A large software company runs a small engineering department that is remotely located over a slow WAN connection.
Which option should the company use to install an exported Symantec Endpoint Protection (SEP) package to the remote site using the smallest amount of network bandwidth?
A company deploys Symantec Endpoint Protection client to its sales staff who travel across the country.
Which deployment method should the company use to notify its sales staff to install the client?
An organization recently experienced a definition storm where clients downloaded full definition packages from the management server.
Where can the SEPM increase the amount of content revisions so that clients with older content can get delta updates?
Which Symantec Endpoint Protection Management (SEPM) database option is the default for deployments of fewer than 1,000 clients?
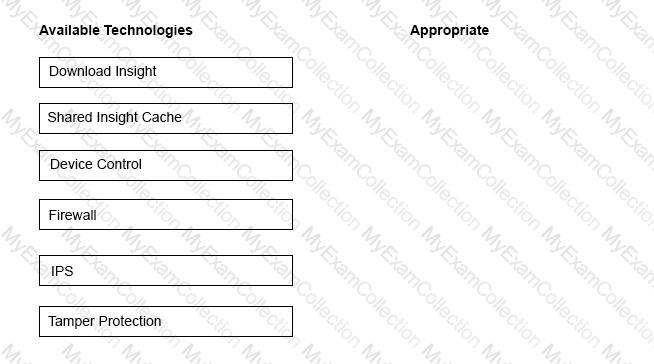
An administrator is unknowingly trying to connect to a malicious website and download a known threat within a .rar file. All Symantec Endpoint Protection technologies are installed on the client’s system.
Drag and drop the technologies to the right side of the screen in the sequence necessary to block or detect the malicious file.
An administrator changes the Virus and Spyware Protection policy for a specific group that disables Auto-Protect. The administrator assigns the policy and the client systems apply the corresponding policy serial number. Upon visual inspection of a physical client system, the policy serial number is correct. However, Auto-Protect is still enabled on the client system.
Which action should the administrator take to ensure that the desired setting is in place on the client?
Where in the Symantec Endpoint Protection (SEP) management console will a SEP administrator find the option to allow all users to enable and disable the client firewall?
Which technology can prevent an unknown executable from being downloaded through a browser session?
Catastrophic hardware failure has occurred on a single Symantec Endpoint Protection Manager (SEPM) in an environment with two SEPMs.
What is the quickest way an administrator can restore the environment to its original state?
Which object in the Symantec Endpoint Protection Manager console describes the most granular level to which a policy can be assigned?
An administrator is troubleshooting a Symantec Endpoint Protection (SEP) replication.
Which component log should the administrator check to determine whether the communication between the two sites is working correctly?
After several failed logon attempts, the Symantec Endpoint Protection Manager (SEPM) has locked the default admin account. An administrator needs to make system changes as soon as possible to address an outbreak, but the admin account is the only account.
Which action should the administrator take to correct the problem with minimal impact to the existing environment?


