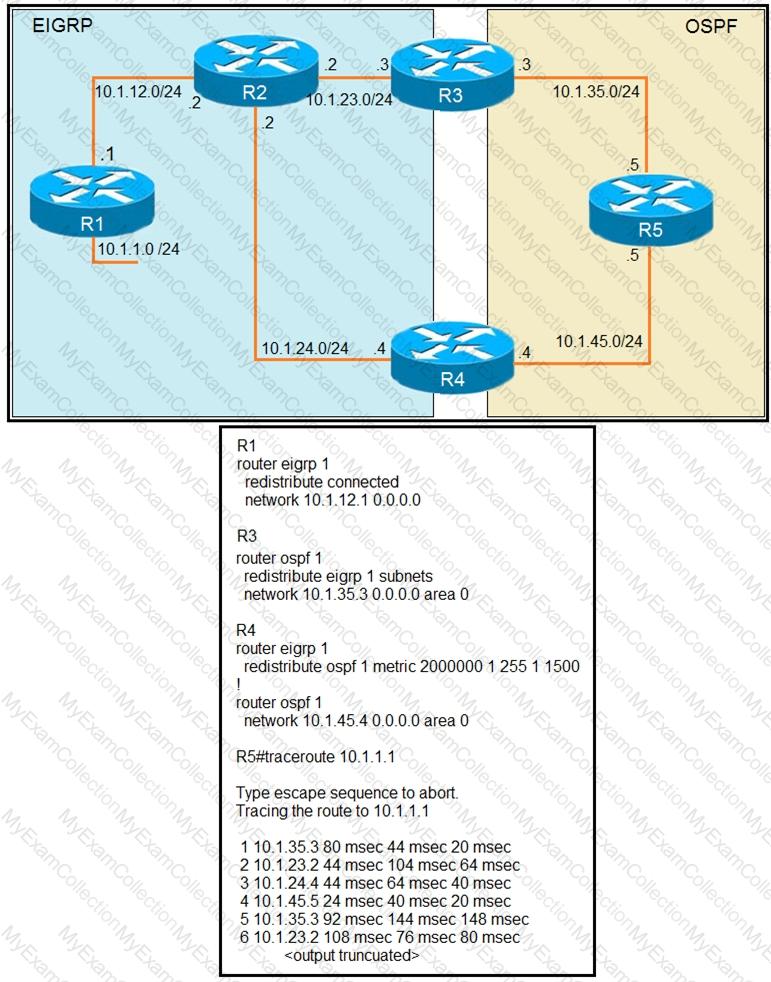
The output of the trace route from R5 shows a loop in the network. Which configuration
prevents this loop?
A)
B)
C)

D)
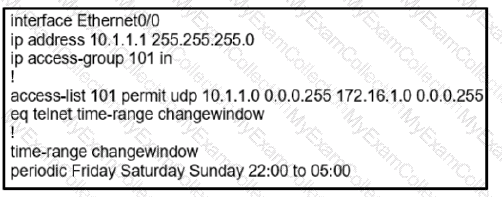
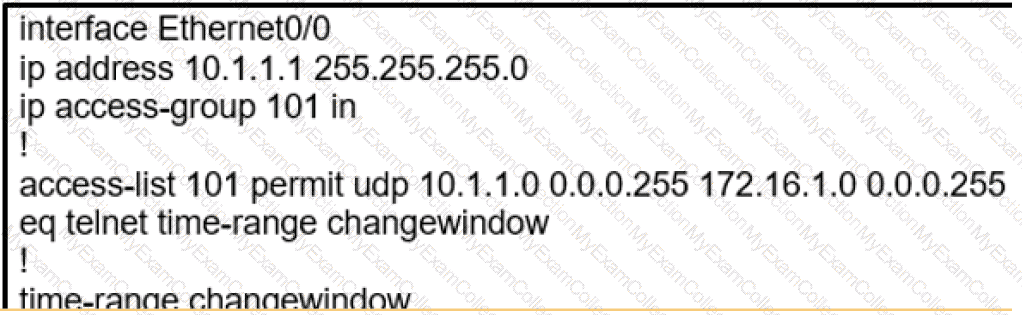
During the maintenance window an administrator accidentally deleted the Telnet-related
configuration that permits a Telnet connection from the inside network (Eth0/0) to the outside of the networking between Friday – Sunday night hours only. Which configuration resolves the issue?
A)
B)
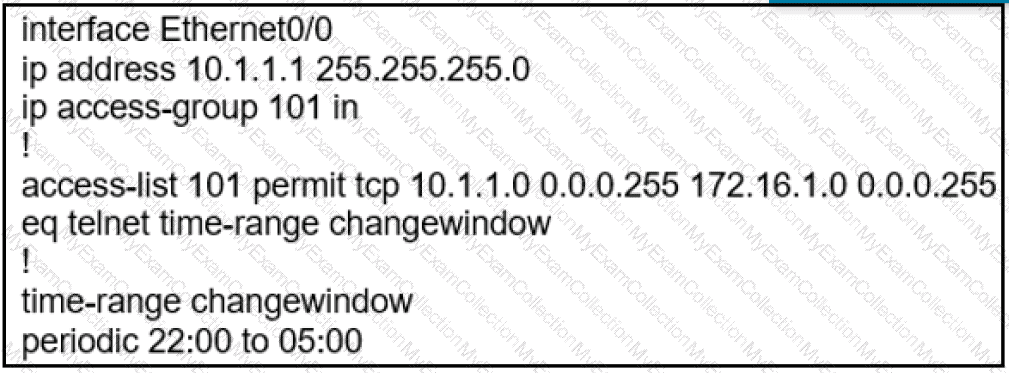
C)
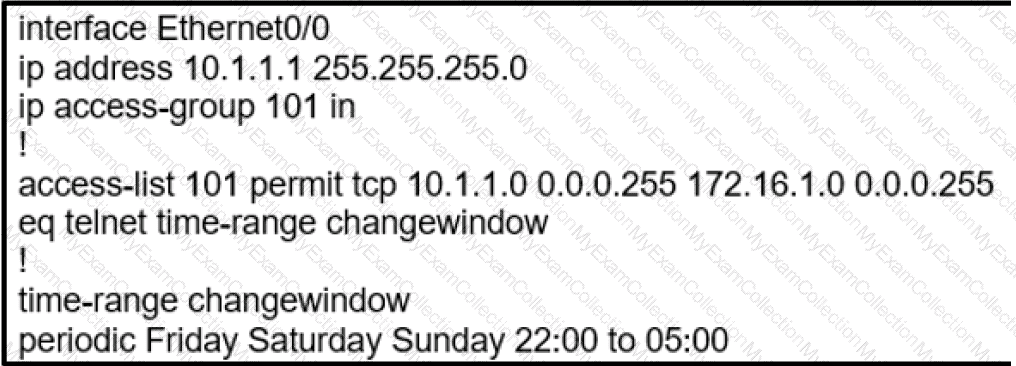
D)
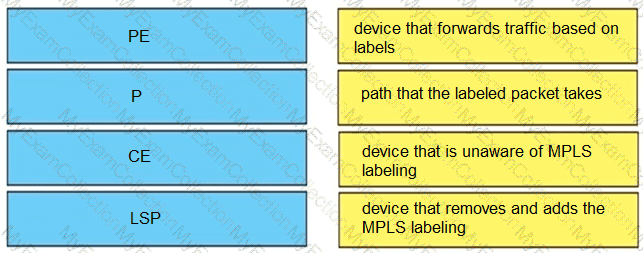
Drag and drop the MPLS terms from the left onto the correct definitions on the right.
Refer to the exhibit.
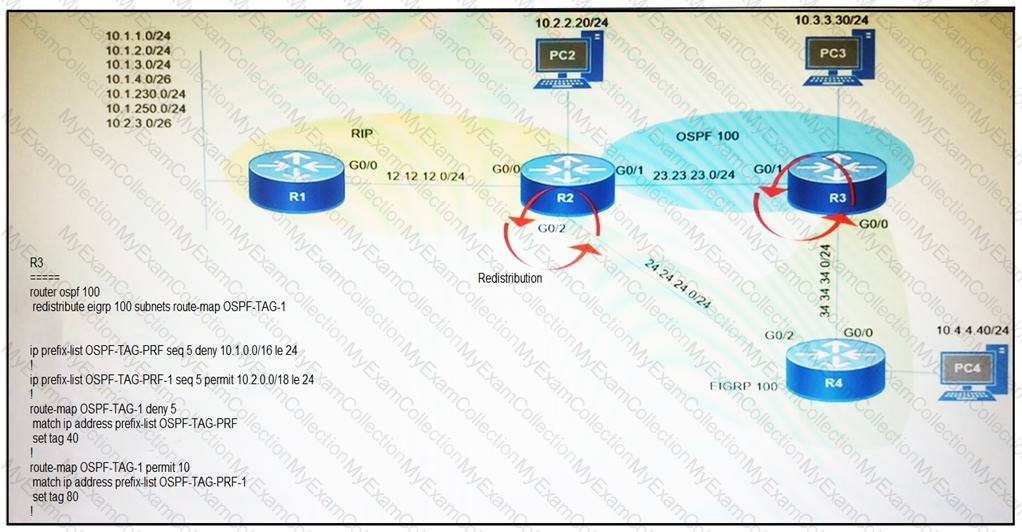
Which subnet is redistributed from EIGRP to OSPF routing protocols?
An engineer configured the wrong default gateway for the Cisco DNA Center enterprise interface during the install. Which command must the engineer run to correct the configuration?
Refer to the exhibit.
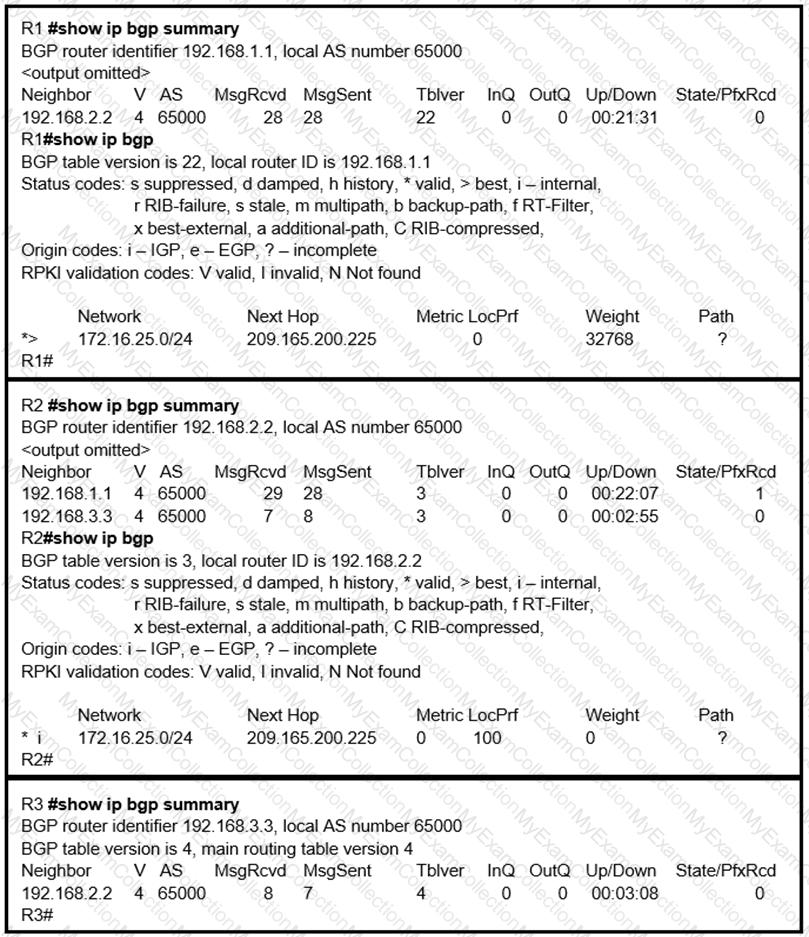
R2 is a route reflector, and R1 and R3 are route reflector clients. The route reflector learns the route to 172.16.25.0/24 from R1, but it does not advertise to R3. What is the reason the route is not advertised?
When provisioning a device in Cisco DNA Center, the engineer sees the error message “Cannot select the device. Not compatible with templateâ€.
What is the reason for the error?
Refer to the exhibit.
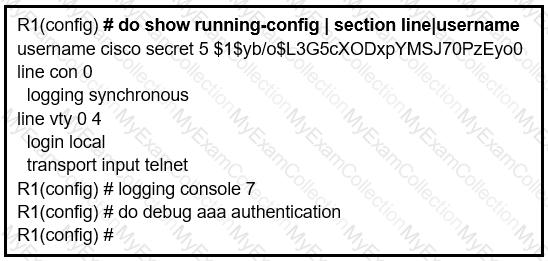
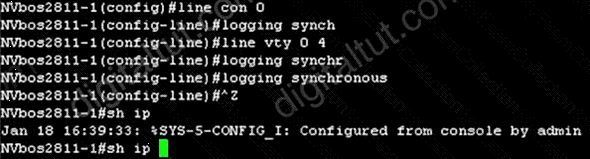
An administrator that is connected to the console does not see debug messages when
remote users log in. Which action ensures that debug messages are displayed for remote logins?
Drag and drop the OSPF adjacency states from the left onto the correct descriptions on the right.
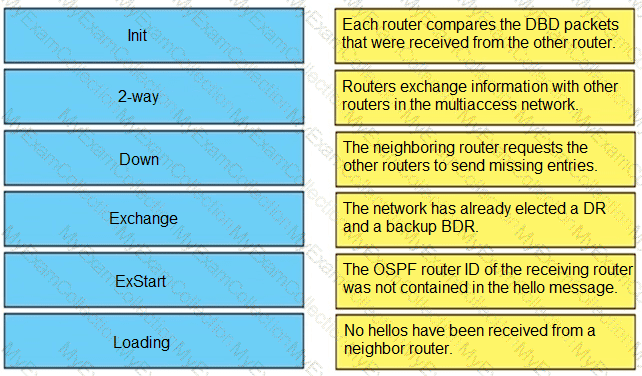
Which two statements about redistributing EIGRP into OSPF are true? (Choose two)
Which attribute eliminates LFAs that belong to protected paths in situations where links in a network are connected through a common fiber?
Refer to the exhibit.
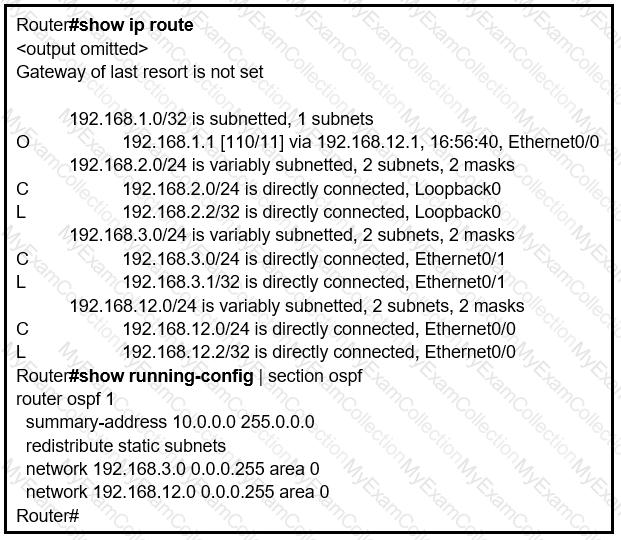
An engineer is trying to generate a summary route in OSPF for network 10.0.0.0/8, but the
summary route does not show up in the routing table. Why is the summary route missing?
Refer to the exhibit.
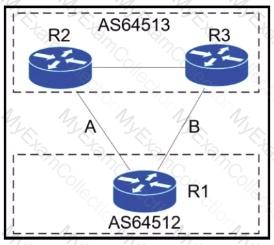
A network engineer for AS64512 must remove the inbound and outbound traffic from link A during maintenance without closing the BGP session so that there ............ a backup link over link A toward the ASN. Which BGP configuration on R1 accomplishes this goal?
A)
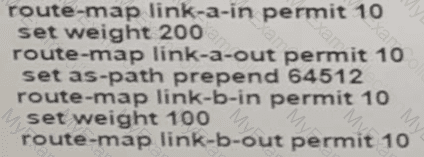
B)

C)
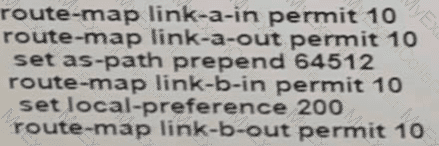
D)
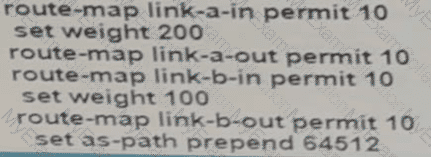
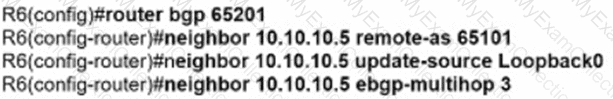
Refer to the exhibit.

