The Gateway Status view in SmartConsole shows the overall status of Security Gateways and Software Blades. What does the Status Attention mean?
Fill in the blanks: A ____ license requires an administrator to designate a gateway for attachment whereas a _____ license is automatically attached to a Security Gateway.
Which of the following is NOT a policy type available for each policy package?
Which SmartConsole application shows correlated logs and aggregated data to provide an overview of potential threats and attack patterns?
Rugged appliances are small appliances with ruggedized hardware and like Quantum Spark appliance they use which operating system?
Fill in the blank RADIUS Accounting gets_____data from requests generated by the accounting client
To view the policy installation history for each gateway, which tool would an administrator use?
Which Security Blade needs to be enabled in order to sanitize and remove potentially malicious content from files, before those files enter the network?
Fill in the blanks: A Security Policy is created in_____, stored in the_____ and Distributed to the various
True or False: The destination server for Security Gateway logs depends on a Security Management Server configuration.
What is required for a certificate-based VPN tunnel between two gateways with separate management systems?
In which scenario is it a valid option to transfer a license from one hardware device to another?
Fill in the blank: Permanent VPN tunnels can be set on all tunnels in the community, on all tunnels for specific gateways, or__________.
Which of the following is NOT supported by Bridge Mode Check Point Security Gateway
Which repositories are installed on the Security Management Server by SmartUpdate?
Fill in the blanks: There are ________ types of software containers ________.
You have successfully backed up your Check Point configurations without the OS information. What command would you use to restore this backup?
An administrator wishes to use Application objects in a rule in their policy but there are no Application objects listed as options to add when clicking the"+" to add new items to the "Services & Applications" column of a rule. What should be done to fix this?
A security zone is a group of one or more network interfaces from different centrally managed gateways. What is considered part of the zone?
Which option in a firewall rule would only match and allow traffic to VPN gateways for one Community in common?
Fill in the blank: In order to install a license, it must first be added to the ____________.
When configuring Spoof Tracking, which tracking actions can an administrator select to be done when spoofed packets are detected?
Fill in the blank: An Endpoint identity agent uses a ___________ for user authentication.
What Check Point tool is used to automatically update Check Point products for the Gaia OS?
Sticky Decision Function (SDF) is required to prevent which of the following? Assume you set up an Active-Active cluster.
What data MUST be supplied to the SmartConsole System Restore window to restore a backup?
In the Check Point Security Management Architecture, which component(s) can store logs?
You are the Check Point administrator for Alpha Corp with an R80 Check Point estate. You have received a call by one of the management users stating that they are unable to browse the Internet with their new tablet connected to the company Wireless. The Wireless system goes through the Check Point Gateway. How do you review the logs to see what the problem may be?
An administrator can use section titles to more easily navigate between large rule bases. Which of these statements is FALSE?
Which software blade enables Access Control policies to accept, drop, or limit web site access based on user, group, and/or machine?
Which of the following is NOT a valid configuration screen of an Access Role Object?
After the initial installation on Check Point appliance, you notice that the Management interface and default gateway are incorrect. Which commands could you use to set the IP to 192.168.80.200/24 and default gateway to 192.168.80.1.
When configuring Anti-Spoofing, which tracking options can an Administrator select?
Customer’s R80 management server needs to be upgraded to R80.10. What is the best upgrade method when the management server is not connected to the Internet?
A stateful inspection firewall works by registering connection data and compiling this information. Where is the information stored?
Fill in the blank: An identity server uses a ___________ for user authentication.
Fill in the blank: Browser-based Authentication sends users to a web page to acquire identities using ___________.
If an administrator wants to restrict access to a network resource only allowing certain users to access it, and only when they are on a specific network what is the best way to accomplish this?
Administrator Dave logs into R80 Management Server to review and makes some rule changes. He notices that there is a padlock sign next to the DNS rule in the Rule Base.
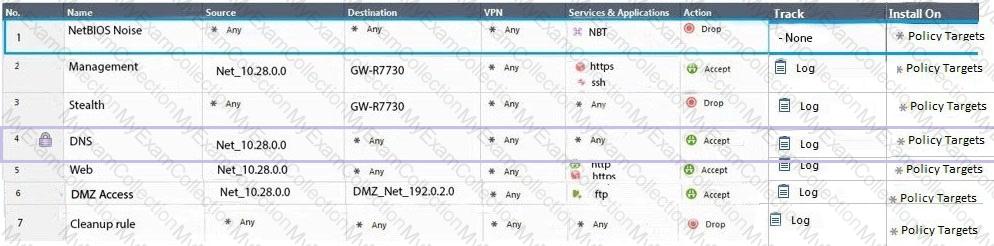
What is the possible explanation for this?
