You are configuring an e-mail client to connect to your e-mail account. Which of following is required to set up the e-mail account?
Your customer scheduled a meeting to discuss a project you are managing. Early testing indicates that there are currently quality problems with some of the more complex features. The customer stated that quality and budget are his two main concerns: The project must be developed within budget and must be very high quality. When you asked the customer if he would be willing to extend the deadline to meet his objectives, he stated this was not possible. What adjustment to the project triangle components can you suggest to meet your customer’s needs?
Three hardware devices need to communicate with the CPU simultaneously. Which of the following will each device need to issue?
You are creating a style sheet to format your Web pages. For the page background color, you enter the hexadecimal code FF0000. What color will the page background be when you apply this style?
You want to enable wireless security on your Android device and your Linux system. Which of the following is a disadvantage of Wired Equivalent Privacy (WEP)?
You have recently purchased a new wireless router. You would like to configure a name for your wireless network so that you can easily identify it when scanning available wireless networks. Which term describes this wireless network device name?
You are using an e-mail client that you are unfamiliar with. You need to send an e-mail with an attachment but you do not see a feature labeled “attachment†anywhere on the client. What icon should you look for that is commonly used to invoke the e-mail attachment option?
Marcella is looking for a very unique product online. She has found one on the XYZ Company’s Web site, which is designed well and appears to be legitimate. As she navigates through the checkout process, she reaches the checkout page with this URL, which asks her to enter her credit card information:
http://XYZ.com/gp/checkout.html/ref=chk_out_TLS12B_lb?ie=IJTFB &docld=10007931
Why should Marcella cancel her online transaction instead of proceeding?
Consider the network configuration shown in the command prompt:
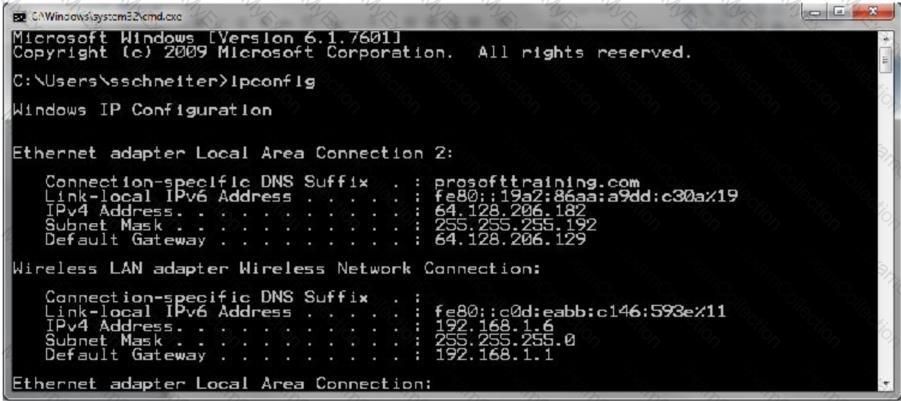
What does the Default Gateway identify?