The R1 and R2 configurations are:
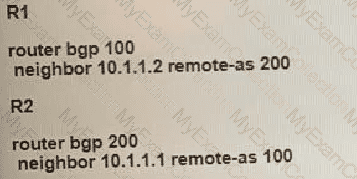
The neighbor is not coming up. Which two sets of configurations bring the neighbors up? (Choose two.)
Refer to the exhibit.
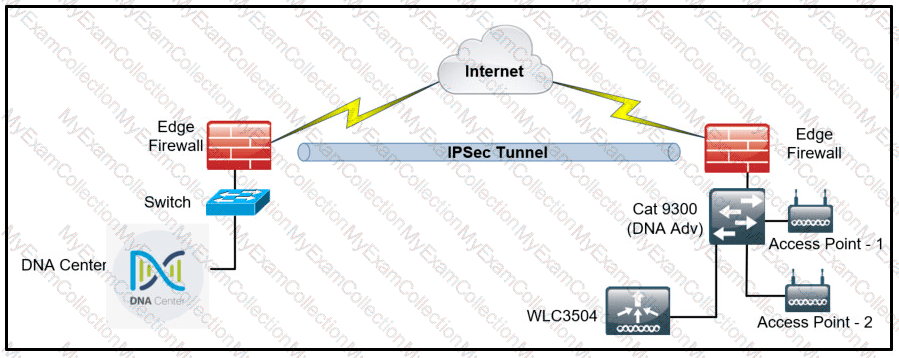
A network administrator is discovering a Cisco Catalyst 9300 and a Cisco WLC 3504 in Cisco DNA Center. The Catalyst 9300 is added successfully However the WLC is showing [ error "uncontactable" when the administrator tries to add it in Cisco DNA Center. Which action discovers WLC in Cisco DNA Center successfully?
Drag and drop the MPLS VPN device types from the left onto the definitions on the right.
Refer to the exhibit.

A network administrator configured an IPv6 access list to allow TCP return frame only, but it is not working as expected. Which changes resolve this issue?
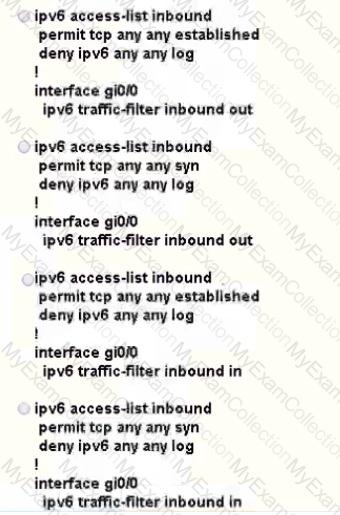
Refer to the exhibit.
A network is under a cyberattack. A network engineer connected to R1 by SSH and enabled the terminal monitor via SSH session to find the source and destination of the attack. The session was flooded with messages, which made it impossible for the engineer to troubleshoot the issue. Which command resolves this issue on R1?
Refer to the exhibit.

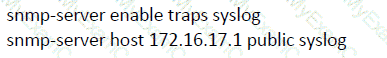
The administrator can see the traps for the failed login attempts, but cannot see the traps of successful login attempts. What command is needed to resolve the issue?
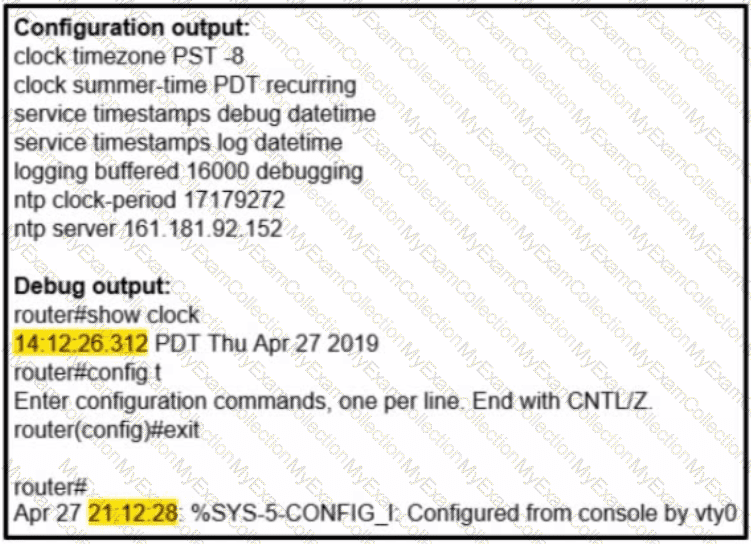
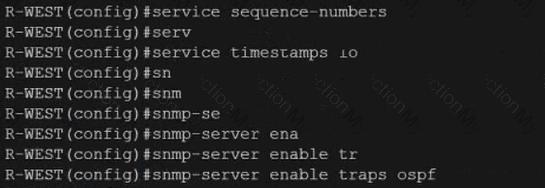
Refer to the exhibit. A network administrator configured NTP on a Cisco router to get synchronized time for system and logs from a unified time source The configuration did not work as desired Which service must be enabled to resolve the issue?
A DMVPN single hub topology is using IPsec + mGRE with OSPF. What should be configured on the hub to ensure it will be the designated router?
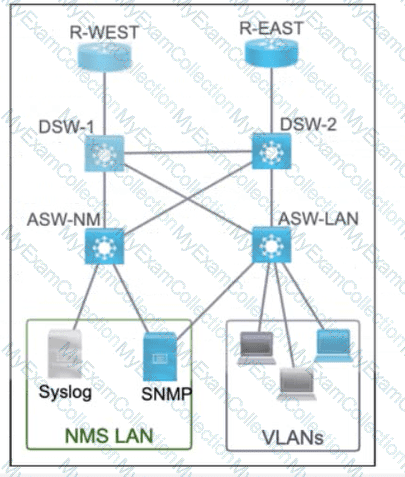
Clients on ALS2 receive IPv4 and IPv6 addresses but clients on ALS1 receive only IPv4 addresses and not IPv6 addresses. Which action on DSW1 allows clients on ALS1 to receive IPv6 addresses?
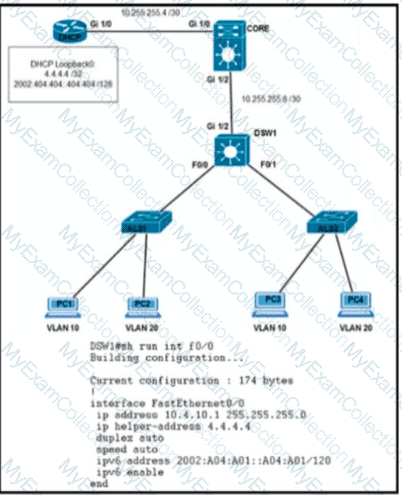
Which Ipv6 first-hop security feature helps to minimize denial of service attacks?
Drag and drop the MPLS concepts from the left onto the descriptions on the right.

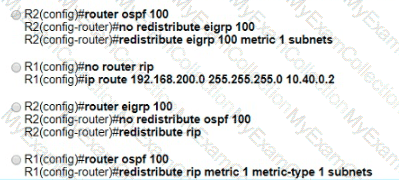
Refer to the exhibit.
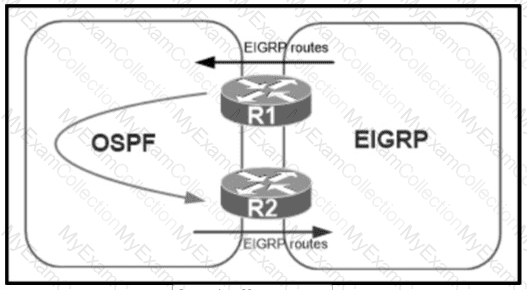
A network administrator configured mutual redistribution on R1 and R2 routers, which caused instability in the network. Which action resolves the issue?
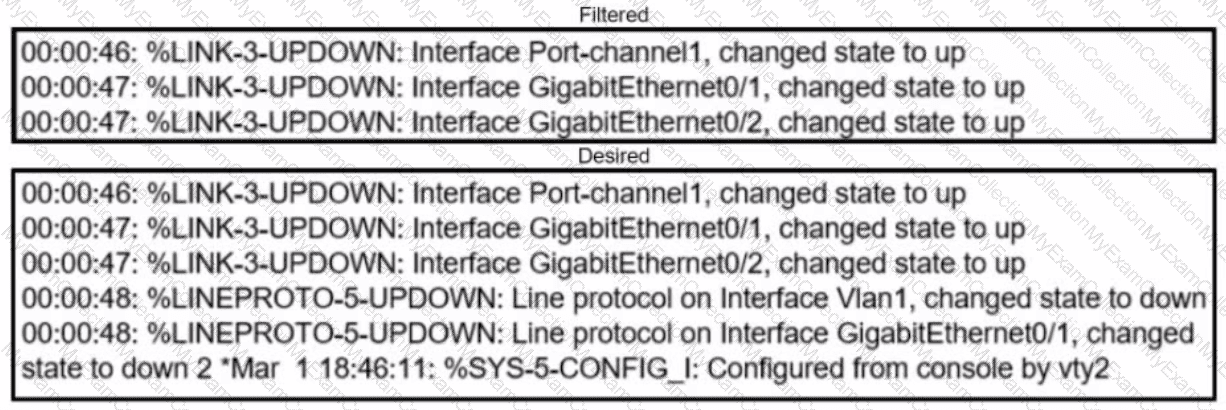
Refer to the exhibits. An engineer filtered messages based on severity to minimize log messages. After applying the filter, the engineer noticed that it filtered required messages as well. Which action must the engineer take to resolve the issue?
Refer to the exhibit.
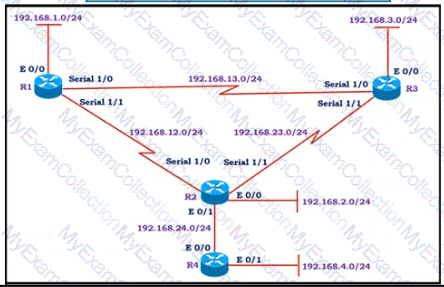
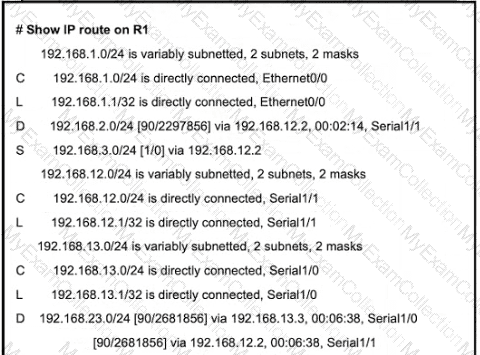
All the serial between R1, R2, and R3 have the Same bandwidth. User on the 192.168.1.0/24 network report slow response times while they access resource on network 192.168.3.0/24. When a traceroute is run on the path. It shows that the packet is getting forwarded via R2 to R3 although the link between R1 and R3 is still up. What must the network administrator to fix the slowness?
An engineer configured SNMP notifications sent to the management server using authentication and encrypting data with DES. An error in the response PDU is received as "UNKNOWNUSERNAME. WRONGDIGEST". Which action resolves the issue?
What is the minimum time gap required by the local system before putting a BFD control packet on the wire?
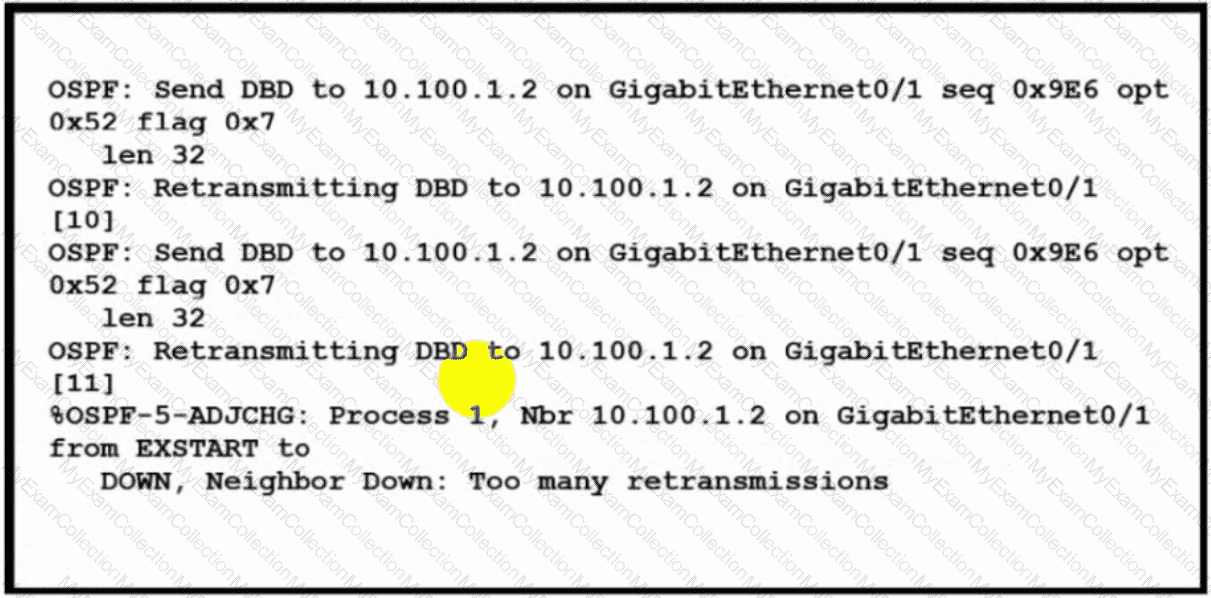
Refer to the exhibit. The OSPF neighbor relationship is not coming up What must be configured to restore OSPF neighbor adjacency?
Refer to Exhibit.
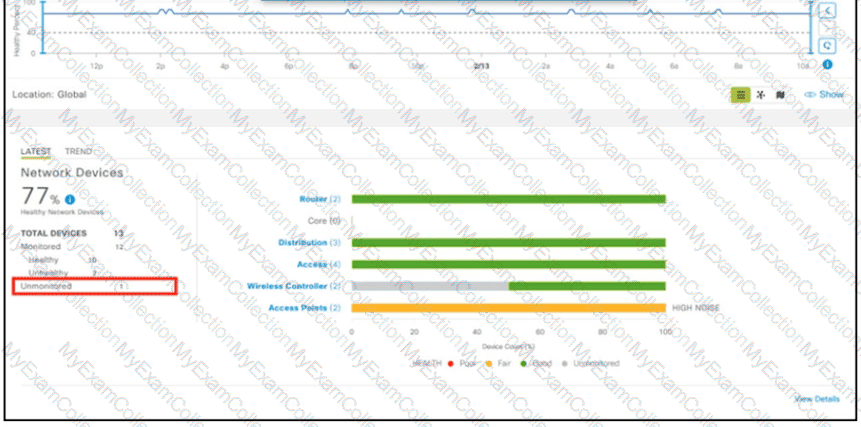
A network administrator added one router in the Cisco DNA Center and checked its discovery and health from the Network Health Dashboard. The network administrator observed that the router is still showing up as unmonitored. What must be configured on the router to mount it in the Cisco DNA Center?
Refer to the exhibit.
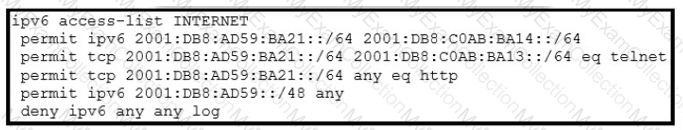
When monitoring an IPv6 access list, an engineer notices that the ACL does not have any hits and is causing unnecessary traffic to pass through the interface Which command must be configured to resolve the issue?
Refer to the exhibit.
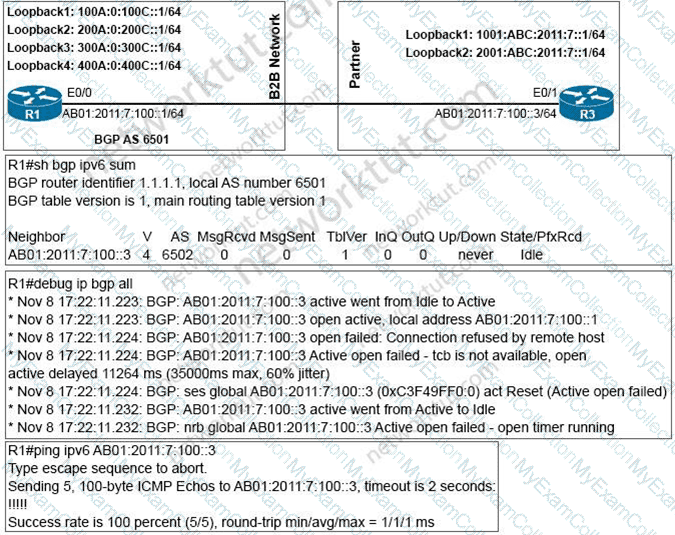

An engineer configured BGP between routers R1 and R3 The BOP peers cannot establish neighbor adjacency to be able to exchange routes. Which configuration resolves this issue?
Refer to exhibit.
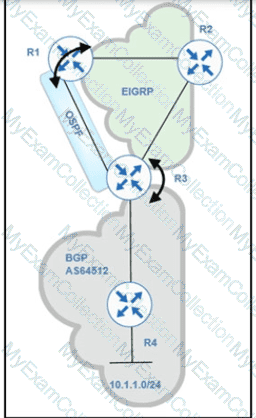
Routing protocols are mutually redistributed on R3 and R1. Users report intermittent connectivity to services hosted on the 10.1.1.0/24 prefix. Significant routing update changes are noticed on R3 when the show ip route profile
command is run. How must the services be stabilized?
Refer to the exhibit.
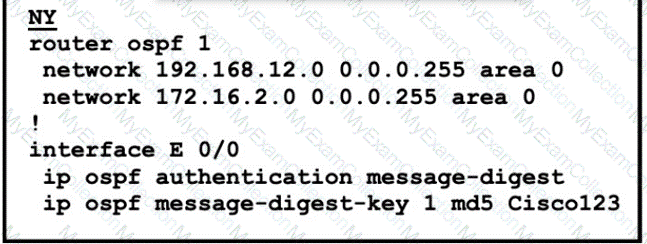
The neighbor relationship is not coming up Which two configurations bring the adjacency up? (Choose two)
When configuring Control Plane Policing on a router to protect it from malicious traffic, an engineer observes that the configured routing protocols start flapping on
that device. Which action in the Control Plane Policy prevents this problem in a production environment while achieving the security objective?
An engineer configured access list NON-CISCO in a policy to influence routes

