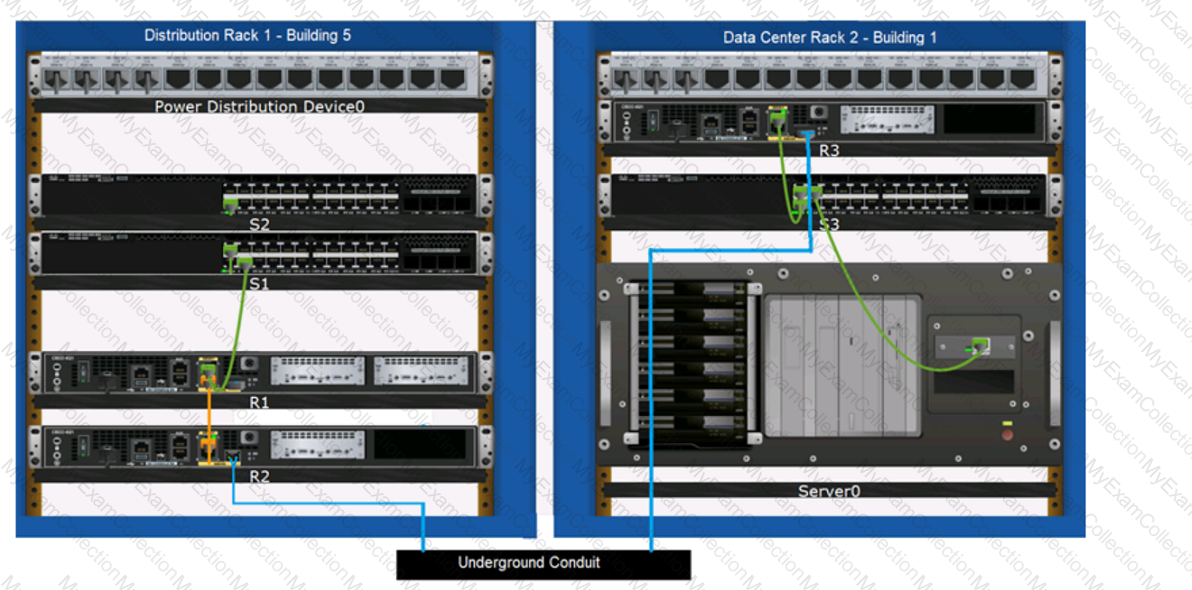
You want to store files that will be accessible by every user on your network.
Which endpoint device do you need?
Which component of the AAA service security model provides identity verification?
A user reports that a company website is not available. The help desk technician issues a tracert command to determine if the server hosting the website is reachable over the network. The output of the command is shown as follows:
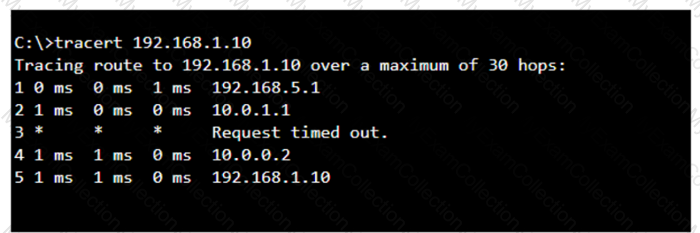
What can you tell from the command output?
Which two pieces of information should you include when you initially create a support ticket? (Choose 2.)
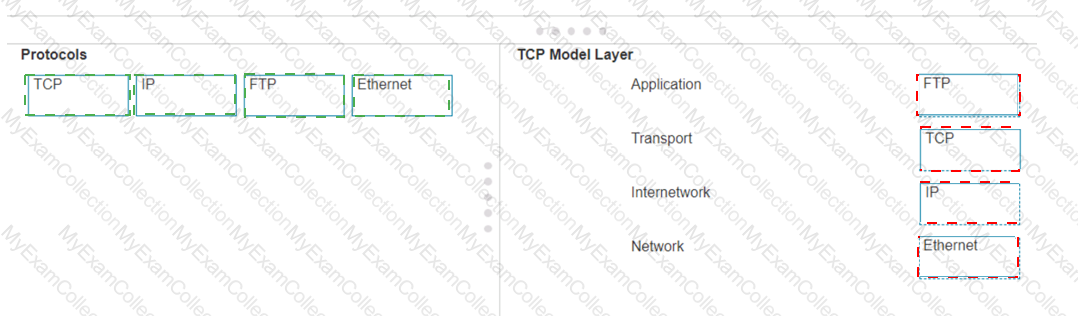
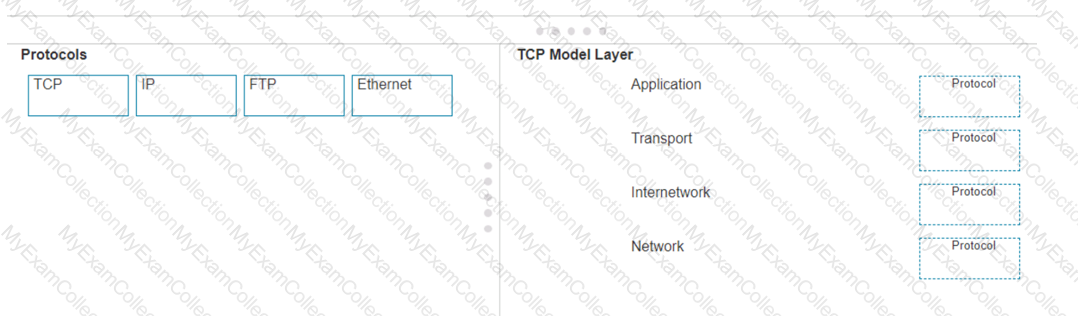
Move each protocol from the list on the left to the correct TCP/IP model layer on the right.
