The 8IG-IP Administrator generates a qkview using "qkview -SO" and needs to transfer the output file via
SCP.
Which directory contains the output file?
A BIG-IP Administrator is checking the BIG-IP device for known vulnerabilities. What should the 8IG-IP Administrator upload to BIG-IP iHealth for further analysis?
Which log file should the BIG-IP Administrator check to determine if a specific user tried to log in to the 8IG-IP Configuration by utility?
A BIG-IP Administrator reviews the log files to determine the cause of a recent problem and finds the
following entry.
Mar 27.07.58.48 local/BIG-IP notice mcpd {5140} 010707275 Pool member 172.16.20.1.10029 monitor
status down.
What is the cause of this log message?
A BIG-IP Administrator adds new Pool Members into an existing, highly utilized pool. Soon after, there are reports that the application is failing to load for some users. What pool level setting should the BIG-IP Administrator check?
The ICMP monitor has been assigned to all nodes. In addition, all pools have been assigned custom monitors. The pool is marked available. If a pool is marked available (green) which situation is sufficient to cause this?
Refer to the exhibit.

During a planned upgrade lo a BIG-IP HA pair running Active/Standby, an outage to application traffic is reported shortly after the Active unit is forced to Standby Reverting the flower resolves the outage. What should the BIG-IP Administrator modify to avoid an outage during the next for over event?
Assume a client's traffic is being processed only by a NAT; no SNAT or virtual server processing takes place. Also assume that the NAT definition specifies a NAT address and an origin address while all other settings are left at their defaults. If a client were to initiate traffic to the NAT address, what changes, if any, would take place when the BIG-IP processes such packets?
A site wishes to perform source address translation on packets from some clients but not others. The determination is not based on the client's IP address, but on the virtual servers their packets arrive on. What could best accomplish this goal?
A BIG-IP Administrator needs to configure the BIG-IP system to perform load balancing for FTP servers
running passive mode FTP.
How should the administrator configure the Virtual Server to perform this load balancing?
All pool members are online. All other virtual server settings are at default What might after the load balancing behavior?
A VLAN has the following objects configured:
Self-IP 10.10.10.100 with port lockdown set to Allow default
Virtual server 10.10.10.100:443 with UDP profile enabled
Virtual server 10.10.10.0/24 port forwarding virtual server
Global destination NAT forwarding 10.10.10.100 to internal server 172.168.10.100
Which object will process this request when https://10.10.10.100 is entered into a browser?
A pool of four servers has been partially upgraded for two new servers with more memory and CPU capacity. The BIG-IP Administrator must change the load balance method to consider more connections for the two new servers. Which load balancing method considers pool member CPU and memory load?
A virtual server is defined per the charts. The last five client connections were to members C, D, A, B, B. Given the conditions shown in the above graphic, if a client with IP address 205.12.45.52 opens a connection to the virtual server, which member will be used for the connection.
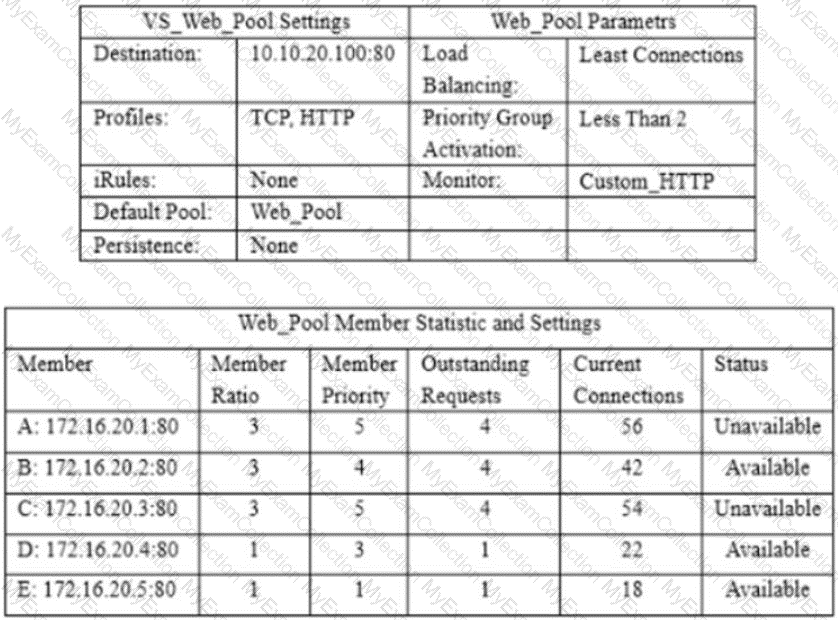
Active connections to pool members are unevenly distributed. The load balancing method is Least Connections (member) Priority Group Activation is disabled. What is a potential cause of the event distribution?