What are the two effects of this route map configuration? (Choose two.)
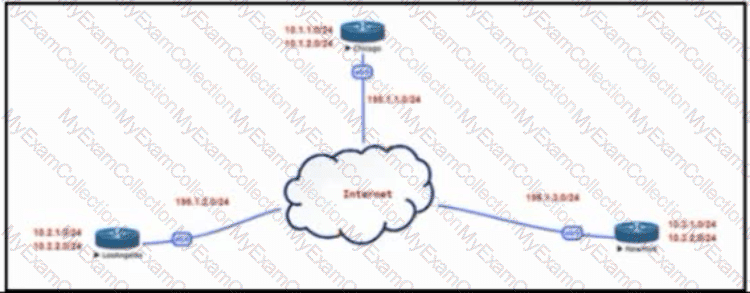
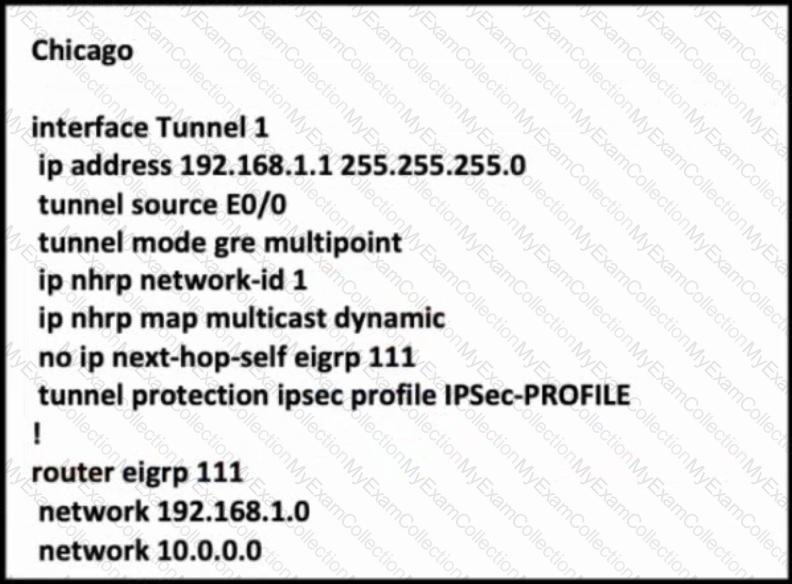
Refer to the exhibit. The Los Angeles and New York routers are receiving routes from Chicago but not from each other. Which configuration fixes the issue?
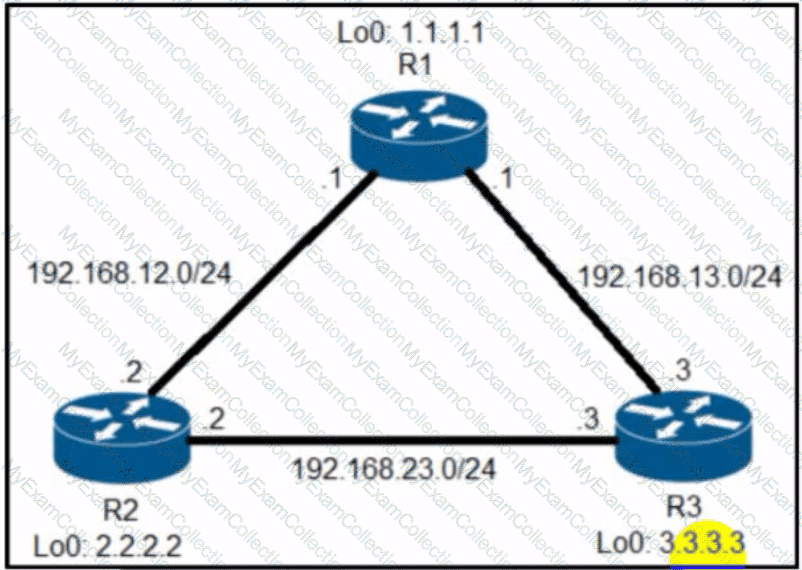

Refer to the exhibit. R2 has two paths to reach 192.168.13.0/24. but traffic is sent only through R3. Which action allows traffic to use both paths?
An engineer configured a DHCP server for Cisco IP phones to download its configuration from a TFTP server, but the IP phones failed to toad the configuration What must be configured to resolve the issue?
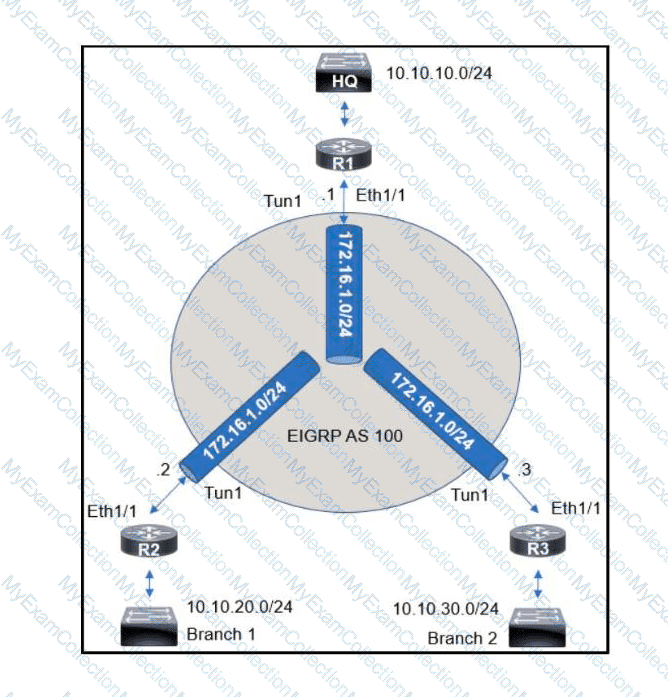
An engineer sets up a DMVPN connection to connect branch 1 and branch 2 to HQ branch 1 and branch 2 cannot communicate with each other. Which change must be made to resolve this issue?

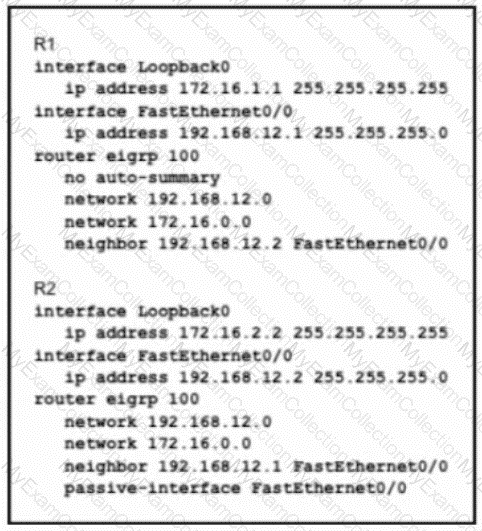
Refer to the exhibit. R1 and R2 cannot establish an EIGRP adjacency. Which action establishes EIGRP adjacency?
Refer to the exhibit.
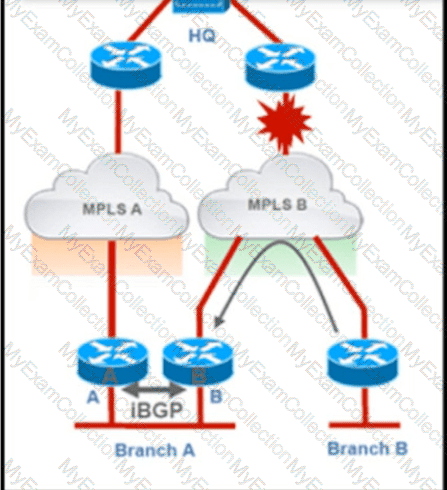
Troubleshoot and ensure that branch B only ever uses the MPLS B network to reach HQ. Which action achieves this requirement?
Refer to Exhibit.
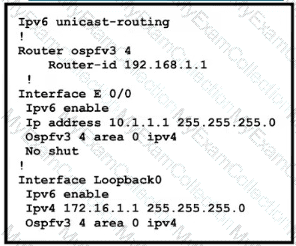
The network administrator configured the branch router for IPv6 on the E0/0 interface. The neighboring router is fully configured to meet requirements, but the neighbor relationship is not coming up. Which action fixes the problem on the branch router to bring the IPv6 neighbors up?
Refer to the exhibit.
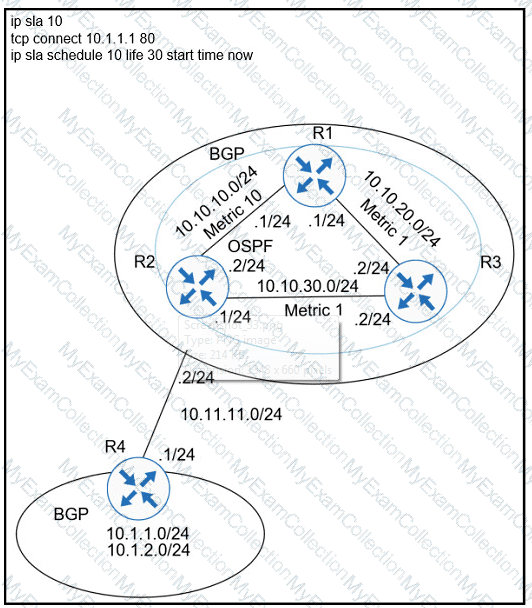
A user has set up an IP SLA probe to test if a non-SLA host web server on IP address 10.1.1.1 accepts HTTP sessions prior to deployment. The probe is failing. Which action should the network administrator recommend for the probe to succeed?
An engineer configured a Cisco router to send reliable and encrypted notifications for any events to the management server. It was noticed that the notification messages are reliable but not encrypted. Which action resolves the issue?
Refer to the exhibit.
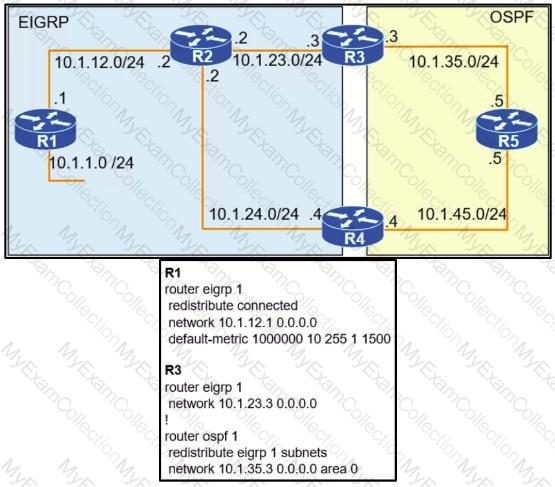
To provide reachability to network 10.1.1.0 /24 from R5, the network administrator redistributes EIGRP into OSPF on R3 but notices that R4 is now taking a ........... path through R5 to reach 10.1.1.0/24 network. Which action fixes the issue while keeping the reachability from R5 to 10.1.1.0/24 network?
Refer to the exhibit.
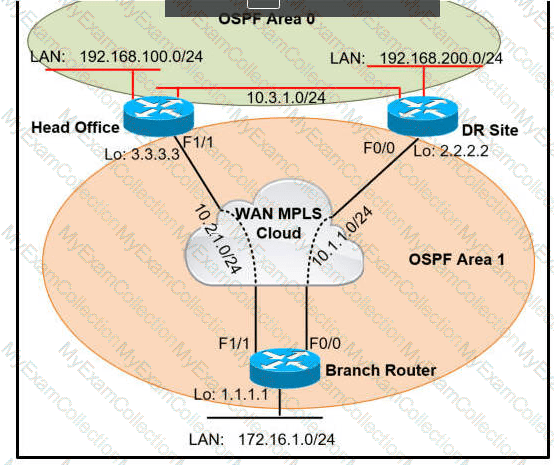
A network administrator reviews the branch router console log to troubleshoot the OSPF adjacency issue with the DR router. Which action resolves this issue?
Exhibit:
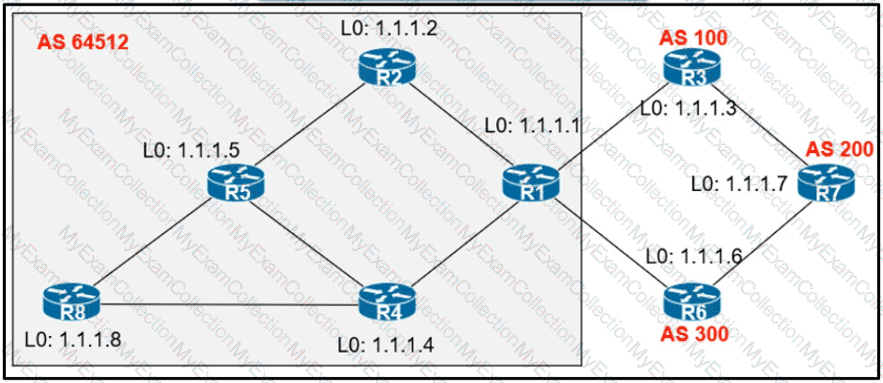
An engineer configured R2 and R5 as route reflectors and noticed that not all routes are sent to R1 to advertise to the eBGP peers. Which iBGP routers must be configured as route reflectors to advertise all routes to restore reachability across all networks?
Refer to the exhibit.
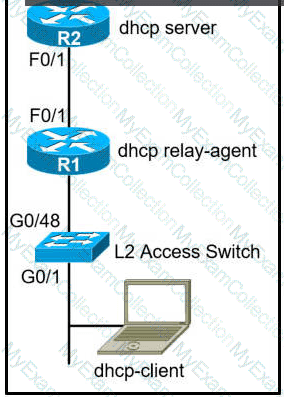
The network administrator can see the DHCP discovery packet in R1. but R2 is not replying to the DHCP request. The R1 related interface is configured with the DHCP helper address. If the PC is directly connected to the FaO/1 interface on R2, the DHCP server assigns as IP address from the DHCP pool to the PC. Which two commands resolve this issue? (Choose two.)
A customer reports to the support desk that they cannot print from their PC to the local printer id:401987778. Which tool must be used to diagnose the issue using Cisco DNA Center Assurance?
Which two protocols work in the control plane of P routers across the MPLS cloud? (choose two)
Refer to the exhibit.
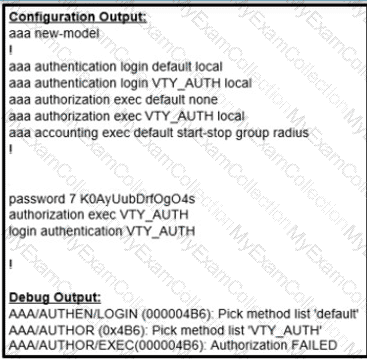
Which action resolves the failed authentication attempt to the router?
Refer to the exhibit.
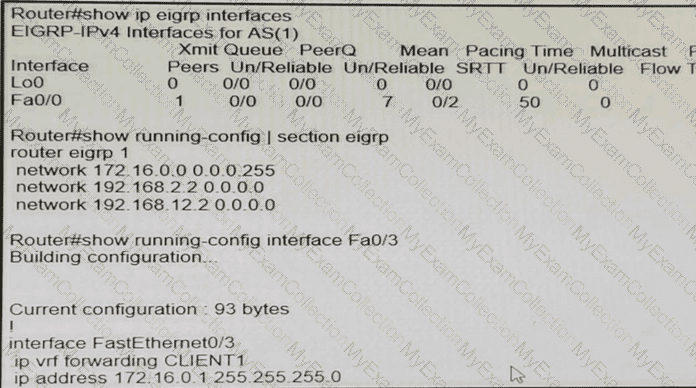
While troubleshooting an EIGRP neighbor adjacency problem, the network engineer notices that the interface connected to the neighboring router is not participating in the EIGRP process. Which action resolves the issues?
Exhibit:
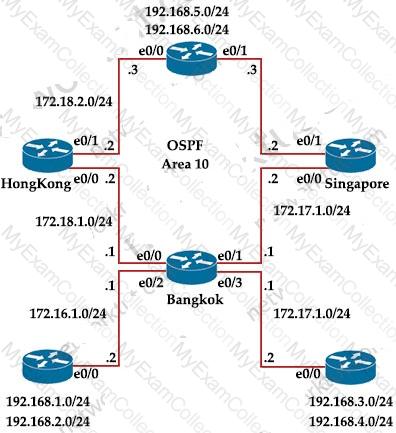
Bangkok is using ECMP to reach to the 192.168.5.0/24 network. The administrator must configure Bangkok in such a way that Telnet traffic from 192.168.3.0/24 and192.168.4.0/24 networks uses the HongKong router as the preferred router. Which set of configurations accomplishes this task?
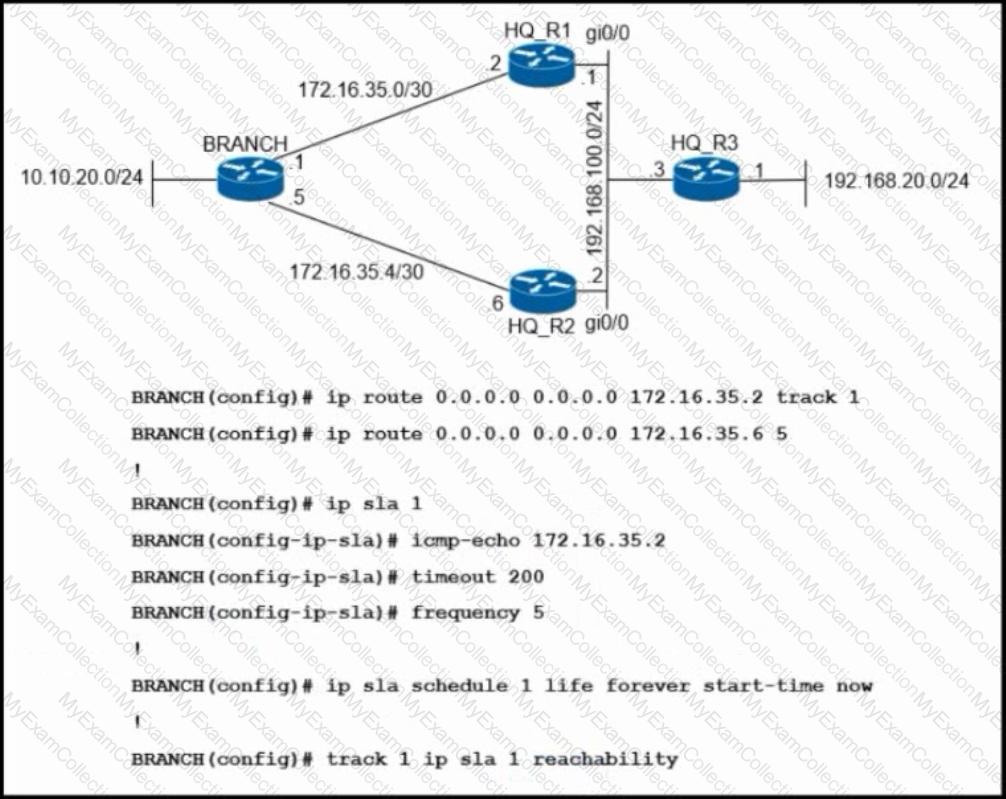
Refer to the exhibit. An engineer has successfully set up a floating static route from the BRANCH router to the HQ network using HQ_R1 as the primary default gateway When the g0/0 goes down on HQ_R1, the branch network cannot reach the HQ network 192.168.20.0/24. Which set of configurations resolves the issue?
Exhibit:
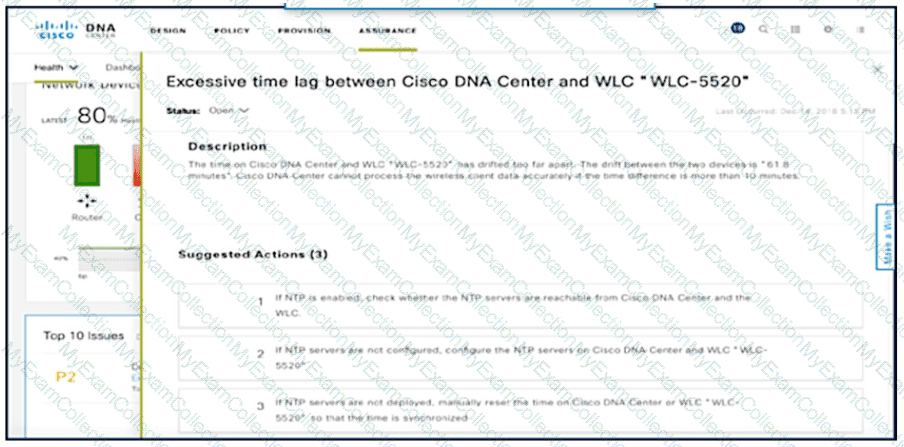
NTP is configured across the network infrastructure and Cisco DNA Center. An NTP issue was reported on the Cisco DNA Center at 17:15. Which action resolves the issue?
Refer to Exhibit.
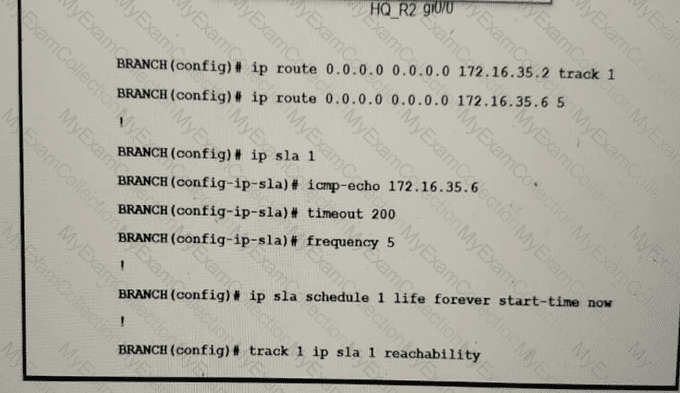
Traffic from the branch network should route through HQ R1 unless the path is unavailable. An engineer tests this functionality by shutting down interface on the BRANCH router toward HQ_R1 router but 192.168.20.0/24 is no longer reachable from the branch router. Which set of configurations resolves the issue?
An engineer needs dynamic routing between two routers and is unable to establish OSPF adjacency. The output of the show ip ospf neighbor command shows that the neighbor state is EXSTART/EXCHANGE. Which action should be taken to resolve this issue?
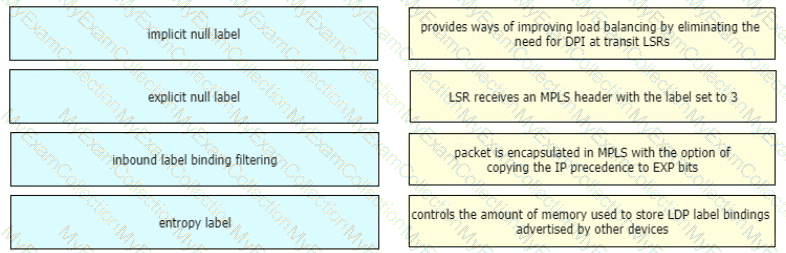
Drag and drop the LDP features from the left onto the descriptions on the right
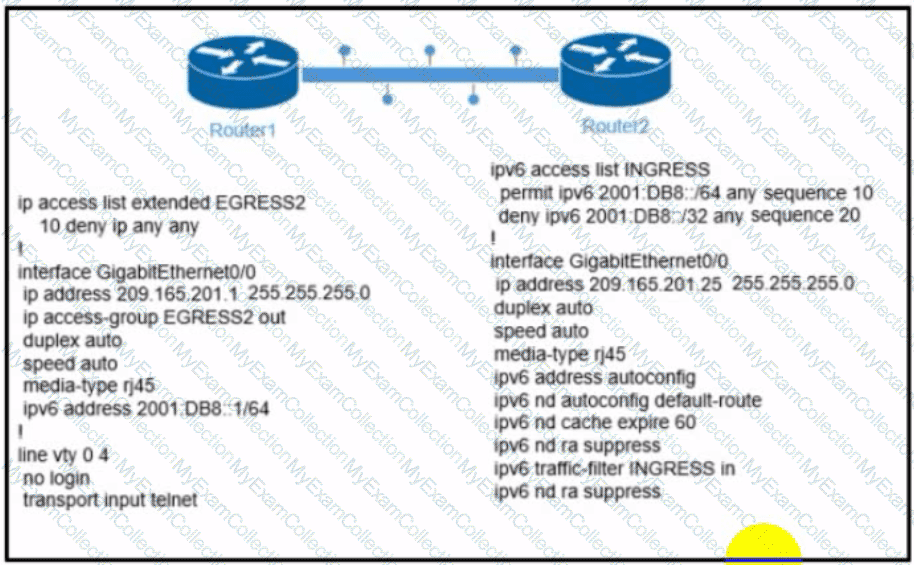
Refer to the exhibit. The engineer configured and connected Router2 to Router1. The link came up but could not establish a Telnet connection to Router1 IPv6 address of 2001:DB8::1. Which configuration allows Router2 to establish a Telnet connection to Router1?
Refer to the exhibit.
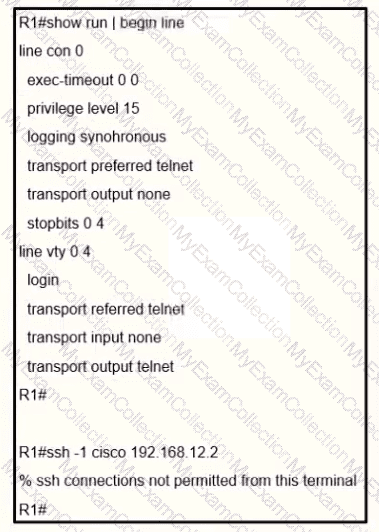
An engineer receives this error message when trying to access another router in-band from the serial interface connected to the console of R1. Which configuration is needed on R1 to resolve this issue?