Note: You will receive partial credit for each correct match.
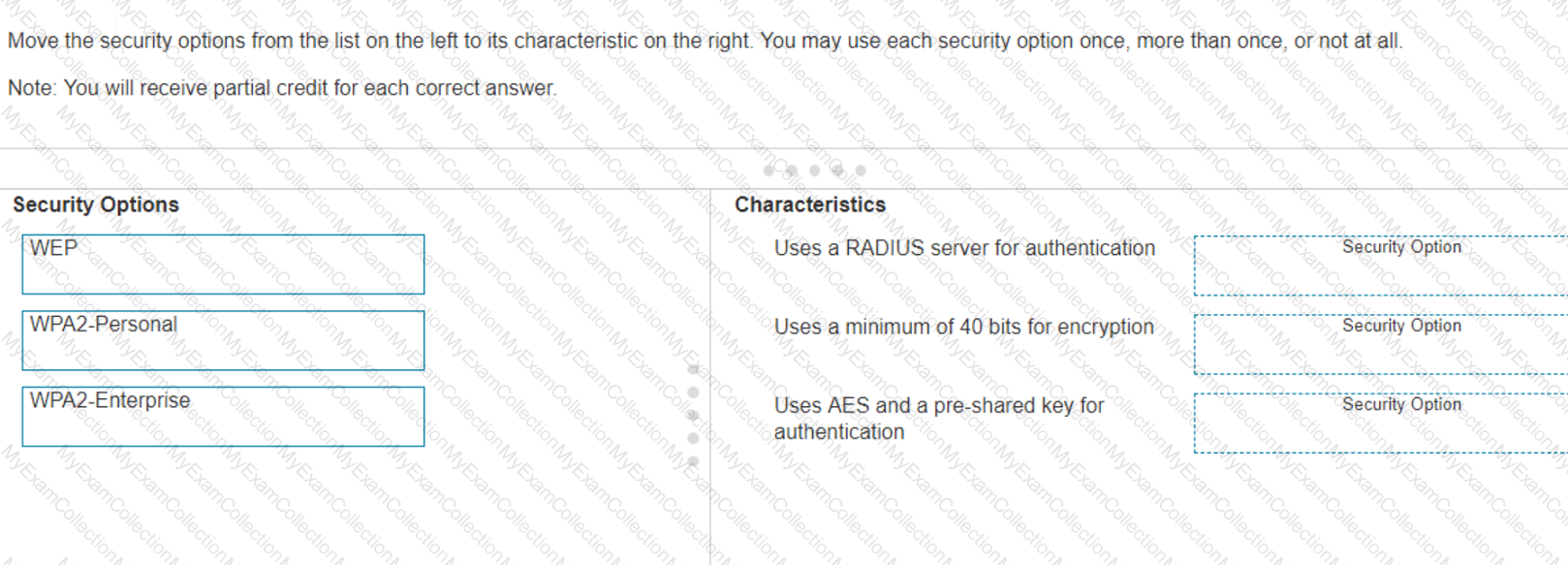
Move the security options from the list on the left to its characteristic on the right. You may use each security option once, more than once, or not at all.
Note: You will receive partial credit for each correct answer.
A host is given the IP address 172.16.100.25 and the subnet mask 255.255.252.0.
What is the CIDR notation for this address?
What is the most compressed valid format of the IPv6 address 2001 :0db8:0000:0016:0000:001b: 2000:0056?
Examine the connections shown in the following image. Move the cable types on the right to the appropriate connection description on the left. You may
use each cable type more than once or not at all.