Fill in the blank: The_____is used to obtain identification and security information about network users.
Fill in the blank: Back up and restores can be accomplished through_________.
What are the Threat Prevention software components available on the Check Point Security Gateway?
When URL Filtering is set, what identifying data gets sent to the Check Point Online Web Service?
With URL Filtering, what portion of the traffic is sent to the Check Point Online Web Service for analysis?
Both major kinds of NAT support Hide and Static NAT. However, one offers more flexibility. Which statement is true?
One of major features in R80.x SmartConsole is concurrent administration. Which of the following is NOT possible considering that AdminA, AdminB, and AdminC are editing the same Security Policy?
Fill in the blank RADIUS protocol uses_____to communicate with the gateway
Tom has connected to the Management Server remotely using SmartConsole and is in the process of making some Rule Base changes, when he suddenly loses connectivity. Connectivity is restored shortly afterward. What will happen to the changes already made?
Which type of Endpoint Identity Agent includes packet tagging and computer authentication?
Is it possible to have more than one administrator connected to a Security Management Server at once?
In order to modify Security Policies, the administrator can use which of the following tools? (Choose the best answer.)
When you upload a package or license to the appropriate repository in SmartUpdate. where is the package or license stored?
You want to store the GAiA configuration in a file for later reference. What command should you use?
The SmartEvent R80 Web application for real-time event monitoring is called:
To provide updated malicious data signatures to all Threat Prevention blades, the Threat Prevention gateway does what with the data?
You have created a rule at the top of your Rule Base to permit Guest Wireless access to the Internet. However, when guest users attempt to reach the Internet, they are not seeing the splash page to accept your Terms of Service, and cannot access the Internet. How can you fix this?
What are the software components used by Autonomous Threat Prevention Profiles in R8I.20 and higher?
Which single Security Blade can be turned on to block both malicious files from being downloaded as well as block websites known to host malware?
While enabling the Identity Awareness blade the Identity Awareness wizard does not automatically detect the windows domain Why does it not detect the windows domain?
Fill in the blanks: The Application Layer Firewalls inspect traffic through the ______ layer(s) of the TCP/IP model and up to and including the ______ layer.
Which of the following is NOT supported by Bridge Mode on the Check Point Security Gateway?
There are four policy types available for each policy package. What are those policy types?
When defining group-based access in an LDAP environment with Identity Awareness, what is the BEST object type to represent an LDAP group in a Security Policy?
Can multiple administrators connect to a Security Management Server at the same time?
An administrator wishes to enable Identity Awareness on the Check Point firewalls. However they allow users to use company issued or personal laptops. Since the administrator cannot manage the personal laptops, which of the following methods would BEST suit this company?
Which of the following is used to initially create trust between a Gateway and Security Management Server?
Access roles allow the firewall administrator to configure network access according to:
AdminA and AdminB are both logged in on SmartConsole What does it mean if AdmmB sees a lock icon on a rule? Choose the BEST answer.
True or False: In a Distributed Environment, a Central License can be installed via CLI on a Security Gateway
When a Security Gateway sends its logs to an IP address other than its own, which deployment option is installed?
Fill in the blank: SmartConsole, SmartEvent GUI client, and ___________ allow viewing of billions of consolidated logs and shows them as prioritized security events.
Fill in the blank: In Security Gateways R75 and above, SIC uses ______________ for encryption.
John is the administrator of a R80 Security Management server managing r R77.30 Check Point Security Gateway. John is currently updating the network objects and amending the rules using SmartConsole. To make John’s changes available to other administrators, and to save the database before installing a policy, what must John do?
Fill in the blank: The _____ feature allows administrators to share a policy with other policy packages.
Of all the Check Point components in your network, which one changes most often and should be backed up most frequently?
Choose what BEST describes the reason why querying logs now are very fast.
In HTTPS Inspection policy, what actions are available in the "Actions" column of a rule?