Refer to the exhibit. A network administrator redistributed the default static route into OSPF toward all internal routers to reach to Internet. Which set of commands restores reachability to the Internet by internal routers?
Refer to the exhibit.
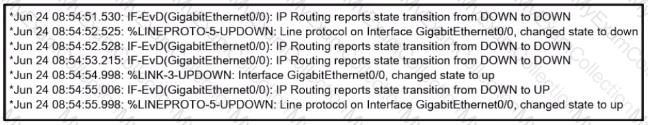
R1 is connected with R2 via GigabitEthernet0/0, and R2 cannot ping R1. What action will fix the issue?
An engineer configured two routers connected to two different service providers using BGP with default attributes. One of the links is presenting high delay, which causes slowness in the network. Which BGP attribute must the engineer configure to avoid using the high-delay ISP link if the second ISP link is up?
An engineer is troubleshooting on the console session of a router and turns on multiple debug commands. The console screen is filled with scrolling debug messages that none of the commands can be verified if entered correctly or display any output. Which action allows the engineer to see entered console commands while still continuing the analysis of the debug messages?
Which two components are needed for a service provider to utilize the LVPN MPLS application? (Choose two.)
Refer to the exhibit.
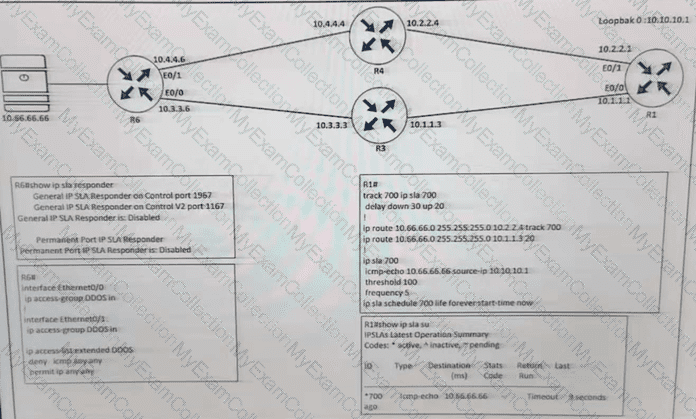
R1 is configured with IP SLA to check the availability of the server behind R6 but it kept failing. Which configuration resolves the issue?
Refer to the exhibit.
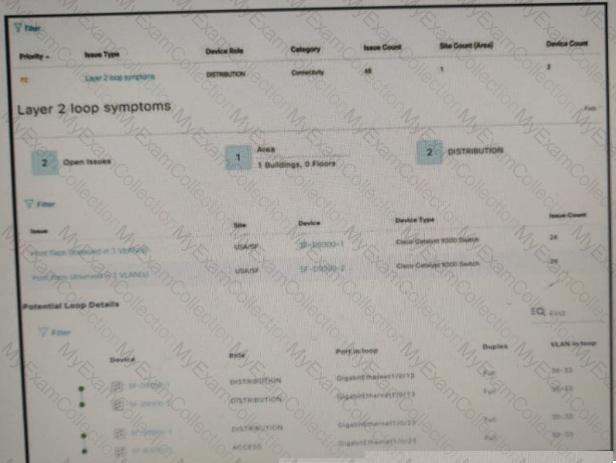

An engineer identifier a Layer 2 loop using DNAC. Which command fixes the problem in the SF-D9300-1 switch?
i.
Which two labet distribution methods are used by routers in MPLS? (Choose two )
Refer to the exhibit.
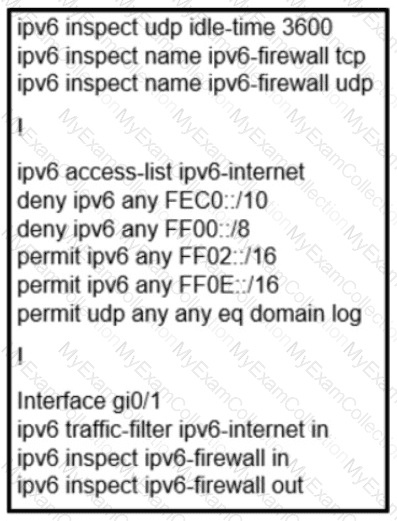
A network administrator configured name resolution for IPv6 traffic to be allowed through an inbound access list. After the access list is applied to resolve the issue, name resolution still did not work. Which action does the network administrator take to resolve the name resolution problem?
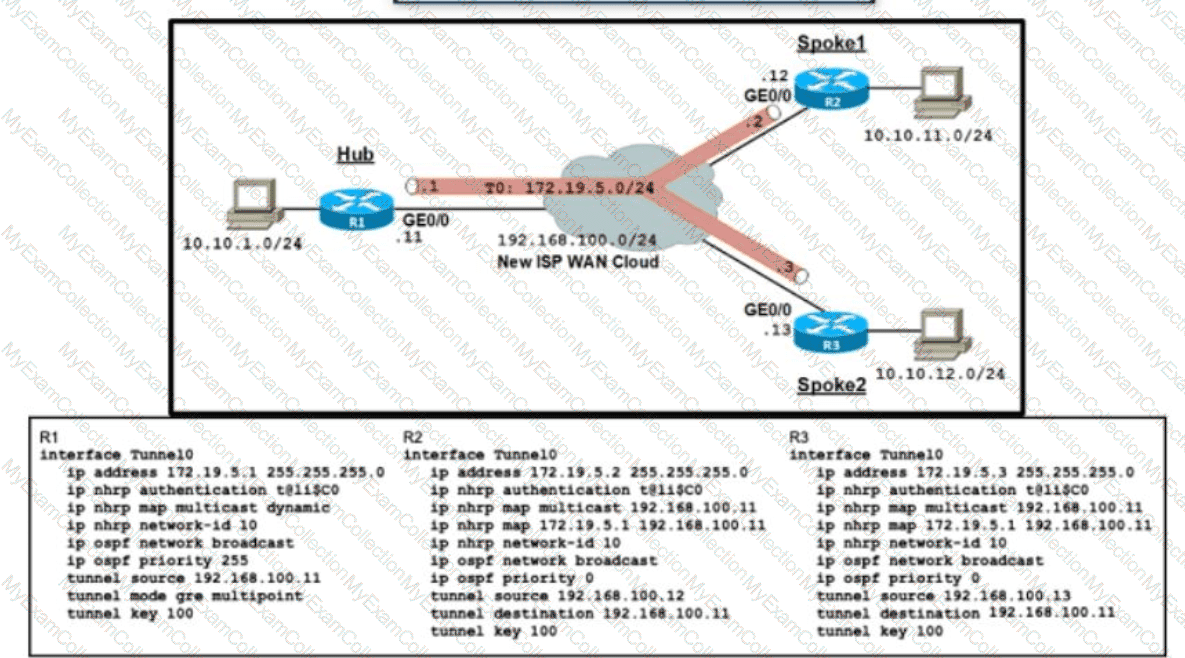
Refer to the exhibit. An organization is installing a new L3 MPLS link to establish DM VPN Phase 2 tunnels between the hub and two spoke routers Which additional configuration should the engineer implement on each device to achieve optimal routing between the spokes?
A)

B)

C)

D)

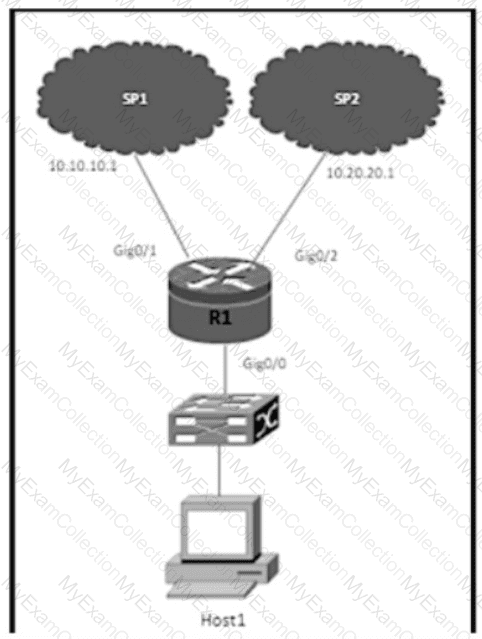
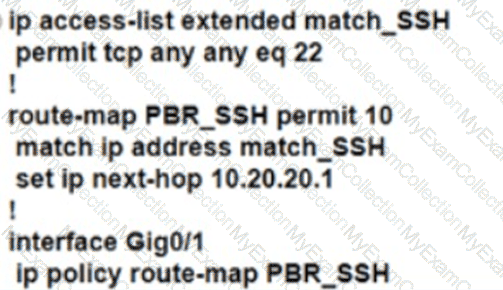
Refer to the exhibit. R1 uses SP1 as the primary path. A network engineer must force all SSH traffic generated from R1 toward SP2. Which configuration accomplishes the task?
A)
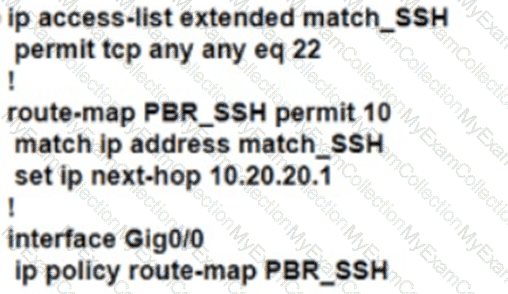
B)
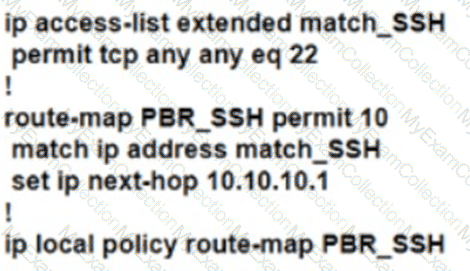
C)

