A website is using source address persistence with a 30 second timeout A client is idle for 35 seconds
What happens to their connection?
A BIG-IP Administrator has a cluster of devices.
What should the administrator do after creating a new Virtual Server on device 1?
Which TransportLayer Security (TLS) extension can be used to enable a single virtual server to serve multiple HTTPS websites in different can be used to enable a single virtual server to server domains?
The use of attack signature within an intrusion Detection System (IDS) is an application of which security model?
An administrator points the browser at h.tp://www mydomain com.The destination server listens on TCP port 8080 Which feature must be enabled on the virtual server for this configuration to work?
Tl SISSL prides which functionary when a web browser connects to web site using the HTTPS protocol?
An administrator configures a custom MAC masquerade address on a redundant BIG-IP system
What will be the result?
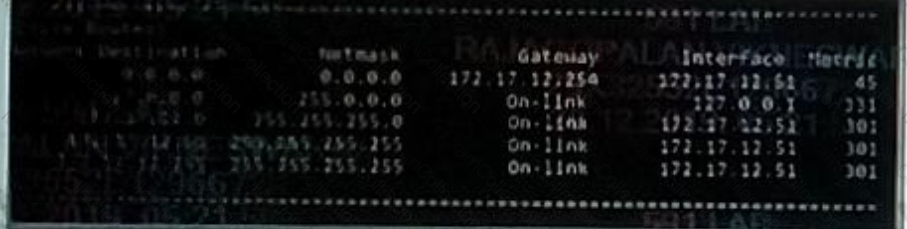
The BIG-IP device has the following configured routes:
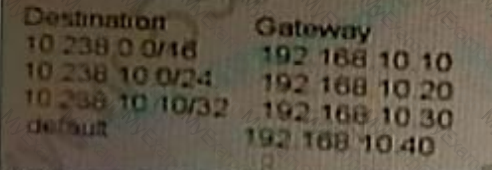
Which gateway will be chosen to send the packet to the destination 10 238 10 11?
Which support service is required to synchrony the time stamps in system logs from these devices?
An administrator needs to lower .he amount of new TCP connections to help with network congest?
How should the administrator accomplish this?
In the Network Map a red diamond appears next to the three member servers in the Virtual Server’s pool. The nodes in the pool each show a green circle. What is the most likely reason for this scenario?
In an administrator's environment, the administrator wants to inspect a high volume of SSL traffic
What should be used for this task?
What describes the third ‘’A’’ in the common authentication acronym AAA?
Given the service list of a server shown, the administrator needs to determine why users are unable to resolve the IP addresswww.example.com .
What is the causing this issue?
End users report widespread issues accessing multiple network resources
What tool should the BIG IP Administrator use to view the status of all virtual servers and associated resources in one place?
An Administrator enables HTTP keep alive.
How does this affect the network?
An administrator needs to protect a web application from cross-site scripting (CSS) exploits. Which F5 protocol provide this functionality

An administrator sets up a web server for a new web application. The administrator cannot access the web server at is causing this issue?
An IPv4 client tries to access to http://www myserver com
Which type of DNS request should the client send to its configured DNS server?
An administrator suspects that a BIG IP appliance is experiencing performing issue due to spikes in CPU usage checks the performance issues does to spikes in CPU usage checks the performance report in the BIG-IP UI on CPU spikes are evident in the graphs. Which section in the BIG IP UI can the administrator check to troubleshoot the issue further?
A BIG IP Administrator need to perform a packet capture and identify the source IP that is connecting to the Virtual Server.
Which utility should the administrator use on the BIG IP device?
A client needs to learn if a web server supports POST
Which HTTP method is used?
What should a BIG-IP Administrator configure to minimize impact during a failure?
Which security mode. functions by defining what traffic is allowed and rejecting all other traffic?
The administrator wants client request to be directed to the same pool member through the session based on the client IP address.
Which persistence method should the administrator choose?