Refer to the exhibit.

This request was sent to a web application server driven by a database. Which type of web server attack is represented?
What are the two differences between stateful and deep packet inspection? (Choose two )
Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
A user received a targeted spear-phishing email and identified it as suspicious before opening the content. To which category of the Cyber Kill Chain model does to this type of event belong?
Refer to the exhibit.
What is the potential threat identified in this Stealthwatch dashboard?
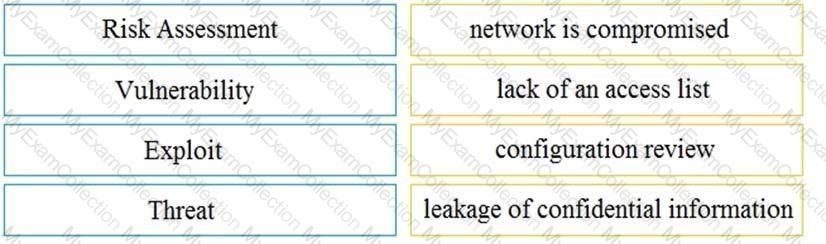
Drag and drop the security concept from the left onto the example of that concept on the right.
What describes the impact of false-positive alerts compared to false-negative alerts?
Which metric is used to capture the level of access needed to launch a successful attack?
Which HTTP header field is used in forensics to identify the type of browser used?
Drag and drop the security concept on the left onto the example of that concept on the right.
How does an SSL certificate impact security between the client and the server?
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
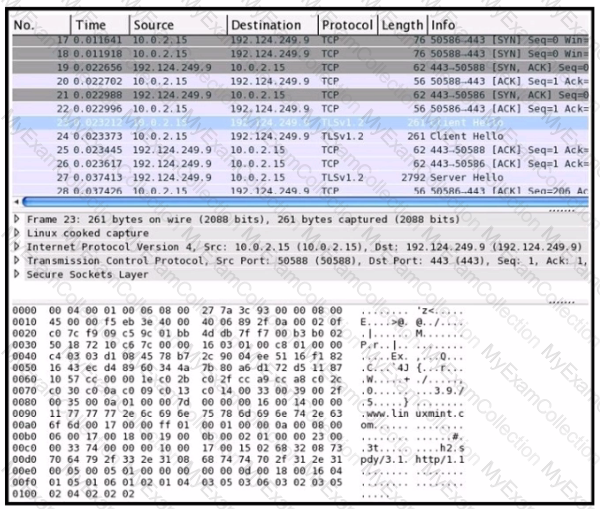
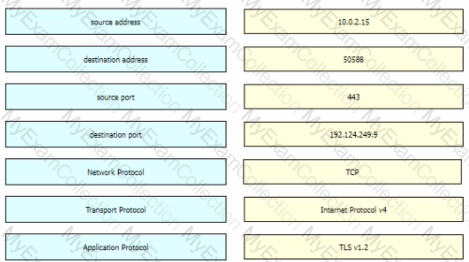
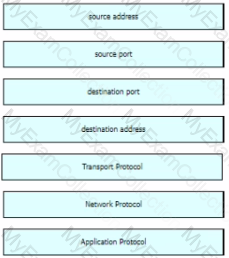
Refer to the exhibit Drag and drop the element names from the left onto the corresponding pieces of the PCAP file on the right.
Which attack method is being used when an attacker tries to compromise a network with an authentication system that uses only 4-digit numeric passwords and no username?
Which metric should be used when evaluating the effectiveness and scope of a Security Operations Center?
Refer to the exhibit.
Which kind of attack method is depicted in this string?
Which vulnerability type is used to read, write, or erase information from a database?
Refer to the exhibit.
What is the potential threat identified in this Stealthwatch dashboard?
An employee reports that someone has logged into their system and made unapproved changes, files are out of order, and several documents have been placed in the recycle bin. The security specialist reviewed the system logs, found nothing suspicious, and was not able to determine what occurred. The software is up to date; there are no alerts from antivirus and no failed login attempts. What is causing the lack of data visibility needed to detect the attack?