D)
Refer to the exhibit.
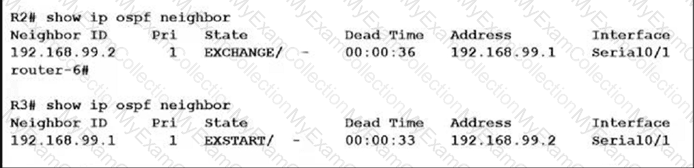
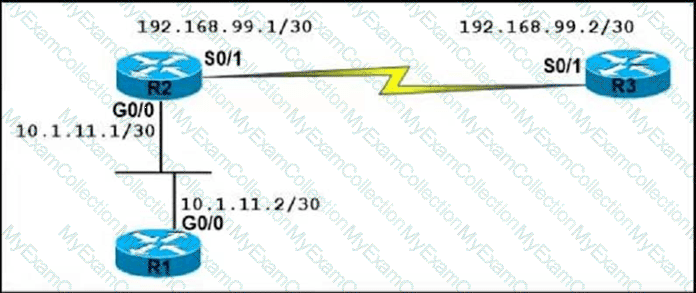
An OSPF neighbor relationship between R2 and R3 is showing stuck in EXCHANGE/EXSTART state. The neighbor is established between R1 and R2. The network engineer can ping from R2 to R3 and vice versa, but the
neighbor is still down. Which action resolves the issue?
Which protocol must be secured with MD-5 authentication across the MPLS cloud to prevent hackers from introducing bogus routers?
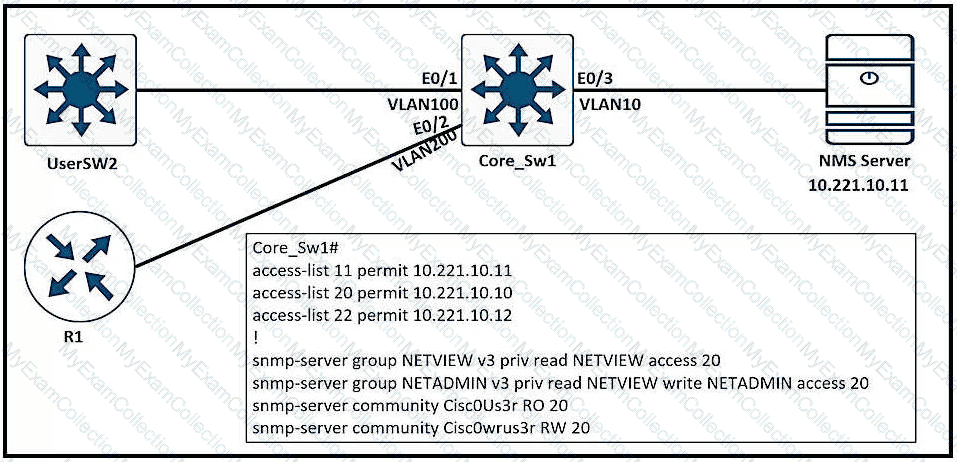
The network administrator configured CoPP so that all HTTP and HTTPS traffic from the administrator device located at 172.16 1.99 toward the router CPU is limited to 500 kbps. Any traffic that exceeds this limit must be dropped.
access-list 100 permit ip host 172.16.1.99 any
!
class-map CM-ADMIN
match access-group 100
!
policy-map PM-COPP
class CM-ADMIN
police 500000 conform-action transmit
!
interface E0/0
service-policy input PM-COPP
CoPP failed to capture the desired traffic and the CPU load is getting higher.
Which two configurations resolve the issue? (Choose two.)
The network administrator configured the router for Control Plane Policrg so that inbound SSH traffic is policed to 500 kbps This policy must apply to traffic coming in from 101010 0<24 and 192 168 10.0/24 networks
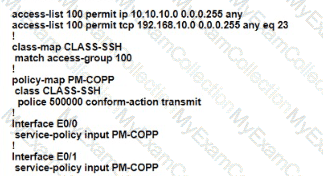
The Control Rane Policing is not applied to SSH traffic and SSH is open to use any bandwidth available. Which configuration resolves this issue?

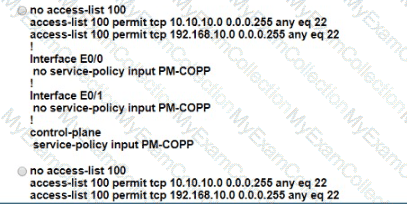
A)
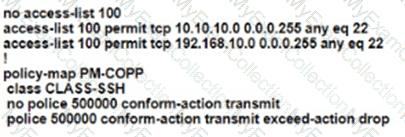
B)
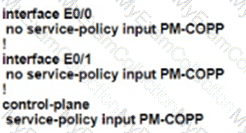
C)
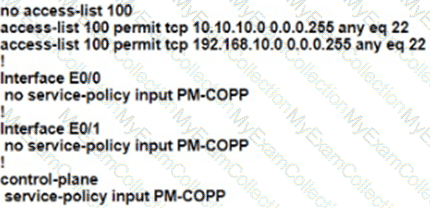
D)
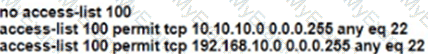
Refer to the exhibit.

A network administrator must configure DMVPN tunnels between the hub and spoke with dynamic spoke-to-spoke tunnel capabilities using EIGRP. Which tunnel interface command must the network administrator configure to establish an EIGRP peer?
An engineer failed to run diagnostic commands on devices using Cisco DNA Center. Which action in Cisco DNA Center resolves the issue?
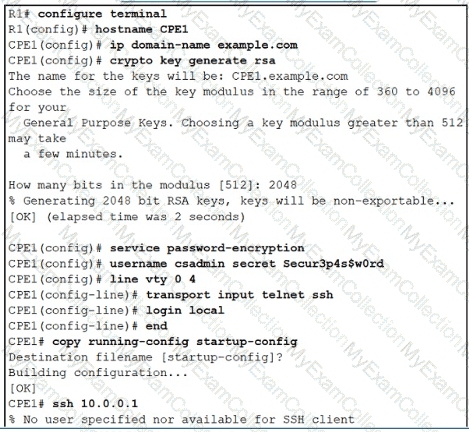
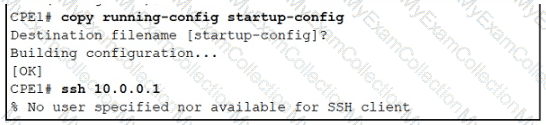
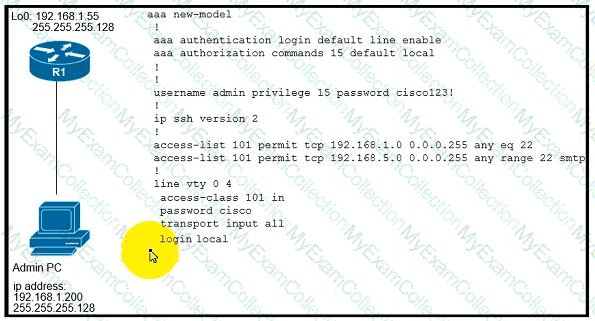
Refer to the exhibit. An administrator must harden a router, but the administrator failed to test the SSH access successfully to the router. Which action resolves the issue?
Refer to the exhibit.
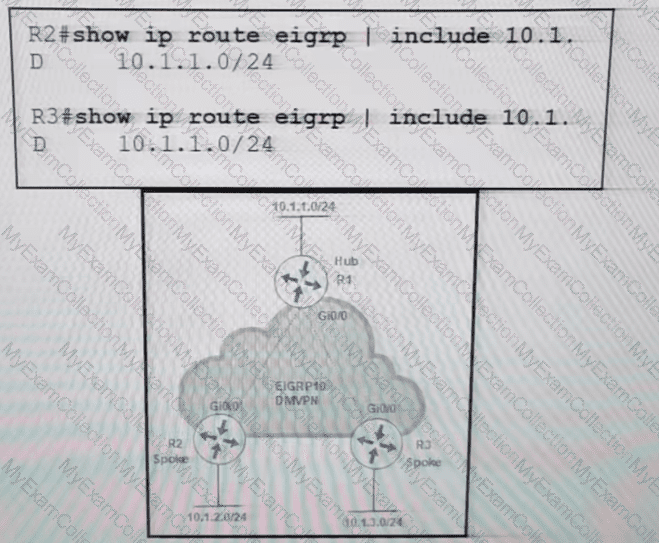
An engineer configures DMVPN and receives the hub location prefix of 10.1.1.0724 on R2 and R3 The R3 prefix of 10 1.3.0/24 is not received on R2. and the R2 prefix 10.1,2.0/24 is not received on R3. Which action reserves the issue?
Refer to the exhibit.
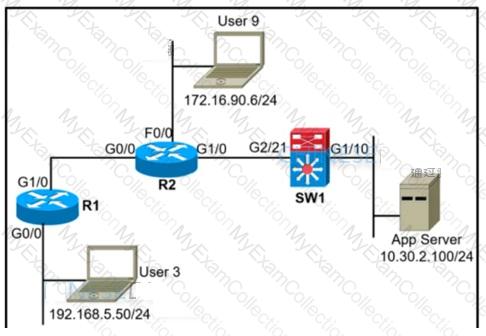
A network administrator must block ping from user 3 to the App Server only. An inbound standard access list is applied to R1 interface G0/0 to block ping. The network administrator was notified that user 3 cannot even ping user 9 anymore. Where must the access list be applied in the outgoing direction to resolve the issue?
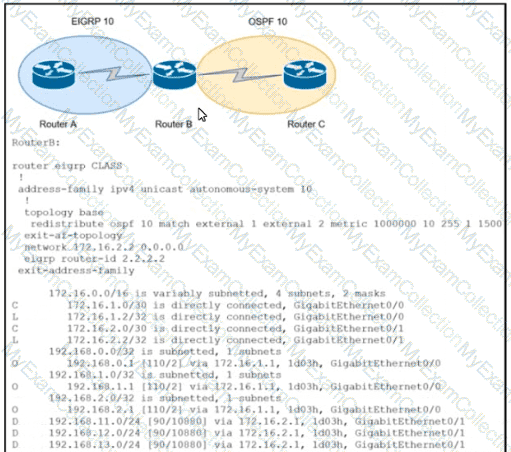
Refer to the exhibit. An engineer configured route exchange between two different companies for a migration project EIGRP routes were learned in router C but no OSPF routes were learned in router A. Which configuration allows router A to receive OSPF routes?
The summary route is not shown in the RouterB routing table after this below configuration on Router_A
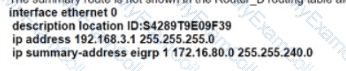 .
.
Which Router_A configuration resolves the issue by advertising the summary route to Router B?