New Syslog servers have been deployed in an organization. The BIG-IP Administrator must reconfigure the BIG-IP system to send log messages to these servers.
In which location in the Configuration Utility can the BIG-IP Administrator make the needed configuration changes to accomplish this?
A BIG-IP Administrator needs to apply a license to the BIG-IP system to increase the user count from the
base license.
Which steps should the BIG-IP Administrator?
Refer to the exhibit.
The BIG-IP Administrator has modified an iRule on one device of an HA pair. The BIG-IP Administrator
notices there is NO traffic on the BIG-IP device in which they are logged into.
What should the BIG-IP Administrator do to verify if the iRule works correctly?
A BIG-IP Administrator plans to resolve a non-critical issue with a BIG-IP device in 2 weeks. What Severity level should be assigned to this type of F5 support ticket?
A BIG-IP Administrator suspects that one of the BIG-IP device power supplies is experiencing power
outages.
Which log file should the BIG-IP Administrator check to verify the suspicion?
A BIGJP Administrator needs to load a UCS file but must exclude the license file. How should the administrator perform this task?
A BIG-IP Administrator finds the following log entry after a report of user issues connecting to a virtual server:
01010201: 2: Inet port exhaustion on 10.70.110.112 to 192.28.123.250:80 (proto 6)
How should the BIG-IP Administrator modify the SNAT pool that is associated with the virtual server?
Assuming there are open connections through an active system's NAT and a fail over occurs, by default, what happens to those connections?

An IT support engineer needs to access and modify Virtual Servers in three partitions (Common /Banking and Dev) daily on a BIG-IP device. The company operates a Least Privilege access policy. What level of access does the IT support engineer need to ensure completion of daily roles?
A 8IG-IP Administrator configures a Virtual Server to load balance traffic between 50 webservers for an
ecommerce website Traffic is being load balanced using the Least Connections (node) method.
The webserver administrators report that customers are losing the contents from their shopping carts
and are unable to complete their orders.
What should the BIG-IP Administrator do to resolve the issue?
A BIG-IP Administrator wants to add the ASM Module to an HA pair of BIG-IP devices. The BIG-IP Administrator has already installed a new Add-On License on both devices in the HA pair. What should the BIG-IP Administrator do next to use the module?
A BIG-IP Administrator is performing maintenance on the active BIG-IP device of an HA pair. The BIG-IP
Administrator needs to minimize traffic disruptions.
What should the BIG-IP Administrator do to start the maintenance activity?
A BIG-IP Administrator needs to install a HotFix on a standalone BIG-IP device, which has HD1.1 as the Active Boot Location. The BIG-IP Administrator has already re-activated the license and created an UCS archive of the configuration. In which sequence should the BIG-IP Administrator perform the remaining steps?
The current status of a given pool is offline (red). Which condition could explain that state? Assume the descriptions below include all monitors assigned for each scenario.
The BIG-IP Administrator generates QKView using tmsh command "qkview -SO". In which directory does the BIG-IP appliance save the QKView?