A network engineer noticed in the NetFlow report that internal hosts are sending many DNS requests to external DNS servers A SOC analyst checked the endpoints and discovered that they are infected and became part of the botnet Endpoints are sending multiple DNS requests but with spoofed IP addresses of valid external sources What kind of attack are infected endpoints involved in1?
The SOC team has confirmed a potential indicator of compromise on an endpoint. The team has narrowed the executable file's type to a new trojan family. According to the NIST Computer Security Incident Handling Guide, what is the next step in handling this event?
An engineer must investigate suspicious connections. Data has been gathered using a tcpdump command on a Linux device and saved as sandboxmatware2022-12-22.pcaps file. The engineer is trying to open the tcpdump in the Wireshark tool. What is the expected result?
Exhibit.
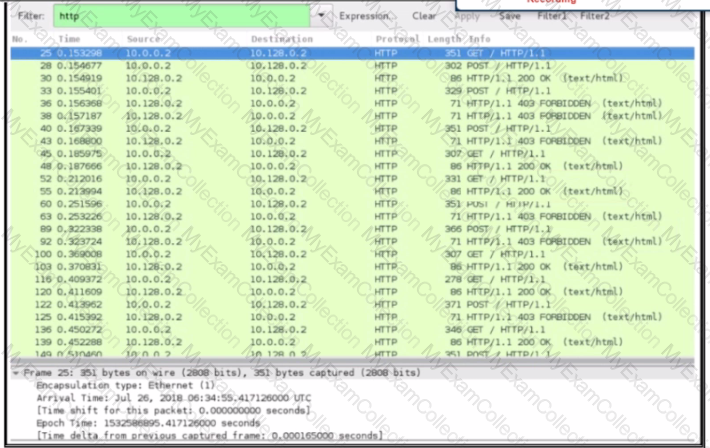
An engineer received a ticket about a slowdown of a web application, Drug analysis of traffic, the engineer suspects a possible attack on a web server. How should the engineer interpret the Wiresharat traffic capture?
What is the difference between the rule-based detection when compared to behavioral detection?
What is the difference between inline traffic interrogation (TAPS) and traffic mirroring (SPAN)?
Refer to the exhibit.
An engineer received an event log file to review. Which technology generated the log?
Refer to the exhibit.
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
When trying to evade IDS/IPS devices, which mechanism allows the user to make the data incomprehensible without a specific key, certificate, or password?
Why should an engineer use a full packet capture to investigate a security breach?
A SOC analyst detected connections to known C&C and port scanning activity to main HR database servers from one of the HR endpoints via Cisco StealthWatch. What are the two next steps of the SOC team according to the NISTSP800-61 incident handling process? (Choose two)
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor.
Which type of evidence is this?
STION NO: 102
Refer to the exhibit.
What is the potential threat identified in this Stealthwatch dashboard?
Refer to the exhibit.
An analyst was given a PCAP file, which is associated with a recent intrusion event in the company FTP server Which display filters should the analyst use to filter the FTP traffic?
Which action should be taken if the system is overwhelmed with alerts when false positives and false negatives are compared?
A malicious file has been identified in a sandbox analysis tool.
Which piece of information is needed to search for additional downloads of this file by other hosts?
An engineer needs to configure network systems to detect command and control communications by decrypting ingress and egress perimeter traffic and allowing network security devices to detect malicious outbound communications. Which technology should be used to accomplish the task?
An engineer needs to have visibility on TCP bandwidth usage, response time, and latency, combined with deep packet inspection to identify unknown software by its network traffic flow. Which two features of Cisco Application Visibility and Control should the engineer use to accomplish this goal? (Choose two.)
A user reports difficulties accessing certain external web pages. When an engineer examines traffic to and from the external domain in full packet captures, they notice that many SYNs have the same sequence number, source, and destination IP address, but they have different payloads. What is causing this situation?