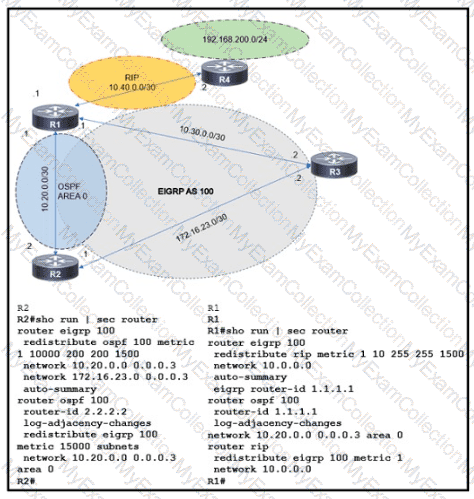
Refer to the exhibit The route to 192 168 200 0 is flapping between R1 and R2 Which set of configuration changes resolves the flapping route?
Refer to the exhibit. An engineer configured user login based on authentication database on the router, but no one can log into the router. Which configuration resolves the issue?
:576
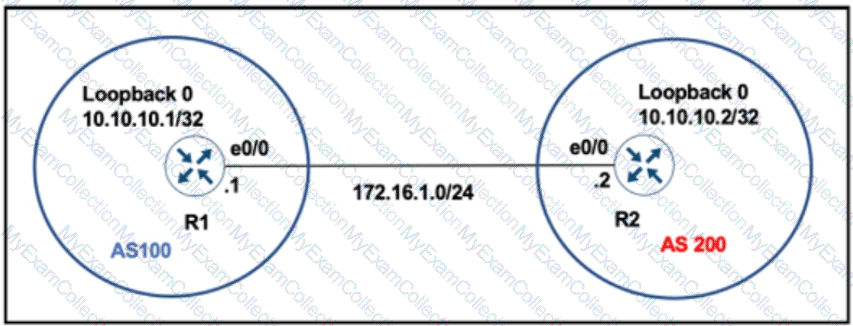
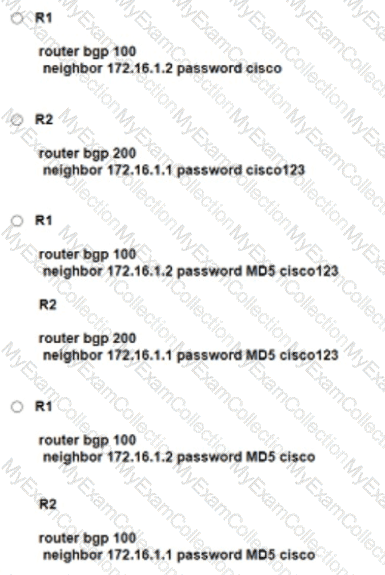
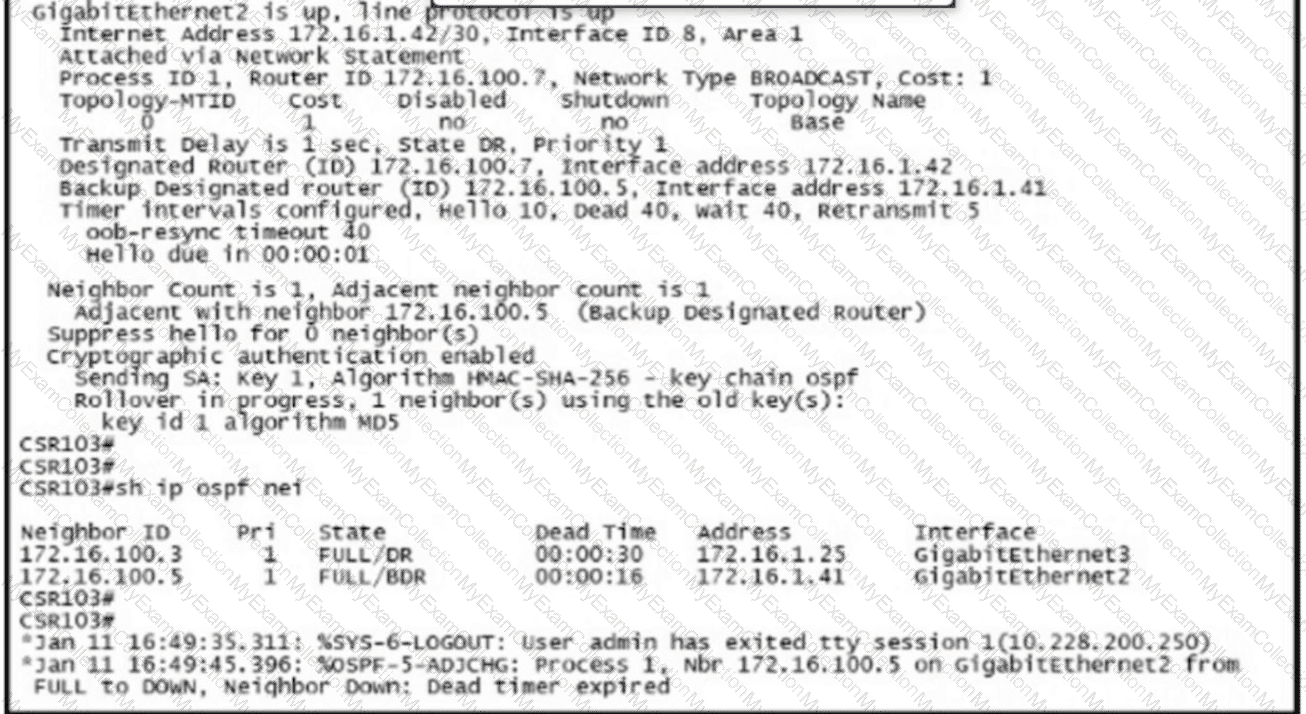
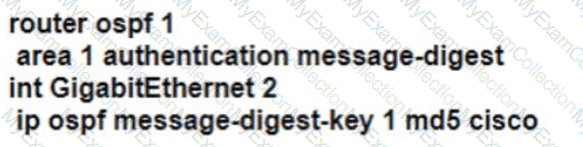
Refer to the exhibit. R1 and R2 have been configured where the neighbor relationship must be authenticatedusmgMD5:
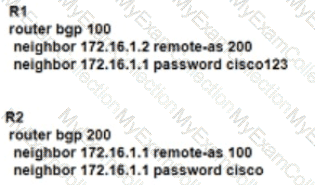
The neighbor relationship is not coming up. Which configuration resolves the issue?
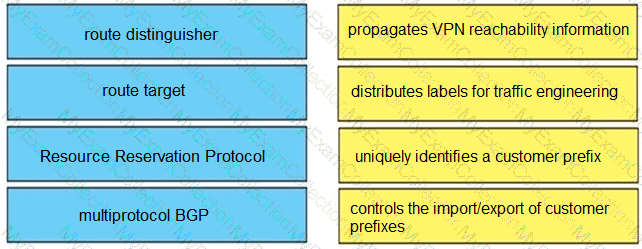
How does an MPLS Layer 3 VPN differentiate the IP address space used between each VPN?
Refer to the exhibit.
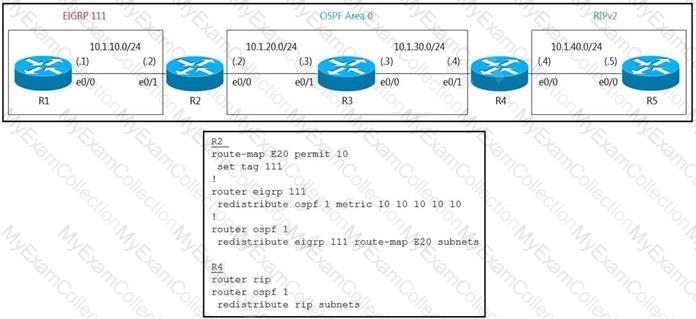
R5 should not receive any routes originated in the EIGRP domain. Which set of configuration changes removes the EIGRP routes from the R5 routing table to fix the issue?
Refer to the exhibit.
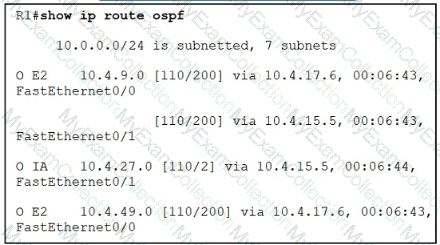
An engineer configures two ASBRs 10 4 17.6 and 10 4 15 5 in an OSPF network to redistribute routes from EIGRP However, both ASBRs show the EIGRP routes as equal costs even though the next-hop router 10 4 17 6 is closer to R1 How should the network traffic to the EIGRP prefixes be sent via 10 4.17.6?
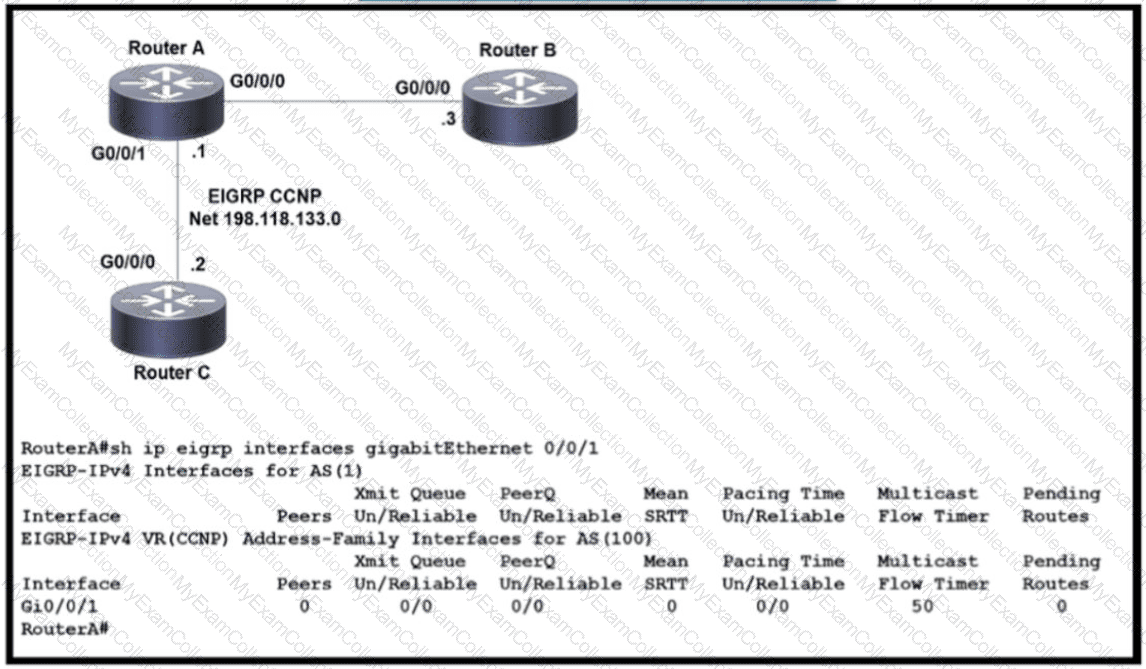
Refer to the exhibit EIGRP adjacency between router A and router C is not working as expected Which two configurations resolve the issue? (Choose two )
A)
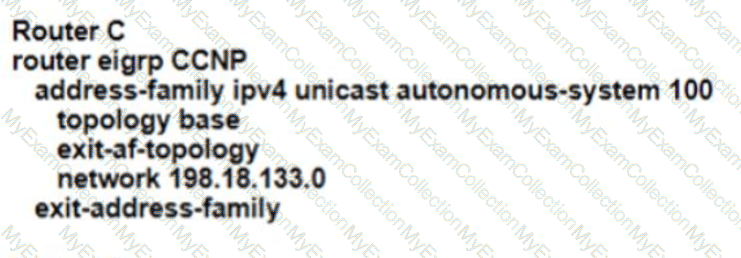
B)
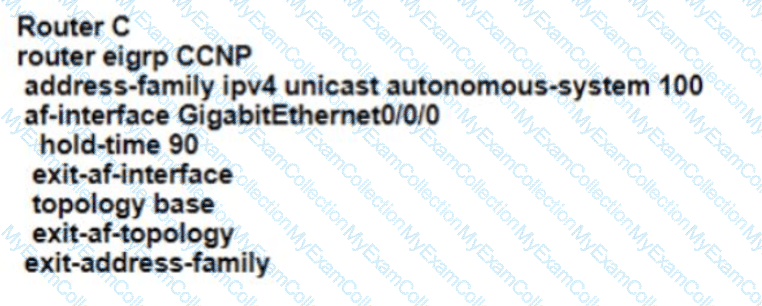
C)
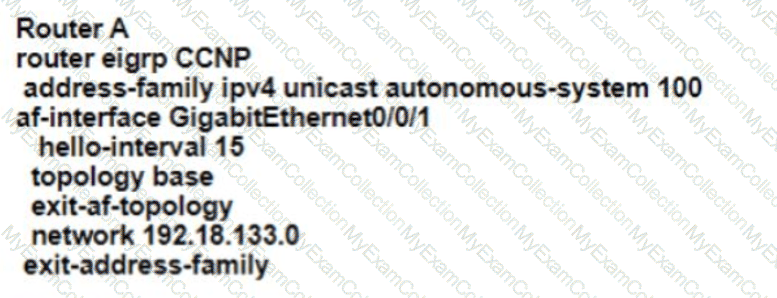
D)

E)
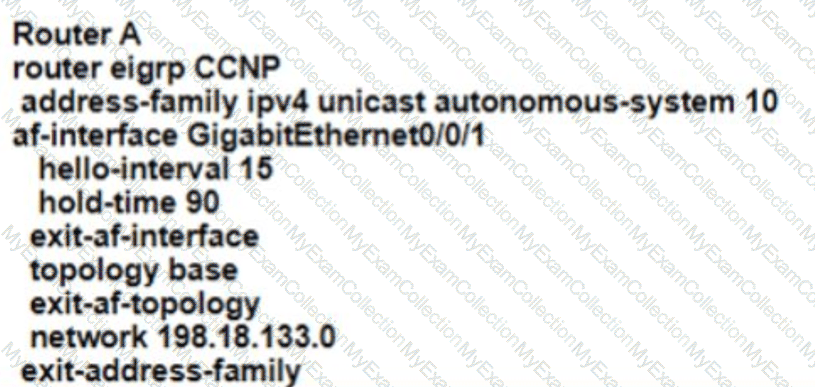
Refer to the exhibit.
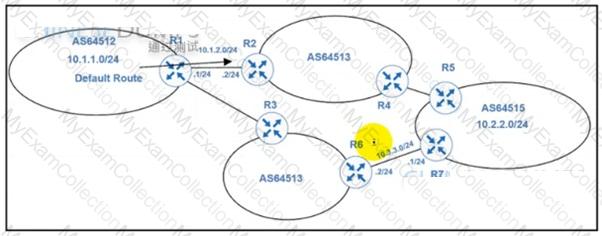
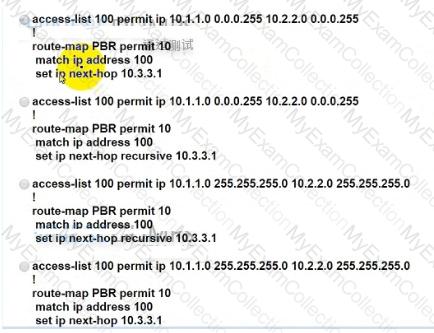
An engineer must configure PBR on R1 to reach to 10.2.2.0/24 via R3 AS64513 as the primary path and a backup route through default route via R2 AS64513. All BGP routes are in the routing table of R1. but a static default route overrides BGP routes. Which PBR configuration achieves the objective?
An engineer configured routing between multiple OSPF domains and introduced a routing loop that caused network instability. Which action resolves the problem?
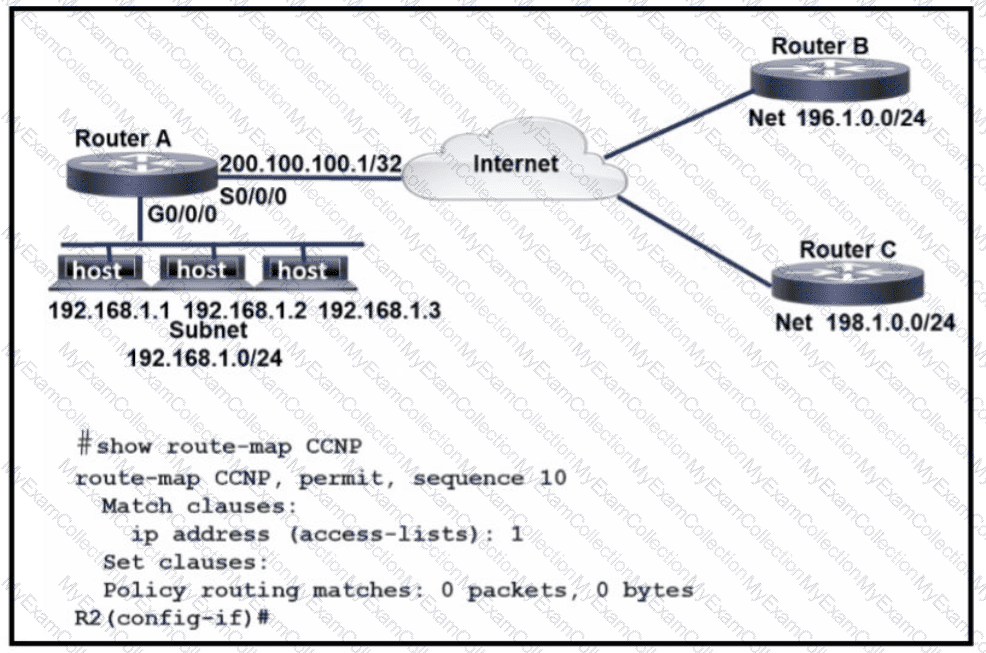
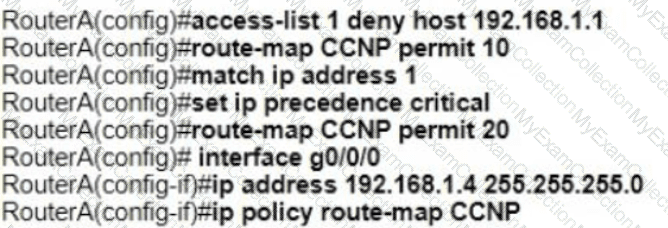
Refer to the exhibit. An engineer configures router A to mark all inside to outside traffic from network 192 168 1 0, except from host 192 168 1 1. with critical IP precedence. The policy did not work as expected Which configuration resolves the issue?
A)
B)
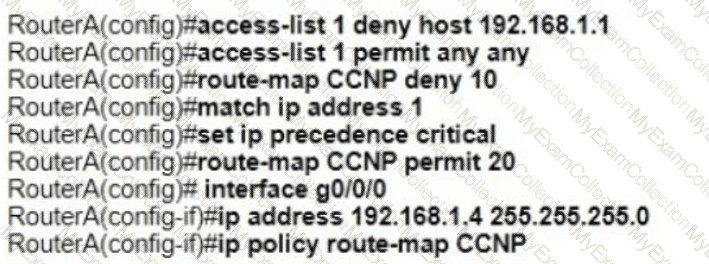
C)
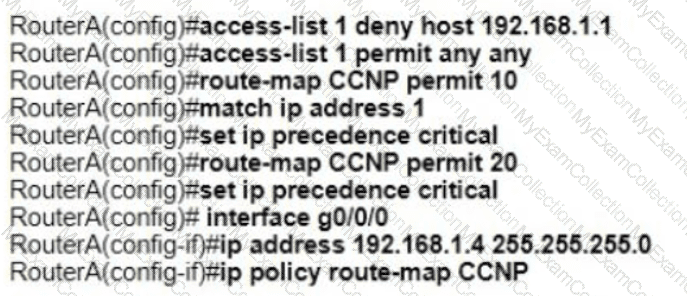
D)


Refer to the exhibit. Router R4 is configured correctly with default OSPF values. A network engineer configured R7 for OSPF. R7 must not be elected as a DR for the segment between R4-R7. The adjacency between R4 and R7 failed to form. Which configuration resolves the issue?

Refer to the exhibit.
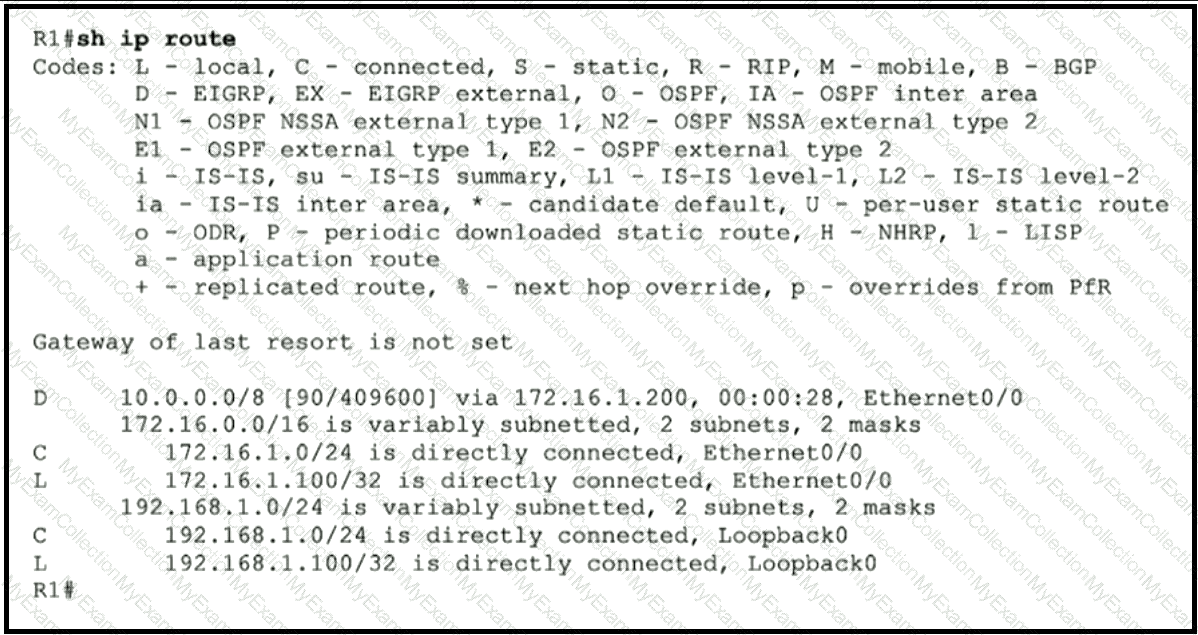
The R2 loopback interface is advertised with RIP and EIGRP using default values. Which configuration changes make R1 reach the R2 loopback using RIP?
The network administrator configured CoPP so that all SNMP traffic from Cisco Prime located at 192.168.1.11 toward the router CPU is limited to 1000 kbps. Any traffic that exceeds this limit must be dropped.
access-list 100 permit udp any any eq 161
!
class-map CM-SNMP
match access-group 100
!
policy-map PM-COPP
class CM-SNMP
police 1000 conform-action transmit
!
control-plane
service-policy input PM-COPP
The network administrator is not getting the desired result for the SNMP traffic and SNMP traffic is getting dropped frequently. Which set of configurations resolves the issue?
Refer to the exhibit.
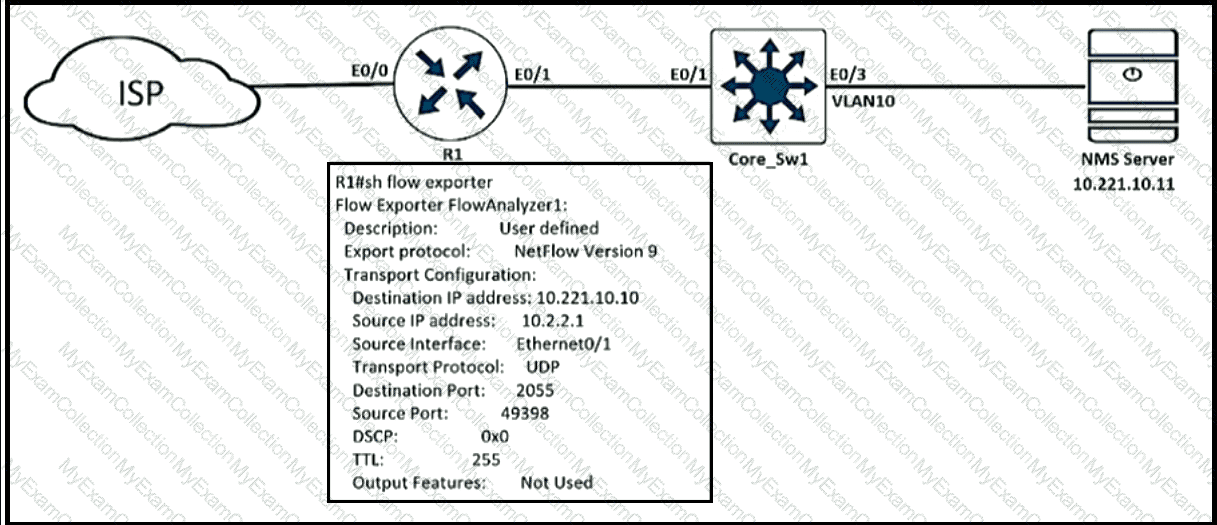
An engineer configured NetFlow on R1, but the NMS server cannot see the flow from R1. Which configuration resolves the issue?
How are CE advertised routes segmented from other CE routers on an MPLS PE router?
Which technique removes the outermost label of an MPLS-tagged packet before the packet is forwarded to an adjacent LER?
Refer to the exhibit.
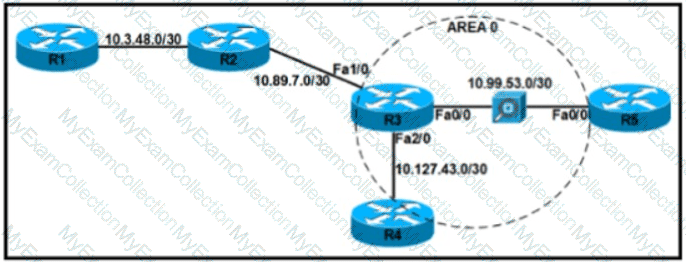
The security department recently installed a monitoring device between routers R3 and R5, which a loss of network connectivity for users connected to R5. Troubleshooting revealed that the monitoring device cannot forward multicast packets. The team already updated R5 with the correct configuration. Which configuration must be implemented on R3 to resolve the problem by ensuring R3 as the DR for the R3-R5 segment?
A)
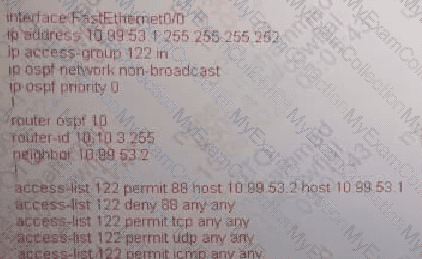
B)
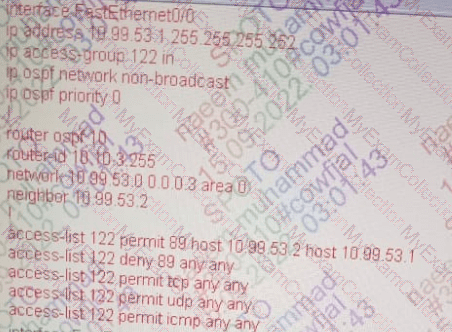
C)
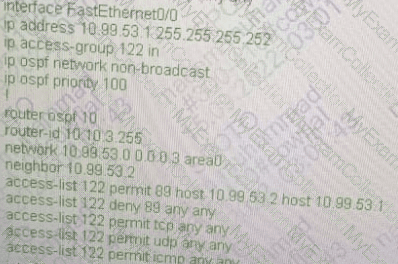
D)

:588
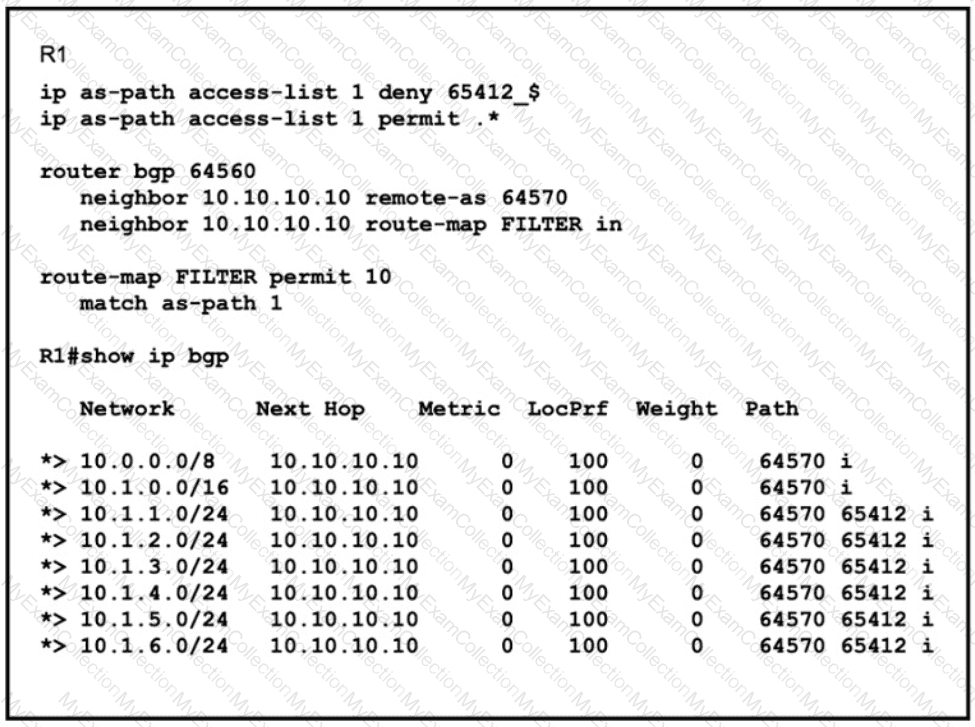
Refer to the exhibit. An engineer must filter prefixes that originate from AS65412. but it is not working correctty. Which configuration must the engineer apply to R1 to resolve the issue?
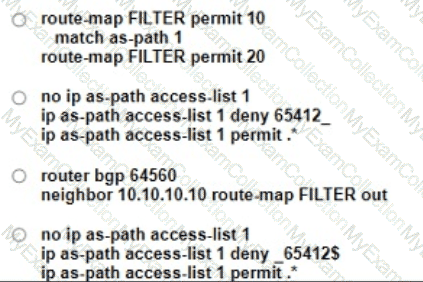
Refer to the exhibit R1 cannot establish a neighbor relationship with R2 Which action resolves the issue"?
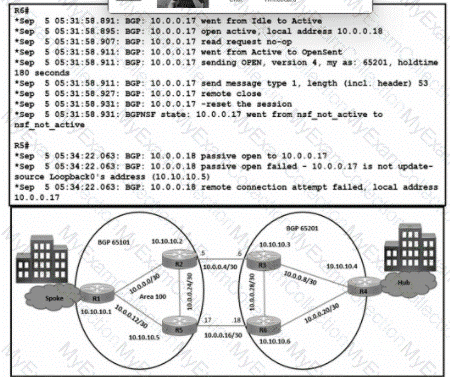
Refer to the exhibit. The traffic from spoke to hub is dropping. The operations team observes:
R2-R3 link is down due to the fiber cut.
R2 and R5 receive traffic from R1 in AS 65101.
R3 and R5 receive traffic from R4 in AS 65201.
Which configuration resolves the issue?
A)

B)

C)
D)
A newly installed spoke router is configured for DMVPN with the ip mtu 1400 command. Which configuration allows the spoke to use fragmentation with the maximum negotiated TCP MTU over GRE?
What are the two reasons for RD and VPNv4 addresses in an MPLS Layer 3 VPN? (Choose two.)
:584
Reler Iothe exhibit The engineer is trying to transfer the newIOSfile to the router R3 but is getting an error Which configuration achieves the file transfer?
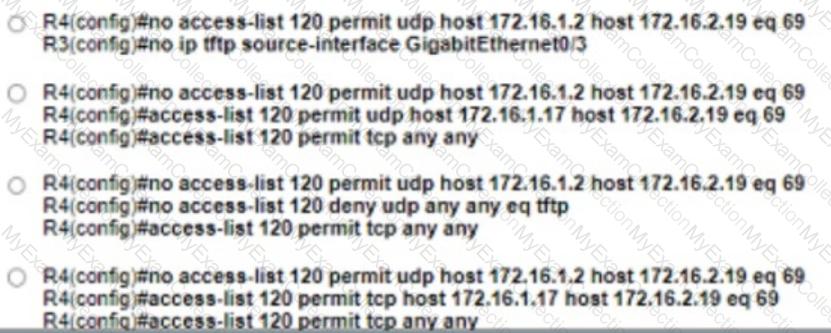
Refer to the exhibit.
During ISP router maintenance, the network produced many alerts because of the flapping interface. Which configuration on R1 resolves the issue?
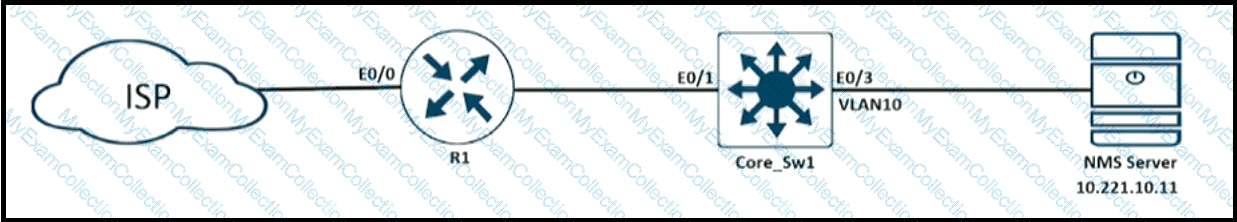
Refer to the exhibit.
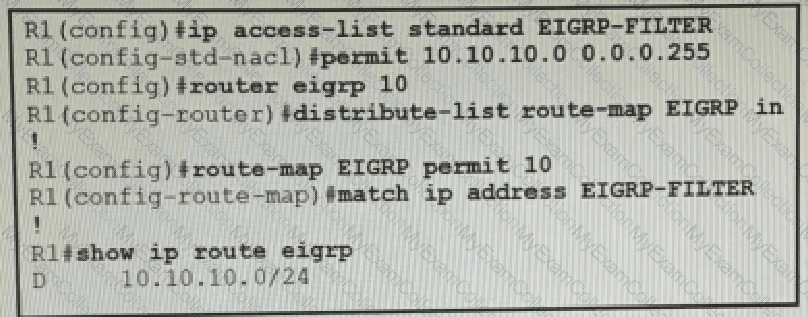
An engineer must filter incoming EIGRP updates to allow only a set of specific prefixes. The distribute list is tested, and it filters out all routes except network 10.10.10.0/24. How should the engineer temporarily allow all prefixes to be learned by the routers again without adjusting the existing access list?
Refer to the exhibit.

An engineer implemented CoPP but did not see OSPF traffic going through it. Which configuration resolves the issue?
R1 and R2 are configured as eBGP neighbor , R1 is in AS100 and R2 is in AS200. R2 is advertising these networks to R1:

The network administrator on R1 must improve convergence by blocking all subnets of 172-16.0.0/16 major network with a mask lower than 23 from coming in, Which set of configurations accomplishes the task on R1?
Drag and drop the operations from the left onto the locations where the operations are performed on the right.
The network administrator is tasked to configure R1 to authenticate telnet connections based on Cisco ISE using RADIUS. ISE has been configured with an IP address of 192.168.1.5 and with a network device pointing towards R1 (192.168.1.1) with a shared secret password of Cisco123. If ISE is down, the administrator should be able to connect using the local database with a username and password combination of admin/cisco123.
The administrator has configured the following on R1:
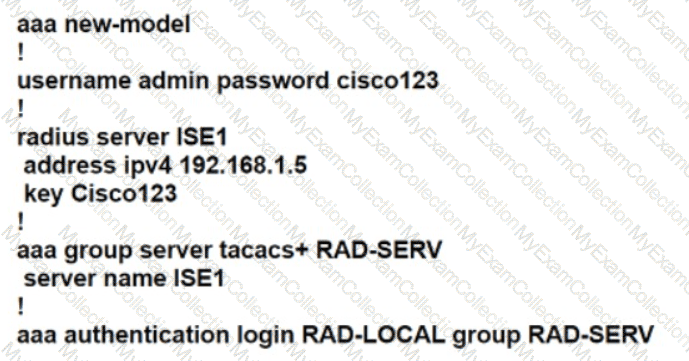
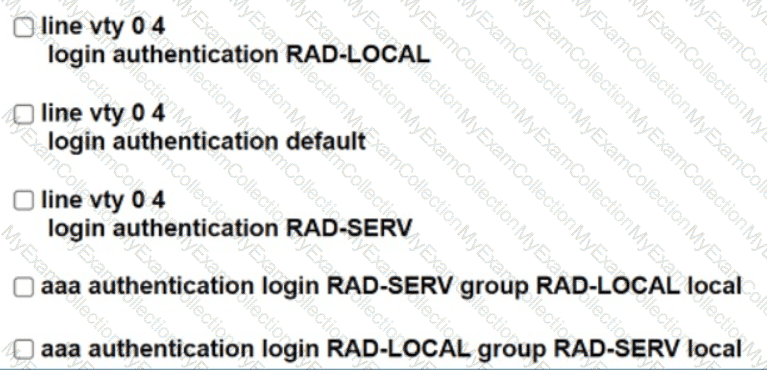
ISE has gone down. The Network Administrator is not able to Telnet to R1 when ISE went down. Which two configuration changes will fix the issue? (Choose two.)
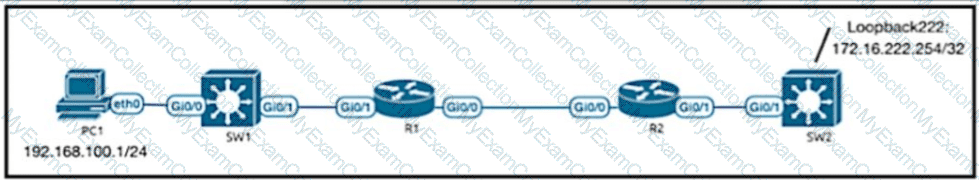
Refer to the exhibit R2 can reach Loopback222, but R1 SW1 and PC1 cannot communicate with 172.16.222 254 R1 and R2 configurations are shown here
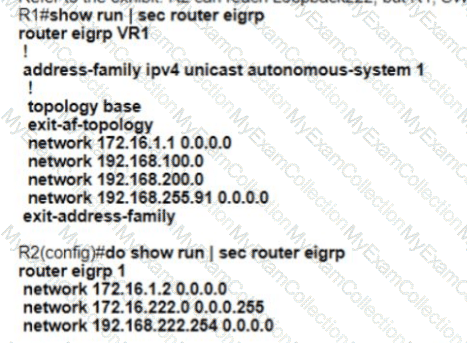
Which EIGRP configuration command resolves the issue?
Refer to the exhibit.
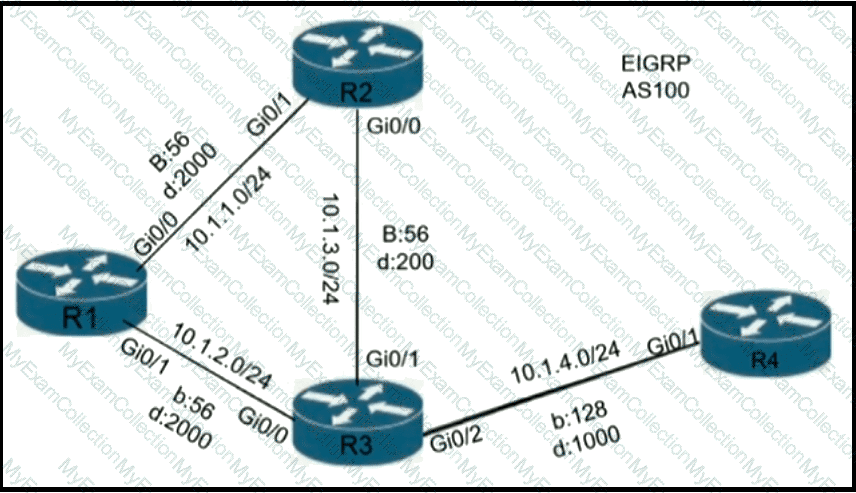
A loop occurs between R1, R2, and R3 while EIGRP is run with poison reverse enabled. Which action prevents the loop between R1, R2, and R3?
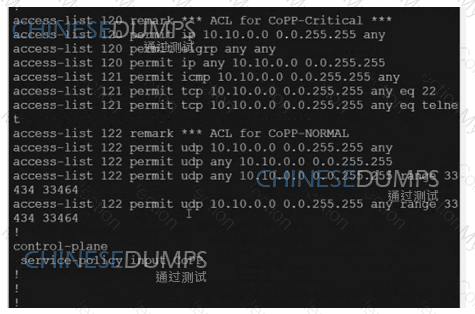
A network is configured with CoPP to protect the CORE router route processor for stability and DDoS protection. As a company policy, a class named class-default is preconfigured and must not be modified or deleted. Troubleshoot CoPP to resolve the issues introduced during the maintenance window to ensure that:
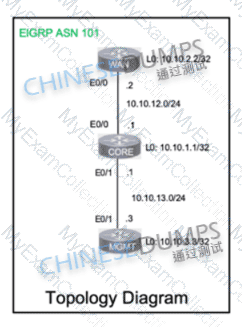
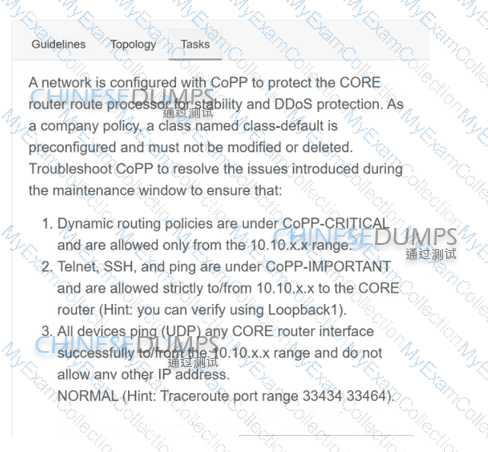
WAN