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
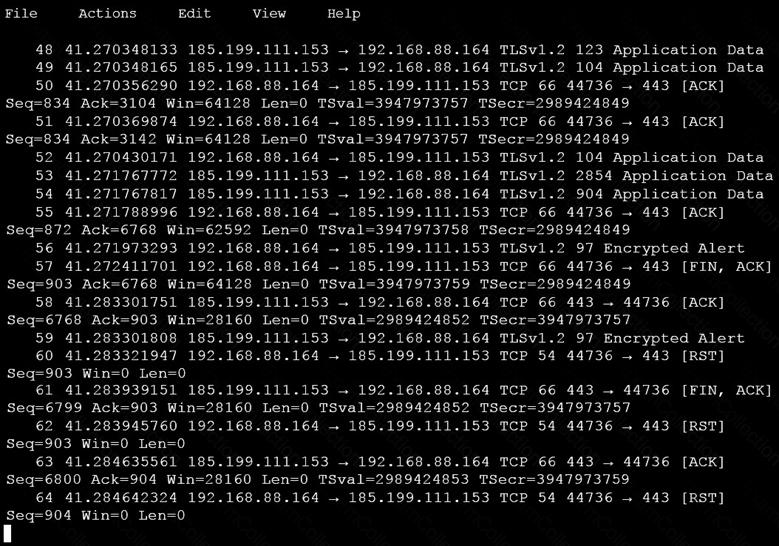
Which obfuscation technique is the attacker using?
An engineer is investigating a case of the unauthorized usage of the “Tcpdump†tool. The analysis revealed that a malicious insider attempted to sniff traffic on a specific interface. What type of information did the malicious insider attempt to obtain?
What is personally identifiable information that must be safeguarded from unauthorized access?
Drag and drop the type of evidence from the left onto the description of that evidence on the right.
A network engineer discovers that a foreign government hacked one of the defense contractors in their home country and stole intellectual property. What is the threat agent in this situation?
An investigator is examining a copy of an ISO file that is stored in CDFS format. What type of evidence is this file?
Which security technology guarantees the integrity and authenticity of all messages transferred to and from a web application?
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
Syslog collecting software is installed on the server For the log containment, a disk with FAT type partition is used An engineer determined that log files are being corrupted when the 4 GB tile size is exceeded. Which action resolves the issue?
Which signature impacts network traffic by causing legitimate traffic to be blocked?
What describes the concept of data consistently and readily being accessible for legitimate users?
Refer to the exhibit.
A workstation downloads a malicious docx file from the Internet and a copy is sent to FTDv. The FTDv sends the file hash to FMC and the tile event is recorded what would have occurred with stronger data visibility.
A security engineer must protect the company from known issues that trigger adware. Recently new incident has been raised that could harm the system. Which security concepts are present in this scenario?
When communicating via TLS, the client initiates the handshake to the server and the server responds back with its certificate for identification.
Which information is available on the server certificate?
Which action matches the weaponization step of the Cyber Kill Chain model?
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which identifier tracks an active program?
An engineer is addressing a connectivity issue between two servers where the remote server is unable to establish a successful session. Initial checks show that the remote server is not receiving an SYN-ACK while establishing a session by sending the first SYN. What is causing this issue?
During which phase of the forensic process are tools and techniques used to extract information from the collected data?
What is the impact of false positive alerts on business compared to true positive?
A system administrator is ensuring that specific registry information is accurate.
Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
Which security principle requires more than one person is required to perform a critical task?
Which security model assumes an attacker within and outside of the network and enforces strict verification before connecting to any system or resource within the organization?
Refer to the exhibit. An employee received an email from an unknown sender with an attachment and reported it as a phishing attempt. An engineer uploaded the file to Cuckoo for further analysis. What should an engineer interpret from the provided Cuckoo report?
An engineer needs to discover alive hosts within the 192.168.1.0/24 range without triggering intrusive portscan alerts on the IDS device using Nmap. Which command will accomplish this goal?
Refer to the exhibit.
What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?


 A screenshot of a computer
Description automatically generated
A screenshot of a computer
Description automatically generated