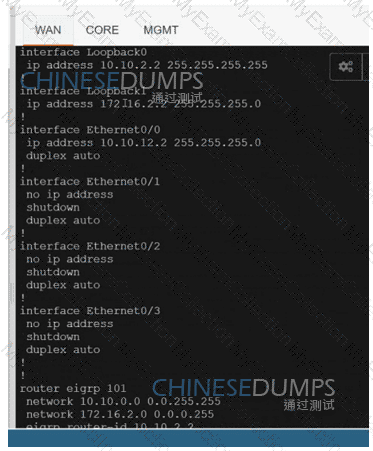
CORE

MGMT
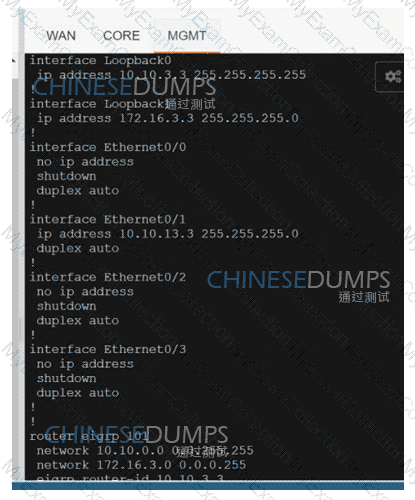
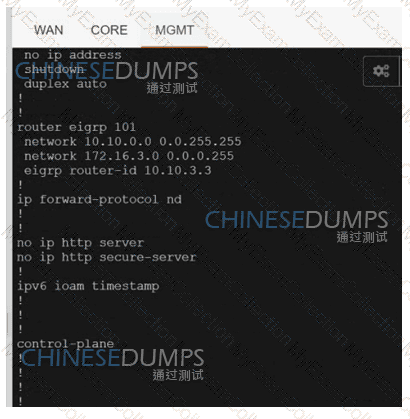
An engineer is creating a policy that overrides normal routing behavior.if the route to a destination of
10.100.100.0/24 is withdrawn from the routing
Table, the policy must direct traffic to a next hop of 10.1 1.1. if the route is present in the routing table, then
normal forwarding must occur. Which
configuration meets the requirements?
:578
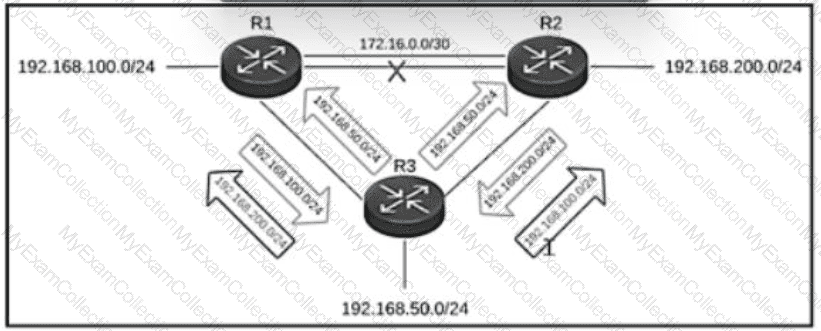
Refer to the exhibit. The primary link between R1 and R2wentdownbutR3isstill advertising the 192.166.200.0/24 networktoR1 and the 192.166.100.0/24 networktoR2, which createsaloop. Which action resolves the issue?
Refer to the exhibit.
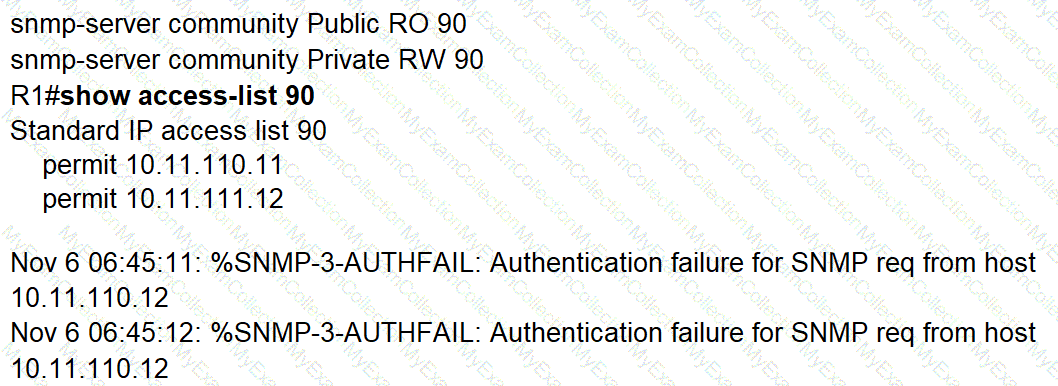
A network administrator notices these console messages from host 10.11.110.12 originating from interface E1/0. The administrator considers this an unauthorized attempt to access SNMP on R1. Which action prevents the attempts to reach R1 E1/0?
:579
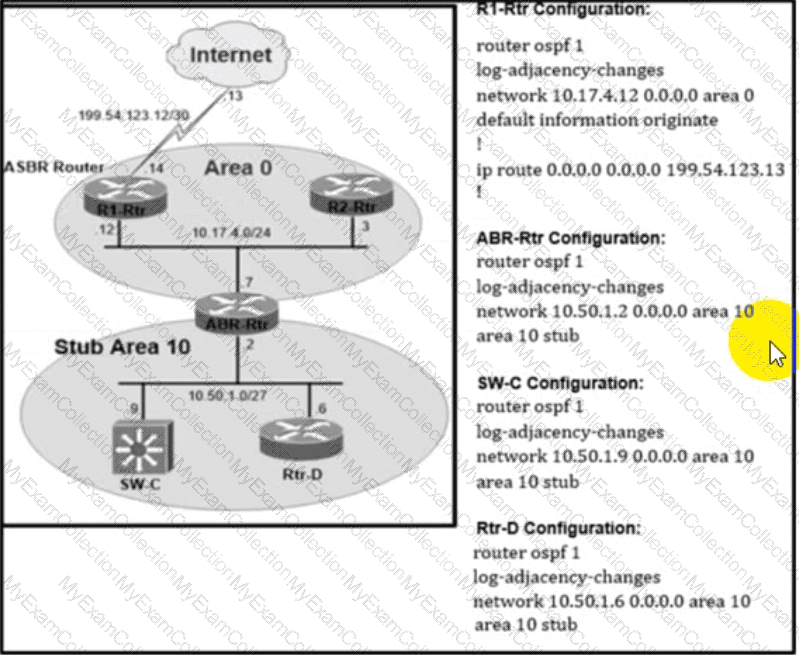
Refer to the exhibit. Router ABR-Rtr is not propagating the internet routes in OSPF area 10. which causes internet reachability problems in the area. Which action resolves the issue?
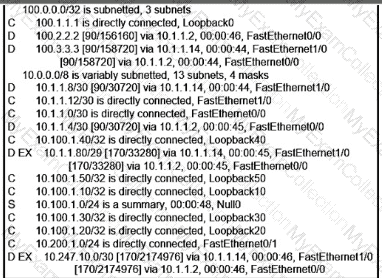
Refer to the exhibit. R1 must advertise all loopback interfaces IP addresses to neighbors, but EIGRP neighbors receive a summary route. Which action resolves the issue?
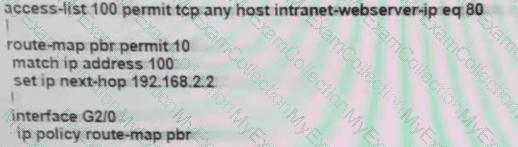
Refer to the exhibit.
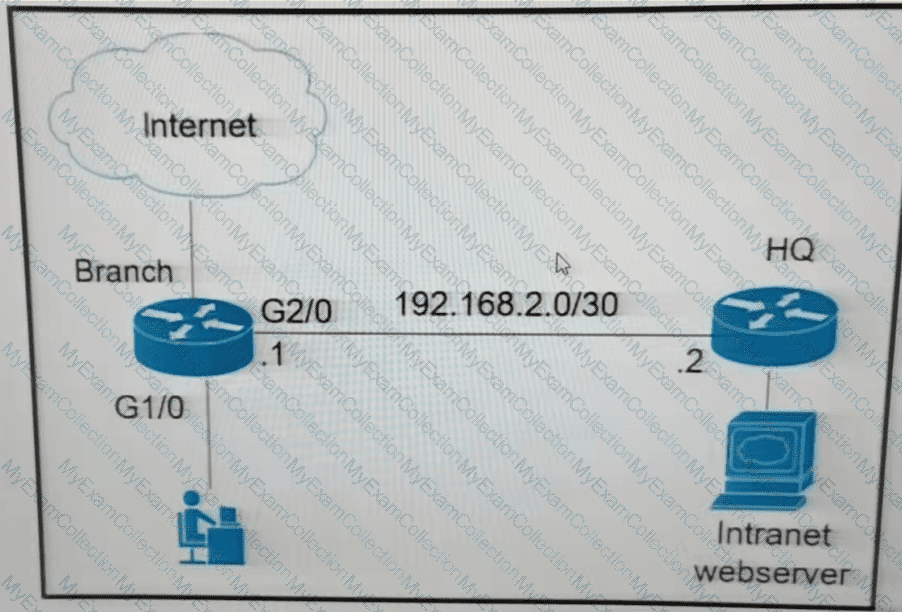
The branch router is configured with a default route toward the internet and has no routes configured for the HQ site that is connected through interface G2/0. The HQ router is fully configured and does not require changes. Which configuration on the branch router makes the intranet website (TCP port 80) available to the branch office users?
A)
B)
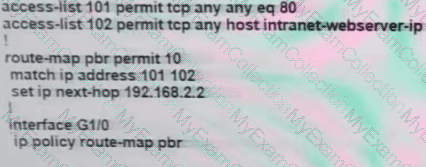
C)
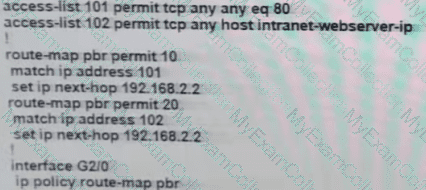
D)
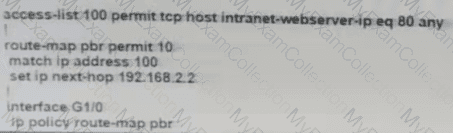
Users were moved from the local DHCP server to the remote corporate DHCP server. After the move,
none of the users were able to use the network.
Which two issues will prevent this setup from working properly? (Choose two)
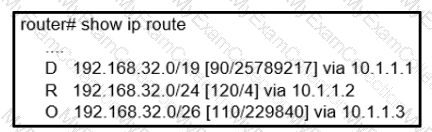
Refer to the exhibit. an engineer is trying to get 192.168.32.100 forwarded through 10.1.1.1, but it was forwarded through 10.1.1.2. What action forwards the packets through 10.1.1.1?
Which SNMP verification command shows the encryption and authentication protocols that are used in
SNMPV3?
Refer to the exhibit.

Which configuration denies Telnet traffic to router 2 from 198A:0:200C::1/64?
A)

B)

C)

D)

Which configuration adds an IPv4 interface to an OSPFv3 process in OSPFv3 address family configuration?
Which Cisco VPN technology can use multipoint tunnel, resulting in a single GRE tunnel interface on the hub, to support multiple connections from multiple spoke devices?




 Graphical user interface, chart Description automatically generated
Graphical user interface, chart Description automatically generated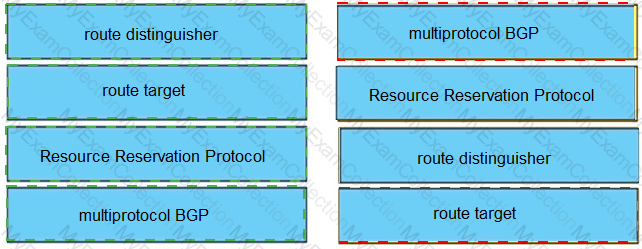
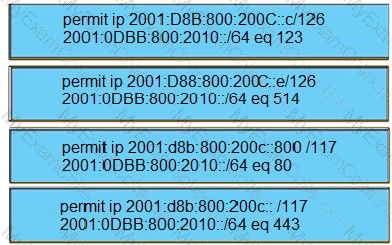
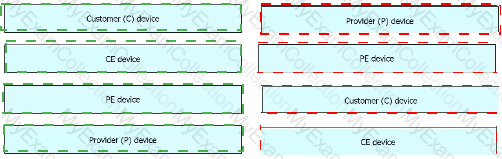


 Table Description automatically generated
Table Description automatically generated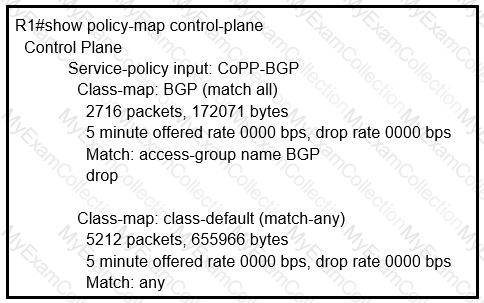

 Graphical user interface, application Description automatically generated
Graphical user interface, application Description automatically generated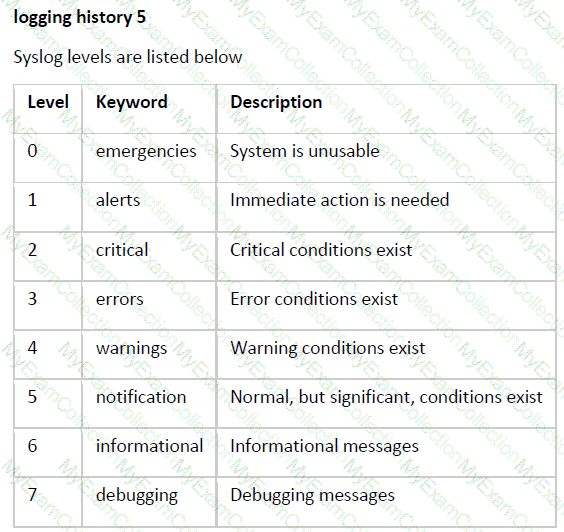


 Diagram Description automatically generated
Diagram Description automatically generated




 A screen shot of a computer
AI-generated content may be incorrect.
A screen shot of a computer
AI-generated content may be incorrect.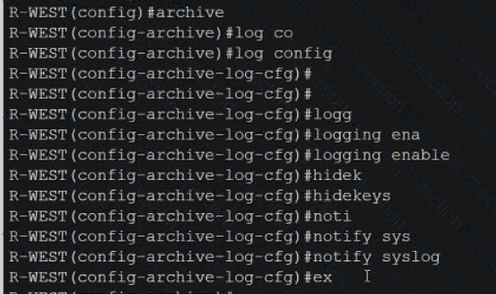 A screen shot of a computer
AI-generated content may be incorrect.
A screen shot of a computer
AI-generated content may be incorrect.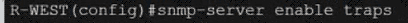

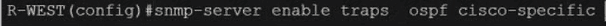

 Text Description automatically generated with medium confidence
Text Description automatically generated with medium confidence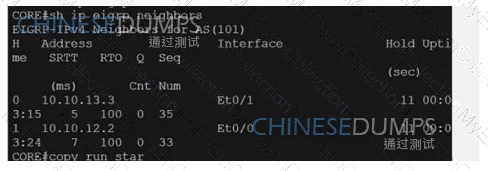 Graphical user interface Description automatically generated with medium confidence
Graphical user interface Description automatically generated with medium confidence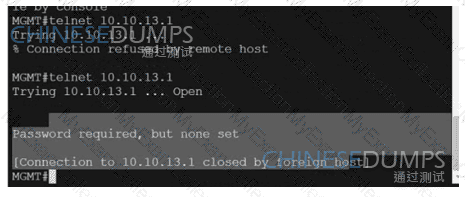 Graphical user interface, text Description automatically generated
Graphical user interface, text Description automatically generated